A new phishing campaign called “Beyond the Grave” targeted international hedge funds on January 9th, 2019. In a statement posted to BleepingComputer, the attackers have stated that they will continue to target banking and financial institutions in the future.
A member named XanderBauer has created a post in the BleepingComputer forums with a title of “Beyond The Grave Virus infecting Hedge Funds”. This post states that their phishing campaign is designed to alter data confidentiality in the targeted hedge funds, but it is not clear if that is to be used for the attackers financial advantage or to cause market instability for political reasons.
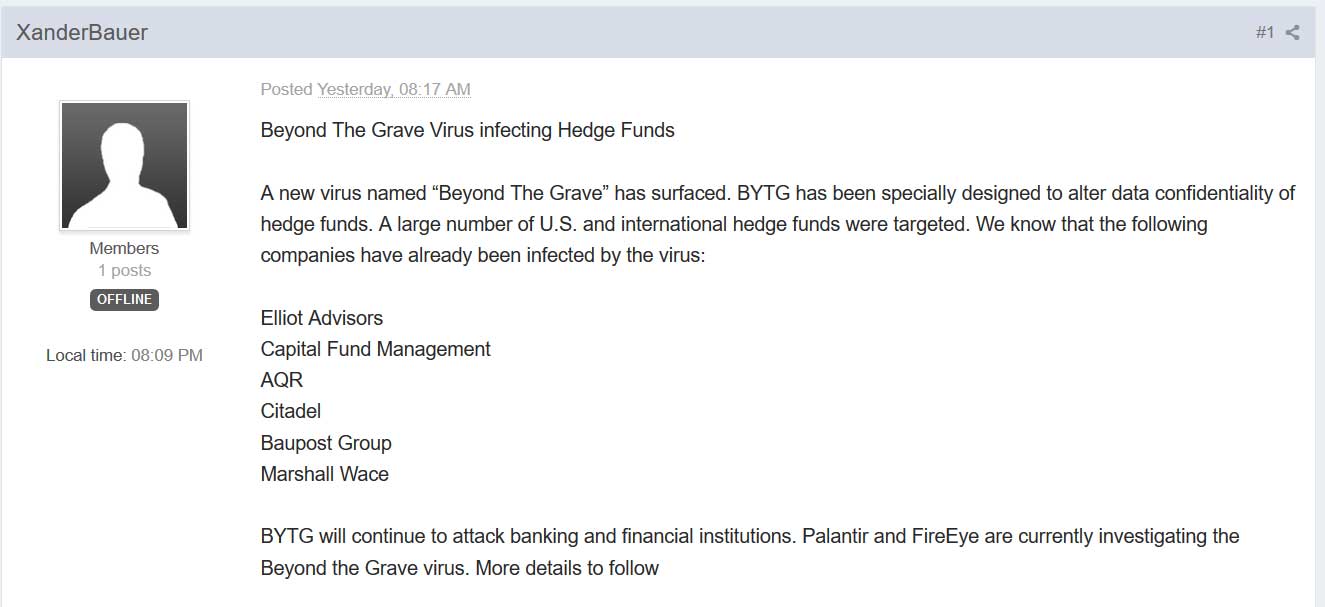
The full text of the post is as follows.
Beyond The Grave Virus infecting Hedge Funds
A new virus named “Beyond The Grave” has surfaced. BYTG has been specially designed to alter data confidentiality of hedge funds. A large number of U.S. and international hedge funds were targeted. We know that the following companies have already been infected by the virus:
Elliot Advisors
Capital Fund Management
AQR
Citadel
Baupost Group
Marshall Wace
BYTG will continue to attack banking and financial institutions. Palantir and FireEye are currently investigating the Beyond the Grave virus. More details to followWhile the above statement only lists six hedge funds/financial firms, the images shared by the attacker indicate that they are also targeting Alliance Bernstein, which according to their fourth quarter 2018 review has an AMU (assets under management) of $516.4 billion USD.
Included in the posting to our forums is a link to an imgur.com gallery of images that showcases the attackers phishing campaign. In the image below we can see a phishing campaign being conducted and sending out emails to AQR, Citadel, Bernstein, and Capital Fund Management.
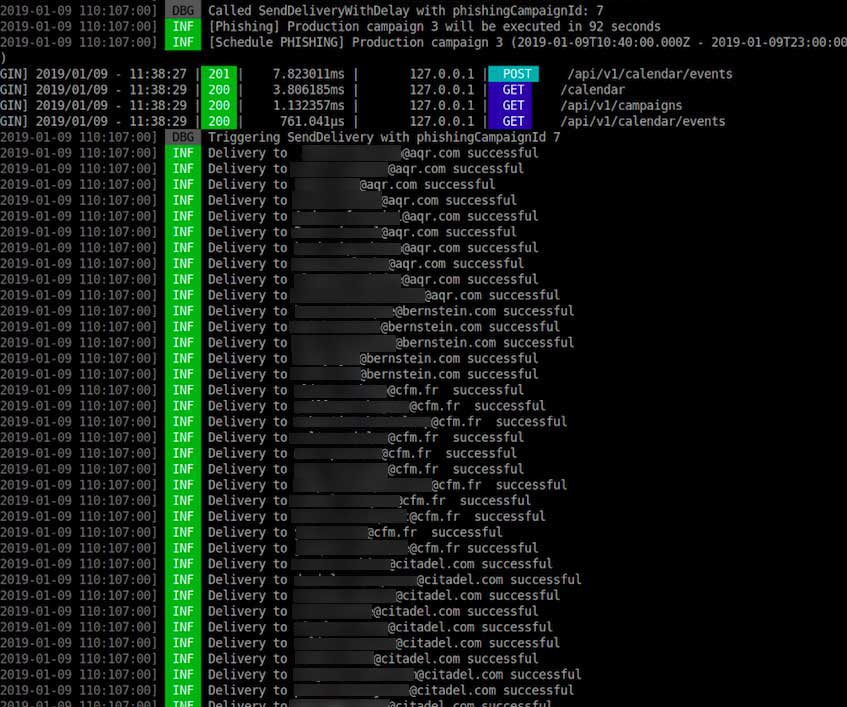
Also included as proof is a sample of the phishing campaign email with a open windows showing the command that executed the phishing kit.
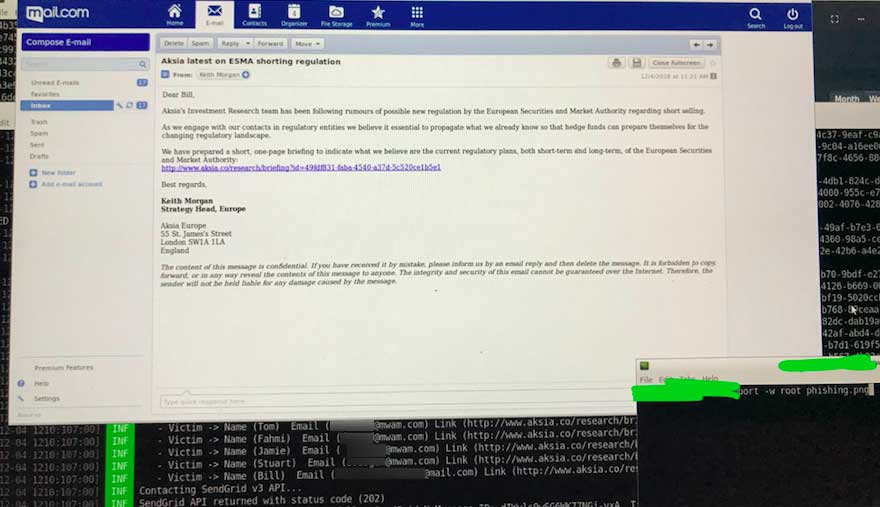
These phishing emails impersonate a legitimate financial research company named Aksia and pretend to be research regarding rumors related to ESMA (European Securities and Markets Authority) halting short selling during Brexit.
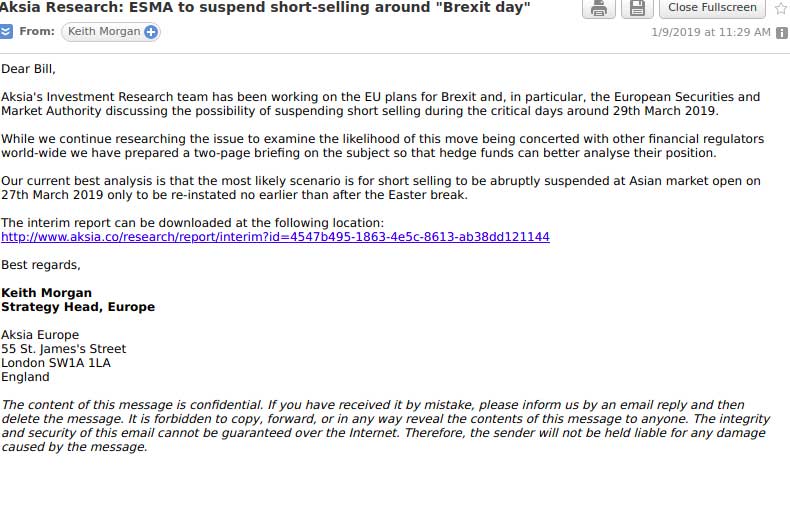
These phishing emails contain links to the alleged research located at the www.aksia.co site, which attempts to impersonate the real Aksia.com site.
http://aksia[.]co/research/report/interim?id=4547b495-1863-4e5c-8613-ab38dd121144
http://www[.]aksia[.]co/research/briefing?id=457ba3d6-b69b-4bc4-ad5d-67ebc816682aWhen visiting these URLs, nothing appears but a blank page. It is not known if the payload has been taken down or if this is being done intentionally to trick the victims into further communicating further with the attackers.
The attacker posted an image that illustrated how at least one of the recipients has fallen for this attack as the victim responded to the attacker asking for more information as “the link does not work.”
While the motive behind the attack is
This is why it is very important for all email users to always check the legitimacy of an url before clicking on it. This can be done by simply going to the root of the URL, which in this case is https://www.aksia.co, and they would have seen a blank page, which should be suspicious. Also doing a search for Aksia would have revealed a different domain than the one in the email.
BleepingComputer has contacted all of the companies targeted by this phishing campaign, Aksia, Palantir, FireEye, and the attacker who posted the information, but have only heard back from Marshall Wace at this time.
A Marshall Wace spokesman stated:
“We are aware that Marshall Wace, alongside other asset managers, was recently targeted by a phishing campaign, but the potential intrusion was picked up by our cyber security systems and we are confident there was no breach of our environment. We remain vigilant.”
To read the original article:



