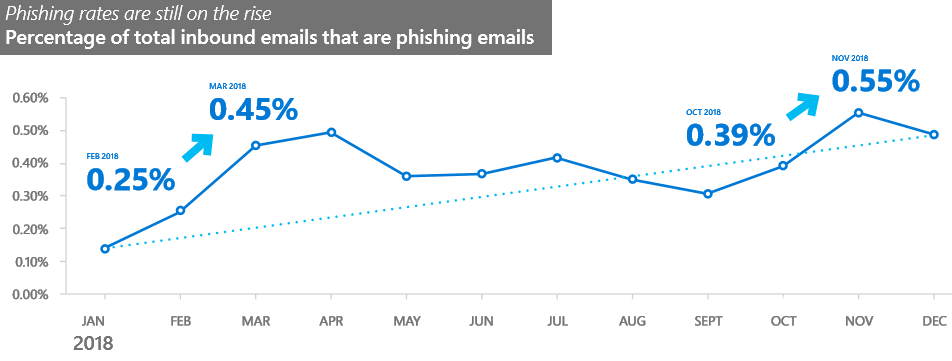
Phishing attacks have seen an impressive 250% increase between January and December 2018, with attackers moving to multiple points of attacks during the same campaign, switching between URLs, domains, and servers when sending e-mails and hosting phishing forms.
Threat actors have also begun to diversify the infrastructure they use to run phishing campaigns, with Microsoft observing as part of its Security Intelligence Report (SIR) Volume 24 that hosted servers and public cloud tools were adopted to make it easier to camouflage as legitimate services or products.
To be more exact, collaboration sites and document sharing services have been used by bad actors to host both fake login forms and malicious payloads distributed trough malspam campaigns.
As a side note, Microsoft saw “an increase in the use of compromised accounts to further distribute malicious emails both inside and outside an organization.”
Phishing attacks on the rise throughout 2018
Phishing also remained the favorite attack method employed by crooks as part of multi-stage malware attacks designed to drop a large variety of malware families on their victims’ computers.
Throughout 2018, Redmond’s team scanned and analyzed more than 470 billion email messages sent and received by its Office 365 customers for phishing and malware, providing a bird’s eye look over the evolution of the phishing methods and trends.
As discovered by Microsoft during their yearly analysis of phishing trends, attackers have used a wide array of malware payloads and lures designed to snatch their victims’ data:
• Domain spoofing (email message domain is an exact match with the original domain)
• Domain impersonation (the email domain is a look-alike of the original domain)
• User impersonation (the email appears to come from someone you trust)
• Text lures (the text message appears to come from a legitimate source and asks the victim to provide sensitive info)
• Credential phishing links (the email contains a link to a page that resembles a login page for a legitimate site)
• Phishing attachments (the email contains a malicious file attachment that the sender entices the victim to open)
• Links to fake cloud storage locations (the email appears to come from a legitimate source and entices the user to give permission and/or enter personal info for accessing a fake cloud storage location)Ransomware and cryptojacking on a downward spiral
On the other hand, cryptojacking, ransomware, and malware encounters have all been on a downward trend during 2018, malware encounters going down in numbers roughly 34% based on stats gathered after collecting and analyzing “6 5 trillion threat signals that go through the Microsoft cloud every day.”
2018 was the year when threat actors made the switch from high maintenance ransomware campaigns to very lucrative and low effort cryptojacking campaigns that led to ever-increasing profits.
“This approach allows them to leverage the processing power of hundreds of thousands of computers instead of one or two Even when a minor infection is discovered, the anonymous nature of cryptocurrency complicates efforts to track down the responsible parties,” says Microsoft’s SIR team.
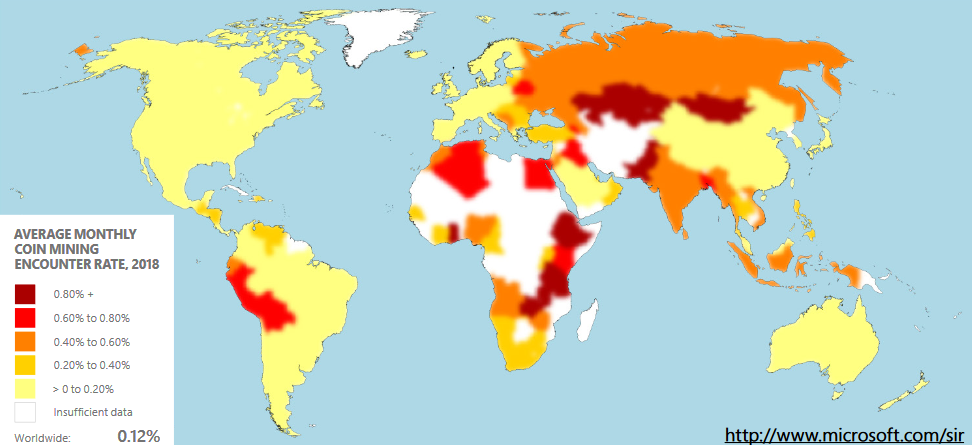
Out of all countries monitored for illicit cryptocurrency mining, the lowest coin mining encounter rates during 2018 were found in Ireland, Japan, the United States, and China with an average monthly coin mining encounter rate of roughly 0.02%.
According to reports, roughly 5% of all Monero cryptocurrency currently in circulation was mined using malware and, right after the start of 2018, miscreants have started spreading cryptominers on compromised machines instead of ransomware, as part of huge campaigns targeting a multitude of vulnerabilities in software products.
However, in the end, cryptocurrency mining encounters also matched the ransomware downward trend seeing a 36% drop between January and December 2018 after the drop in value experienced by cryptocurrencies towards the end of the year.
To read the original article:
https://www.bleepingcomputer.com/news/security/microsoft-sees-250-percent-phishing-increase-malware-decline-by-34-percent/



