EXECUTIVE SUMMARY
Point-of-sale malware is popular among attackers, as it usually leads to them obtaining credit card numbers and immediately use that information for financial gain. This type of malware is generally deployed on retailers’ websites and retail point-of-sale locations with the goal of tracking customers’ payment information. If they successfully obtain credit card details, they can use either the proceeds from the sale of that information or use the credit card data directly to obtain additional exploits and resources for other malware. Point-of-sale terminals are often forgotten about in terms of segregation and can represent a soft target for attackers. Cisco Talos recently discovered a new PoS malware that the attackers are selling on a crimeware forum. Our researchers also discovered the associated payloads with the malware, its infrastructure and control panel. We assess with high confidence that this is not the first malware developed by this actor. A few years ago, they were also pushing the DiamondFox L!NK botnet. Known as “GlitchPOS,” this malware is also being distributed on alternative websites at a higher price than the original.
The actor behind this malware created a video, which we embedded below, showing how easy it is to use it. This is a case where the average user could purchase all the tools necessary to set up their own credit card-skimming botnet.
GLITCHPOS
Packer overview
A packer developed in VisualBasic protects this malware. It’s, on the surface, a fake game. The user interface of the main form (which is not displayed at the execution) contains various pictures of cats:
The purpose of the packer is to decode a library that’s the real payload encoded with the UPX packer. Once decoded, we gain access to GlitchPOS, a memory grabber developed in VisualBasic.
Payload analysis
The payload is small and contains only a few functions. It can connect to a command and control (C2) server to:
- Register the infected systems
- Receive tasks (command execution in memory or on disk)
- Exfiltrate credit card numbers from the memory of the infected system
- Update the exclusion list of scanned processes
- Update the “encryption” key
- Update the User Agent
- Clean itself
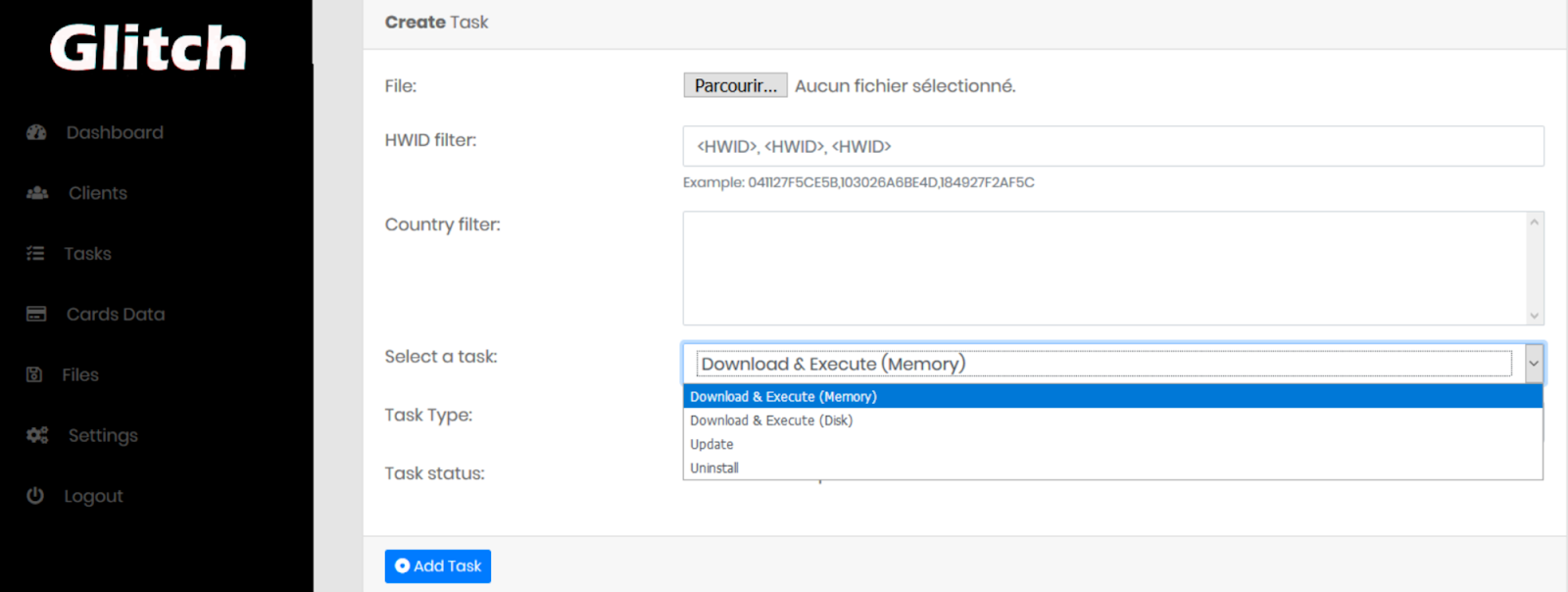
TASKS MECHANISM
The malware receives tasks from the C2 server. Here is the task pane:
The commands are executed via a shellcode directly sent by the C2 server. Here is an example in Wireshark:
The shellcode is encoded with base64. In our screenshot, the shellcode is a RunPE:
“ENCRYPTION” KEY
The “encryption” key of the communication can be updated in the panel. The communication is not encrypted but simply XORed:
CREDIT CARD GRABBER
The main purpose of this malware is to steal credit card numbers (Track1 and Track2) from the memory of the infected system. GlitchPOS uses a regular expression to perform this task:
- (%B)\d{0,19}\^[\w\s\/]{2,26}\^\d{7}\w*\?
The purpose of this regular expression is to detect Track 1 format B
Here is an example of Track 1:
Cardholder : M. TALOS
Card number*: 1234 5678 9012 3445
Expiration: 01/99
%B1234567890123445^TALOS/M.
- ;\d{13,19}=\d{7}\w*\?
The purpose of this regular expression is to detect Track 2
Here is an example of Track 2 based on the previous example:
;1234567890123445=99011200XXXX00000000?*
If a match is identified in memory, the result is sent to the C2 server. The malware maintains an exclusion list provided by the server. Here is the default list: chrome, firefox, iexplore, svchost, smss, csrss, wininit, steam, devenv, thunderbird, skype, pidgin, services, dwn, dllhost, jusched, jucheck, lsass, winlogon, alg, wscntfy, taskmgr, taskhost, spoolsv, qml, akw.
Panel
Here are some additional screenshots of the GlitchPOS panel. These screenshots were provided by the seller to promote the malware.
The “Dashboard:”
The “Clients” list:
The “Cards Date:”
LINKED WITH DIAMONDFOX L!NK BOTNET
Author: Edbitss
The first mention of GlitchPOS was on Feb. 2, 2019 on a malware forum:
Edbitss is allegedly the developer of the DiamondFox L!NK botnet in 2015/2016 and 2017 as explained in a report by CheckPoint.
The developer created this video to promote GlitchPOS, as well. In this video, you can see the author set up the malware and capture the data from a swiped card. We apologize for the quality, shakiness, music, and generally anything else with this video, again, it’s not ours.
The built malware is sold for $250, the builder $600 and finally, the gate address change is charged at $80.
Panel similarities
In addition to the malware language (VisualBasic), we identified similarities between the DiamondFox panel and the GlitchPOS panel. In this section, the DiamondPOS screenshots come from the CheckPoint report mentioned previously.
Both dashboards’ world map are similar (image, code and color):
The author used the same terminology such ask “Clients” or “Tasks” on the left menu:
The icons are the same too in both panels, as well as the infected machine list (starting with the HWID). The PHP file naming convention is similar to DiamondFox, too.
The author clearly reused code from DiamondFox panel on the GlitchPOS panel.
Comparison of GlitchPOS and the DiamondFox POS module
In 2017, the DiamondFox malware included a POS plugin. We decided to check if this module was the same as GlitchPOS, but it is not. For DiamondFox, the author decided to use the leaked code of BlackPOS to build the credit card grabber. On GlitchPOS, the author developed its own code to perform this task and did not use the previously leaked code.
BAD GUYS ARE EVERYWHERE
It’s interesting to see that someone else attempted to push the same malware 25 days after edbitss on an alternative forum:
This attacker even tried to cash in by increasing some prices.
Some members even attempted to call out the unscrupulous behaviour:
With the different information we have, we think that Chameleon101 has taken the previous malware created by Edbitss to sell it on an alternative forum and with a higher price.
CONCLUSION
This investigation shows us that POS malware is still attractive and some people are still working on the development of this family of malware. We can see that edbitss developed malware years even after being publicly mentioned by cybersecurity companies. He left DiamondFox to switch on a new project targeting point-of-sale. The sale opened a few weeks ago, so we don’t know yet how many people bought it or use it. We also see that bad guys steal the work of each other and try to sell malware developed by other developers at a higher price. The final word will be a quote from Edbitss on a DiamondFox screenshot published by himself “In the future, even bank robbers will be replaced.”
To read the original article:
https://blog.talosintelligence.com/2019/03/glitchpos-new-pos-malware-for-sale.html