A new Ransomware-as-a-Service called Yatron is being promoted on Twitter that plans on using the EternalBlue and DoublePulsar exploits to spread to other computer on a network. This ransomware will also attempt to delete encrypted files if a payment has not been made in 72 hours.
BleepingComputer was first notified about the Yatron RaaS by a security researcher who goes by the name A Shadow. Since then, the actor behind this ransomware has strangely been promoting the service by tweeting to various ransomware and security researchers as shown below.
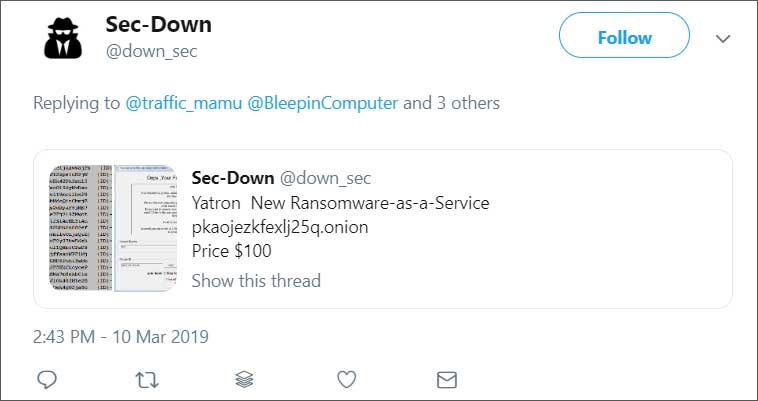
After seeing one of these tweets, BleepingComputer was able to find a sample on VirusTotal and with the help of Michael Gillespie, we started to examine the source code of the ransomware.
Like any other ransomware, when executed it will scan the computer for targeted files and encrypt them. When encrypting a file, it will append the .Yatron extension to an encrypted file’s name as shown below.
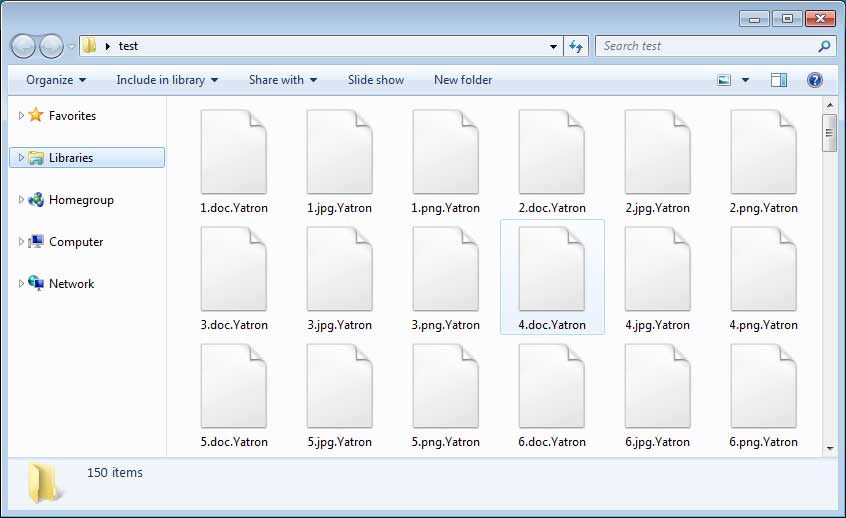
After it has finished encrypting files, it will send the encryption password and unique ID back to the ransomware’s command and control server. According to Gillespie, this ransomware is based off of HiddenTear, but its encryption algorithm has been modified so that it cannot be decrypted using current methods.
Once the encryption is done, things begin to get more interesting.
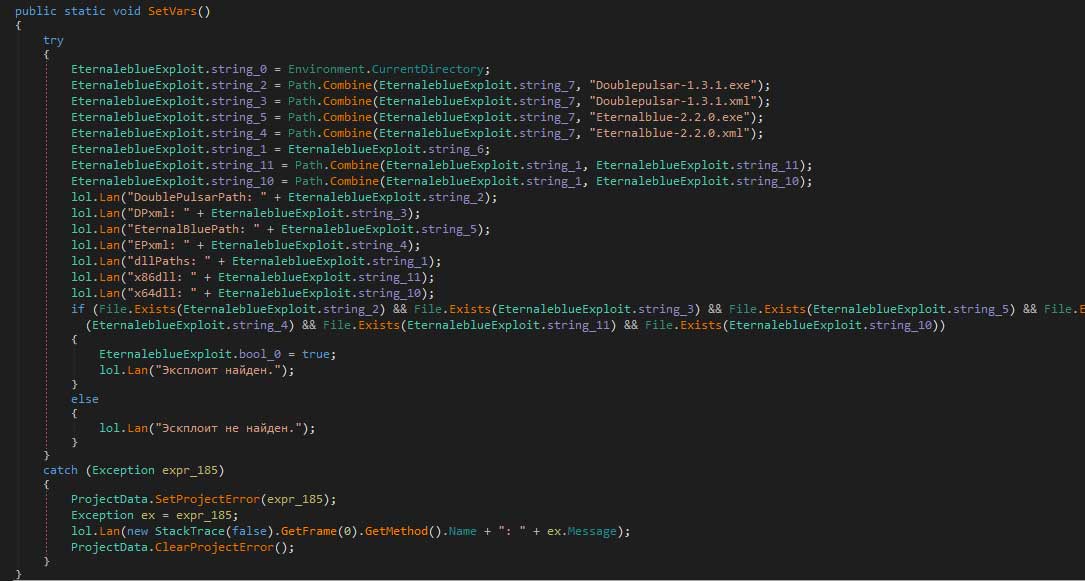
Yatron contains code to utilize the EternalBlue and DoublePulsar exploits to spread to Windows machines on the same network using SMBv1 vulnerabilities that should have been patched a long time ago. Thankfully, the code to utilize these exploits is incomplete and the ransomware does not currently include the Eternalblue-2.2.0.exe and Doublepulsar-1.3.1.exe executables that it relies on.
You can see, though, some of the code that attempts to configure variables that will be used to execute the exploit commands in the screenshot below..
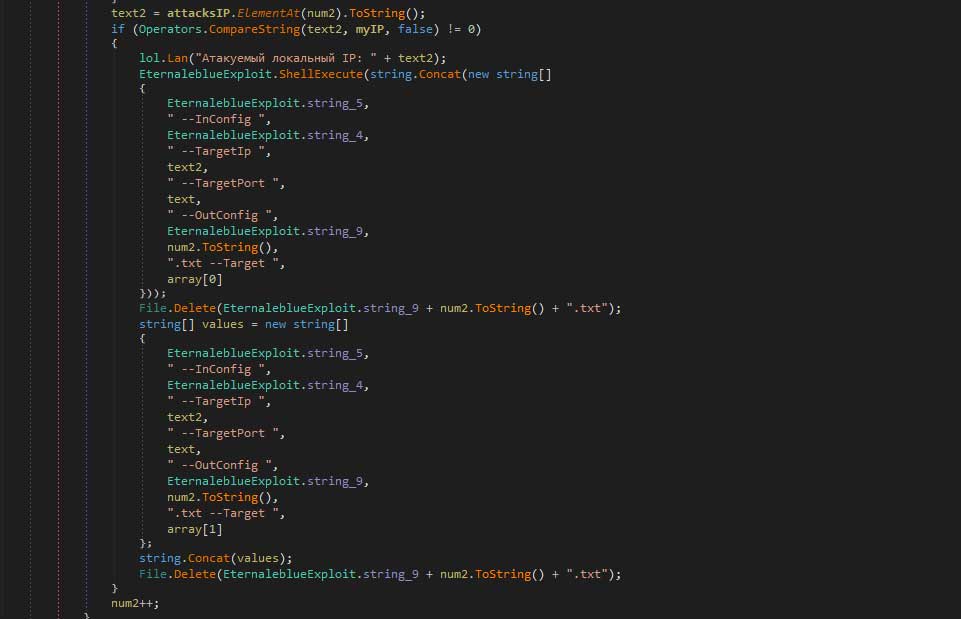
The next screenshot is the ransomware trying to trigger these exploits if the required executables existed on the computer.
In addition to exploiting vulnerabilities, Yatron will attempt to spread via P2P programs by copying the ransomware executable to default folders used by programs like Kazaa, Ares, eMule, and more. The goal is that when these programs are started, the ransomware will automatically be shared by the P2P client.
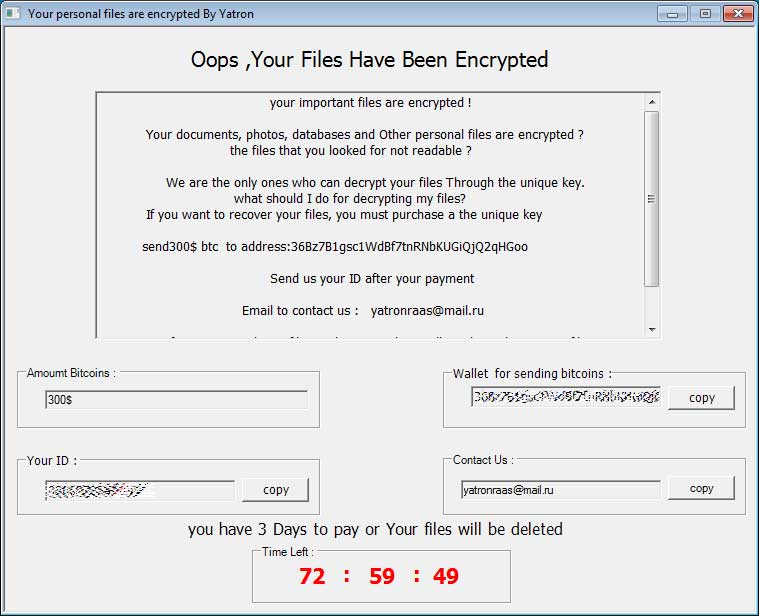
When finished, the ransomware will display an interface that contains a 72 hour countdown until the encrypted files are deleted. To protect files from being deleted, a user can simply terminate the ransom process using a tool like Process Explorer running as an Administrator.
As the sample we analyzed may not be the most up-to-date, some of the above features may have changed or become fully functional. If we find a newer sample, we will update the article as needed.
Promoted as a RaaS
Yatron is promoted as a Ransomware-as-a-Service, but does things a bit differently than most RaaS services.
Typically, when wannabe criminals join a RaaS, the developer takes a revenue share of all submitted ransom payments. For example, some RaaS services will take 20% of all ransom payments, while the affiliate/distributor earns the remaining 80%.
Like another recent RaaS called Jokeroo, the developer of Yatron is selling access to the RaaS for $100 in bitcoins and then there is no fee going forward. This new model is being used as most RaaS services do not earn any money and by having affiliates buy into it, the ransomware developers earn some revenue up front.
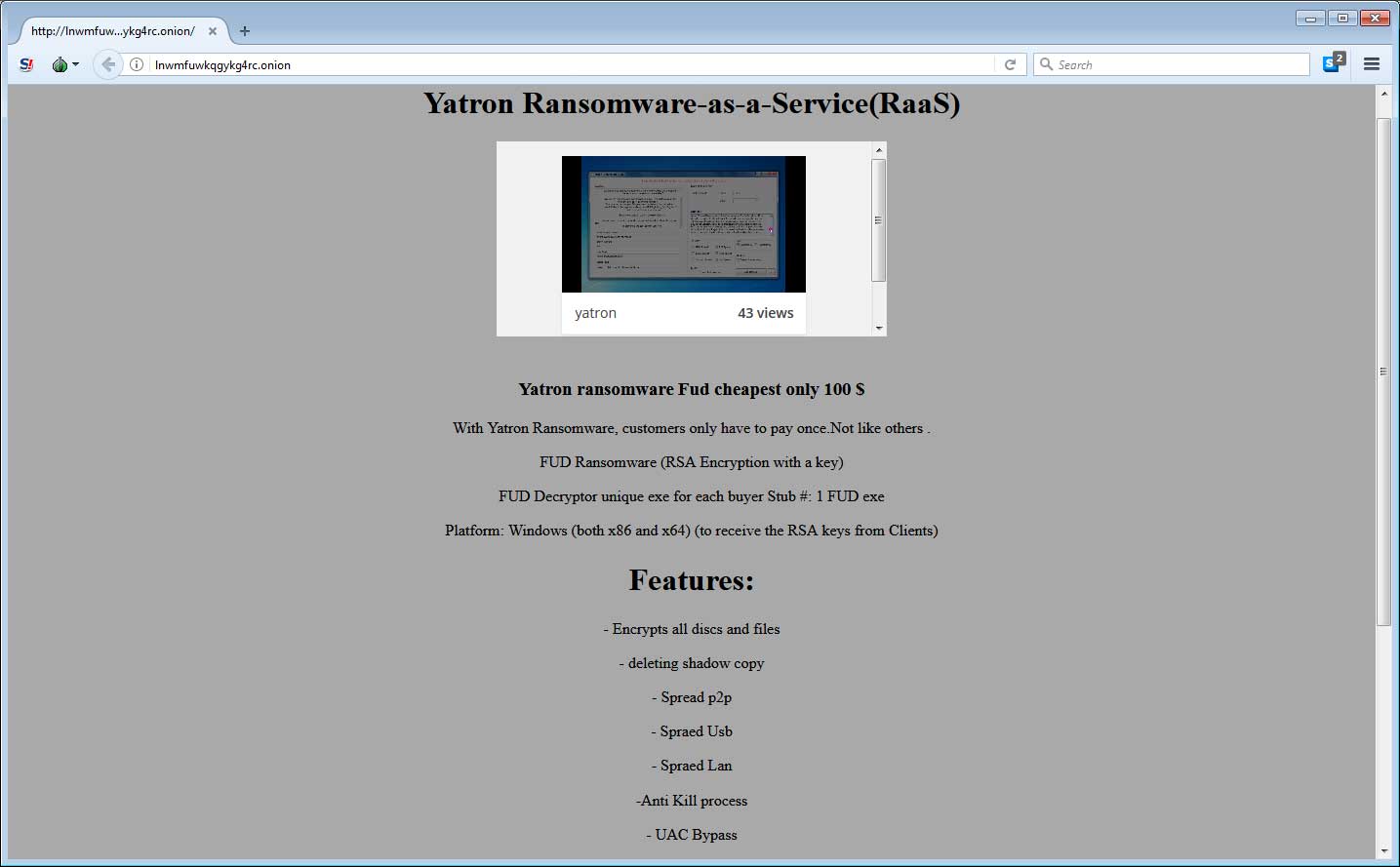
Like all RaaS offerings, Yatron promises a FUD executable, the ability to encrypt a computer, and the deletion of shadow copies. As described earlier in the article, this ransomware also aims to be able to spread via P2P, USB, and LAN.
At the time of this writing, no one has paid to gain access to this ransomware.
To read the original article:



