A Point-of-Sale (POS) malware which uses a domain generation algorithm to create command-and-control domains on the fly was deployed in attacks against small and medium-sized businesses during the last past four years—since at least 2016—according to a team of security researchers from Flashpoint.
The Flashpoint team believes that the malware they dubbed DMSniff “could be gaining an initial foothold on devices either by using brute-force attacks against SSH connections or by scanning for vulnerabilities and exploiting those.”
Additionally, while POS malware is not that uncommon having been observed in the wild multiple times throughout the years [1, 2, 3, 4], the researchers state in their in-depth analysis that DMSniff’s usage of a domain generation algorithm (DGA) to generate command-and-control domains on the spot unquestionably sets it apart from other similar malware.
“This technique is valuable to an attacker because if domains are taken down by law enforcement, technology companies, or hosting providers, the malware can still communicate and receive commands or share stolen data,” said the researchers.
Also, DMSniff will automatically rotate between multiple top-level domains (TLDs) until it manages to find a live command-and-control server (C&C).
The malware which was used since 2016 in attacks designed with credit card data theft as the final goal, uses at least 11 variants of the DGA algorithm which hints at the bad actors having deployed at least 11 different versions of the malware during the last four years.
To steal credit card data from the POS units it manages to infect, DMSniff will continuously go through the list of processes and, when it finds one that looks interesting, it will parse through the terminal’s memory looking for a credit card number.
When it finally manages to pinpoint and lift some card info from the terminal’s memory, the malware will pack it together with “some of the surrounding memory,” archive it, and send it as a package to the C&C server.
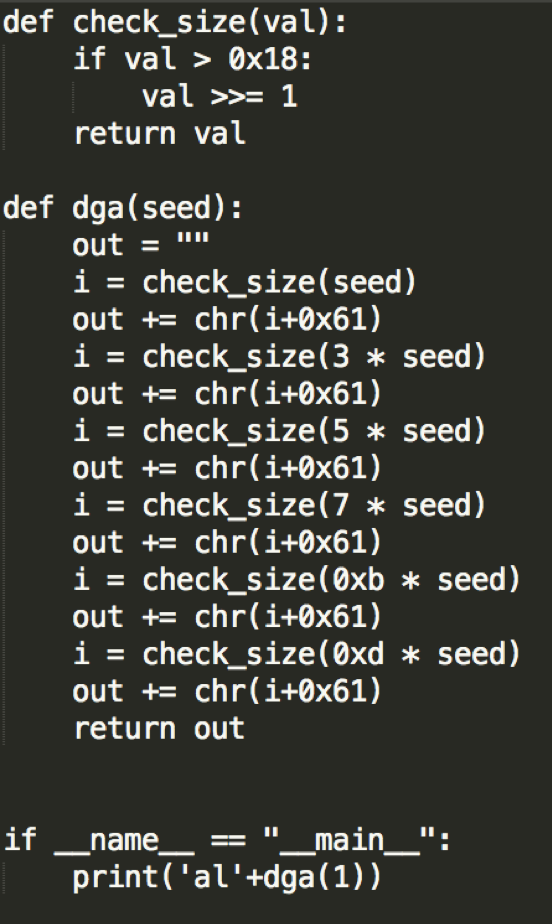
DMSniff also uses a simple string-encoding technique to hide its strings, attempting to protect itself and its C&C communication from analysis when discovered by security researchers and law enforcement.
“This shields the malware’s capabilities from detection, making it difficult for researchers to learn its capabilities,” said the Flashpoint researchers.
During their analysis, the research team “found that this malware was primarily utilized to target small to medium-sized businesses such as restaurants and theaters,” as well as other entertainment businesses which use point-of-sale terminals, the second most-targeted network asset behind database servers according to last year’s Verizon Data Breach Investigations Report.
The Flashpoint research team also provides extensive lists of indicators of compromise (IOCs) and decoded strings for the DMSniff point-of-sale malware.
To read the original article:



