Over the past five months, the London Blue cybercriminal group has been running business email compromise (BEC) scams against employees in Asia working for companies based mostly in the United States, Australia or Europe.
The corporate fraudsters rely on a new database of about 8,500 financial executives from close to 7,800 different companies in the world (most of them in the U.S.). This is almost six times smaller than the previous collection of targets, which contained details of over 50,000 financial execs.
A new report from email security company Agari on Thursday details the methodology adopted by London Blue scammers, such as focusing their attacks on targets in Asia and spoofing domains to make emails look less suspicious.
The U.S. is still the main region at the receiving end of the attacks (39%), but Hong Kong now takes second place (11%) followed by Australia (10%) and Singapore (9%). Malaysia comes fourth and then European countries.
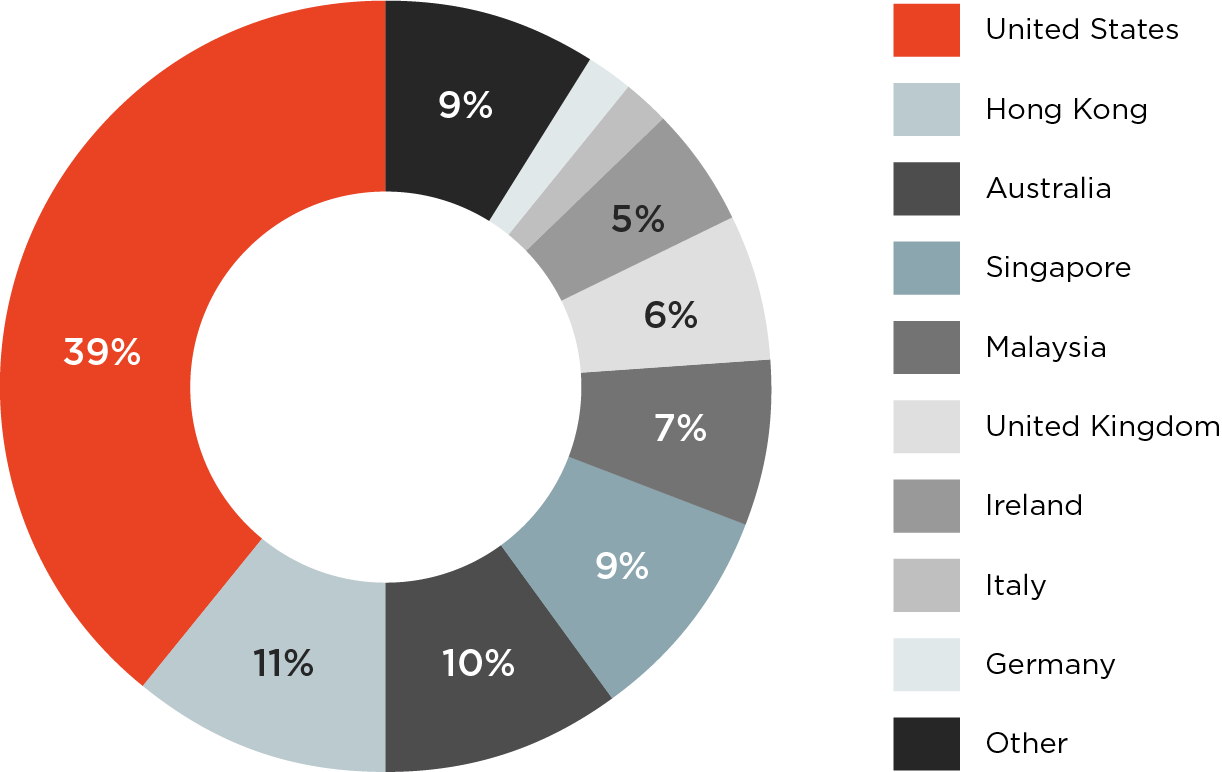
“In February, London Blue collected contact information for and launched BEC campaigns against targets in Hong Kong and Singapore. In March, the group targeted employees located in Malaysia with BEC attacks,” states the report.
On the same month, the BEC scammers improved tactics by spoofing the email address of the target company’s CEO. Previously, they used free and temporary email accounts with a fake name on display; they employed this tactic since 2016.
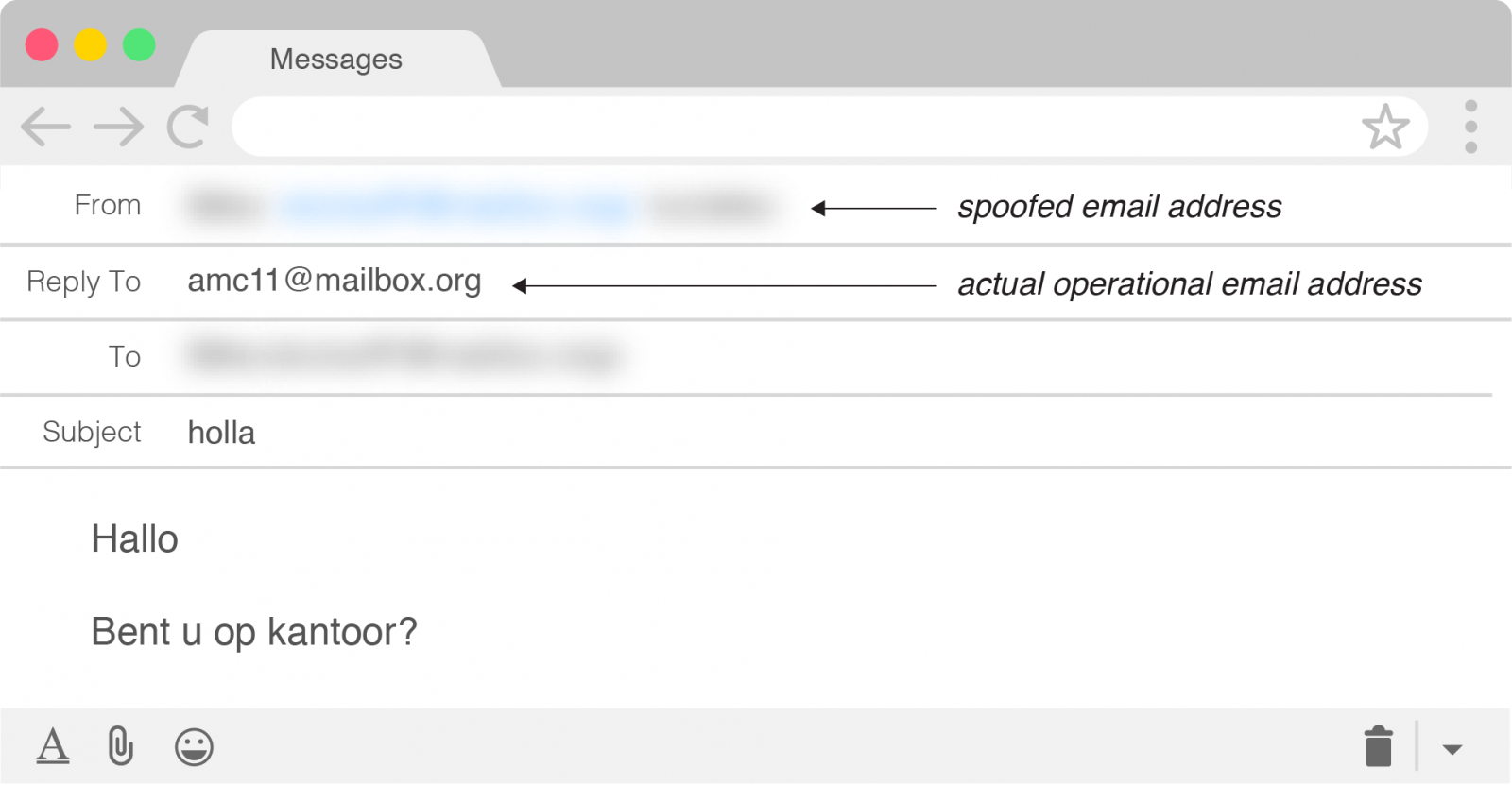
Originating in the United Kingdom, the group was off to a rough start this year, as they made the mistake of targeting Agari CFO Raymond Lim, for the second time in less than a year.
According to Agari, they collected and validated information about Lim in mid-January. Three and a half hours before running the attack, London Blue tested the phishing email to make sure it does not get blocked.
The BEC scammers tried their luck at diverting $86,000 from Agari to a bank account in Mexico, under the pretense of a down payment for an acquisition deal that was about to become public.
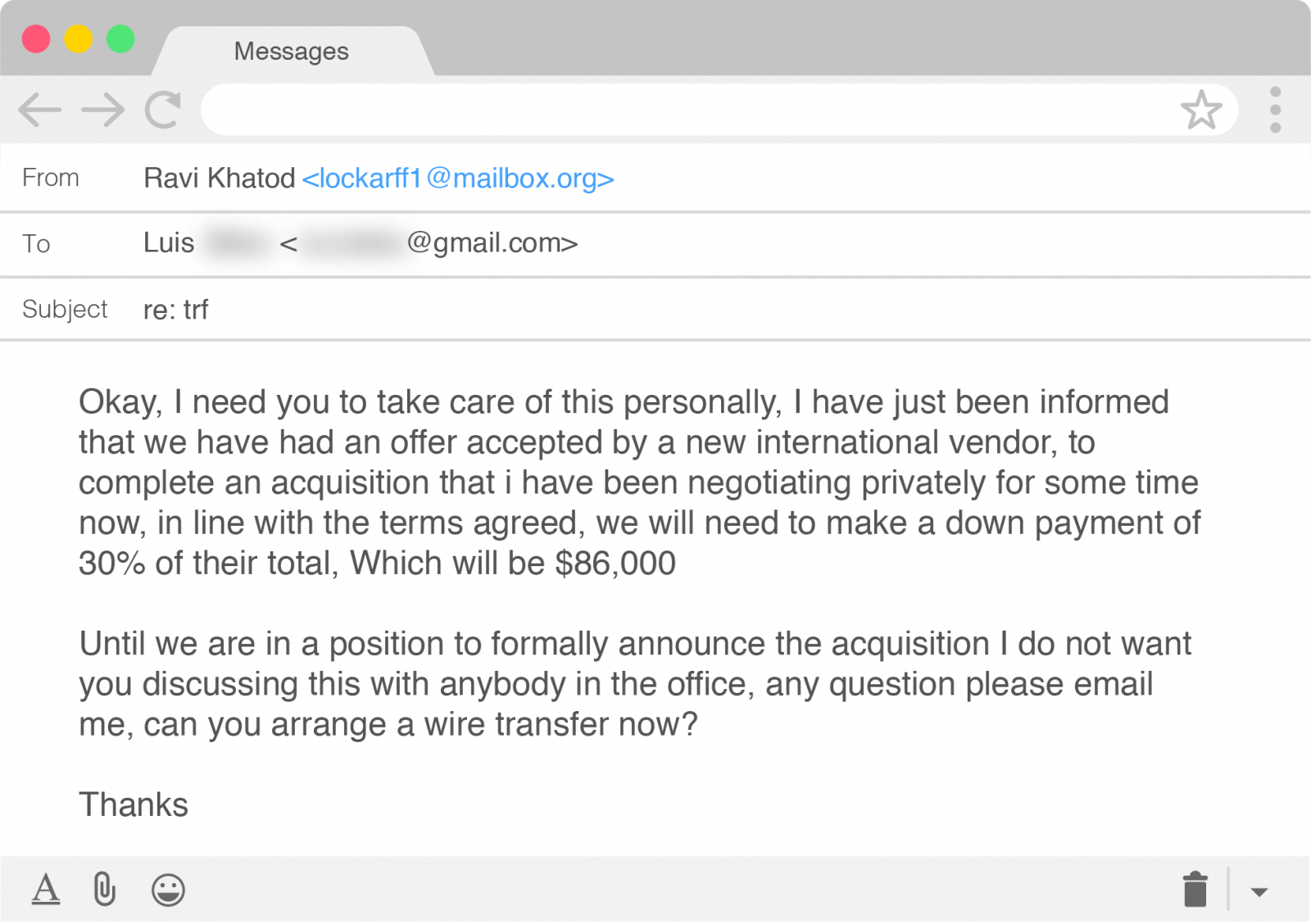
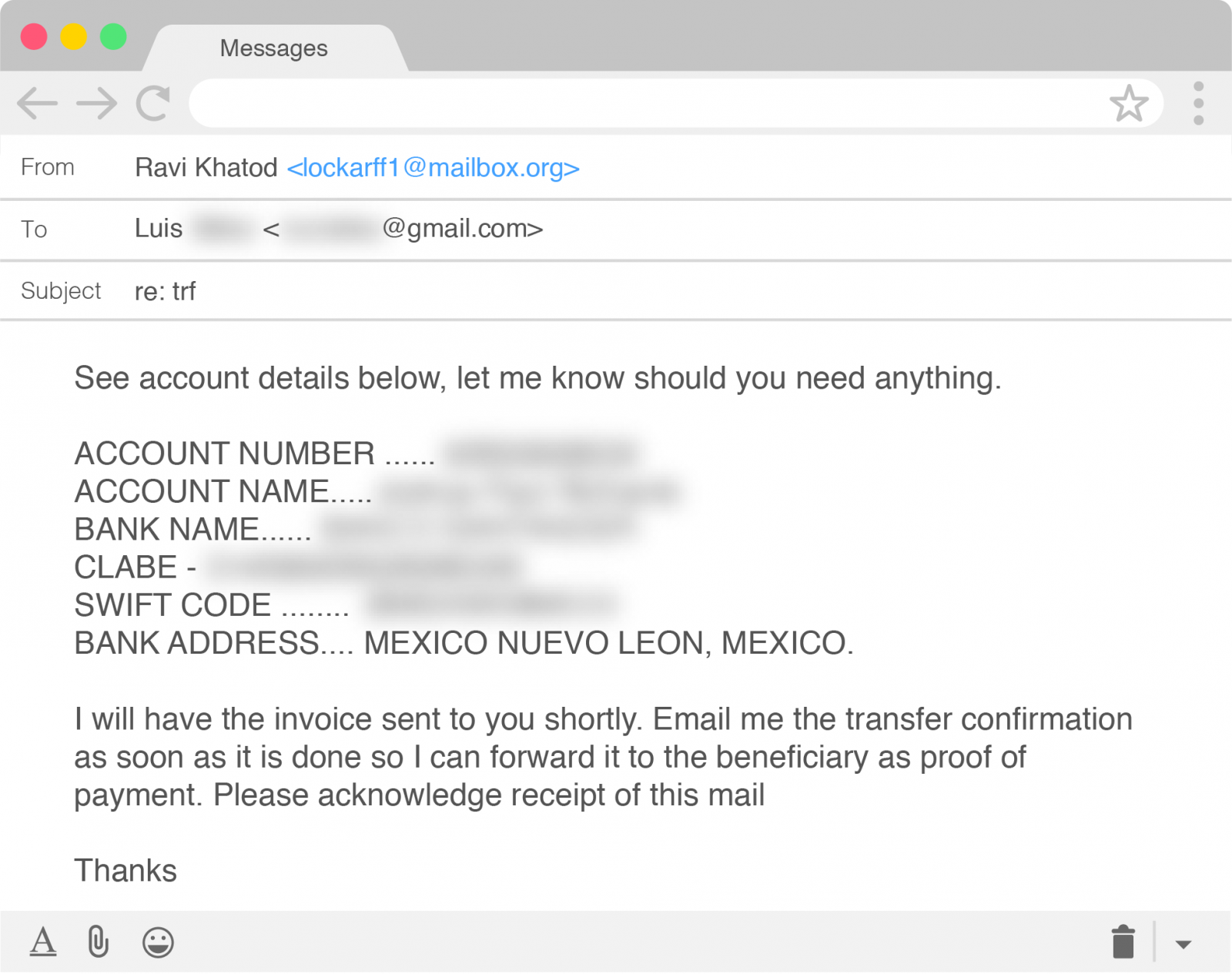
Agari Advanced Threat Protection blocked the email before it reached Lim’s inbox, but the researchers continued the conversation to learn more details about the group’s operation.
The company says that BEC scam groups will keep evolving and using formal business strategies and structure to carry out their work in a more effective way.
“London Blue’s use of legitimate commercial sales prospecting tools shows the out-of-box thinking these groups employ to identify new targets. The pure scale of the group’s target repository is evidence that BEC attacks are a threat to all businesses, regardless of size or location,” Agari concludes.
To read the original article:



