A Windows zero-day vulnerability which got patched by Microsoft as part of the company’s April 2019 Patch Tuesday together with 73 other flaws could allow potential attackers to take full control of vulnerable systems.
The 0-day was actively exploited before patching, with Kaspersky Lab’s researchers Vasiliy Berdnikov and Boris Larin finding an exploit in the wild actively targeting multiple 64-bit versions of Windows, ranging from “Windows 7 to older builds of Windows 10.”
One of five elevations of privilege flaws
This is not the first Local Privilege Escalation flaw discovered by the the Kaspersky Lab researchers recently, with following four others having been patched during the past few months by Redmond:
The Use-After-Free vulnerability tracked as CVE-2019-0859 is present in the win32k.sys kernel mode driver and it stems from the fact the “component fails to properly handle objects in memory.”
“An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights,” says Microsoft’s advisory.
Also, “To exploit this vulnerability, an attacker would first have to log on to the system. An attacker could then run a specially crafted application that could exploit the vulnerability and take control of an affected system.”
As further unearthed by the Kaspersky researchers, the vulnerability was used by threat actors to “make a trivial HTTP reverse shell” (also known as a backdoor) as part of a three-stage PowerShell-based exploitation procedure which would eventually help “the attacker gain full control over the victim’s system.”
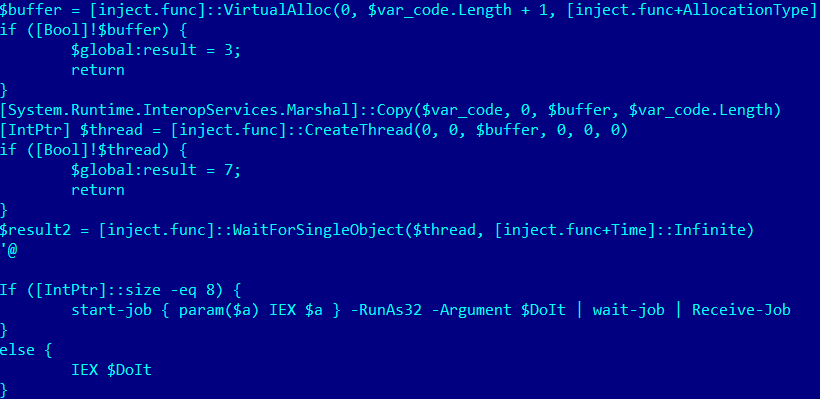
Backdoor enabled attackers to take full control
As detailed by Symantec’s 2019 Internet Security Threat Report, malicious PowerShell script usage has drastically increased by a remarkable 1,000% last year, following the overall trend of bad actors moving to living-of-the-land techniques which allow their malicious tools to stay stealthy after the initial injection for as much time as possible.
The active exploitation of this Windows zero-day using PowerShell scripts shows that bad actors have really embraced the use of readily available tools such as the omnipresent PowerShell to run their malicious tools and dropper scripts.
This is not the only zero-day vulnerability patched by Microsoft last week, with another elevation of privilege vulnerability present in the Win32k component (tracked as CVE-2019-0803) being fixed after previously reported by Alibaba Cloud Intelligence Security Team’s Donghai Zhu.
Just as CVE-2019-0859, the flaw found by Zhu was also exploited in the wild and would allow malicious actors to take full control of the impacted systems.
To read the original article:



