A digitally-signed rootkit is used in wide-reaching malicious activities aimed at stealing login credentials, payment information, and browsing history, spam social network users, and adware activity.
Dubbed Scranos by researchers, the rootkit poses as a video driver. Once installed, it can download any payload its operator chooses. The targets range from popular browsers Chrome, Chromium, Firefox, Opera, Edge, Internet Explorer, Baidu, and Yandex to services from Facebook, Amazon, Airbnb, Steam, and Youtube.
Relatively new on the scene
The certificate used for signing the rootkit, likely stolen, is a DigiCert issue for Yun Yu Health Management Consulting (Shanghai) Co., Ltd., a company that is not involved in software development. At the moment, the certificate is still valid, BleepingComputer was told.
Details about Scranos activity were first published in early January by researchers at Tencent Threat Intelligence Center, who provided a technical analysis of some of the components downloaded on infected computers.
The earliest samples the researchers saw related to this rootkit date from November 2018, which makes Scranos relatively new to the game.
It is a memory rootkit that infects Windows systems via fake software posing as pirated utilities, or legitimate applications like e-book readers, video players, and even anti-malware solutions.
To achieve persistence on the victim host, Scranos rewrites itself to disk before the computer shuts down. It keeps a low profile and deletes all payloads immediately after they serve their purpose; if need be, they can be retrieved at a later time by injecting a downloader into a legitimate ‘svchost.exe’ process.
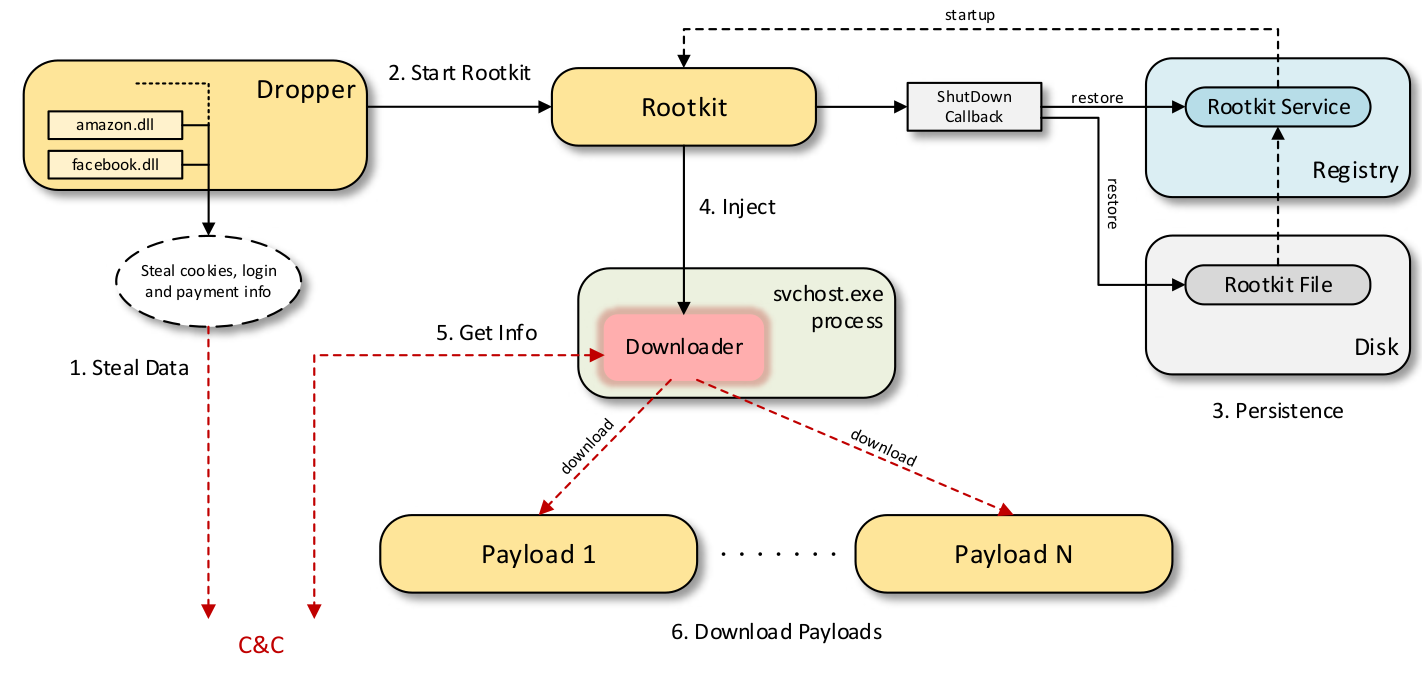
The functionality of the malware is limited to downloading and running the payload dropper, achieving persistence on the infected system, and deleting files that are still in use (for the purpose of removing payloads in memory).
According to an analysis from Bitdefender Labs, the rootkit downloader itself is multifunctional; it can also extract login credentials from the aforementioned browsers and uses specialized DLLs.
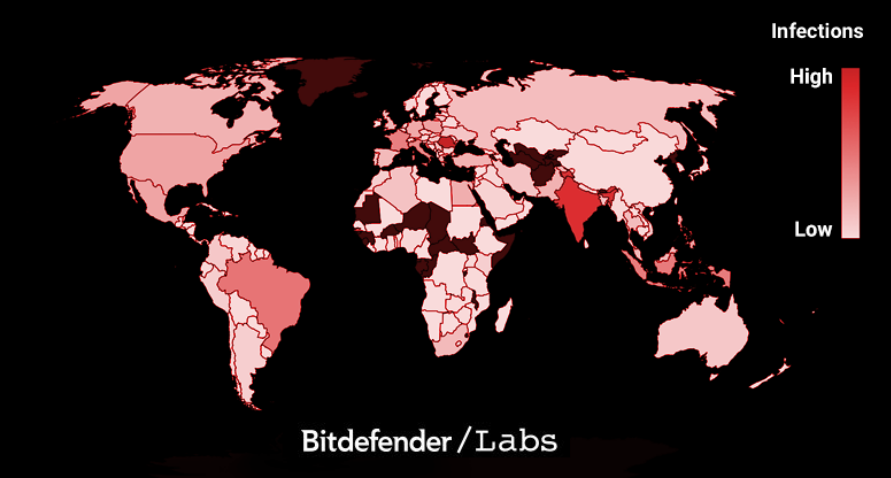
Spreading across the world
Among the payloads observed by the Romanian researchers is one for subscribing users to YouTube channels, a surprising action observed by Tencent researchers, given that its origin appears to be in China (tens of thousands of past victims were from the cities of Guangdong, Shanghai, Jiangsu, and Zhejiang), where YouTube is blocked at country level.
However, Bitdefender says that Scranos activity keeps evolving and reached computers in India, Romania, Brazil, France, Italy, and Indonesia. Moreover, the samples they analyzed suggest that the operators continuously test new components on already infected machines.
Payloads galore
The YouTube subscription payload uses Chrome in debugging mode and hides it from the taskbar, although the process remains visible. If Chrome is not present on the infected computer, the malware installs it on the system.
“After receiving a YouTube page from the C&C, the URL is opened in Chrome and the payload instructs Chrome to take various actions in the page: start a video, mute a video, subscribe to a channel, click ads. These operations are performed through debug commands,” Bitdefender writes in a report shared with BleepingComputer.
In a single day, the YouTube payload ran an aggressive promotion for a particular channel, which brought over 3,100 new subscribers.
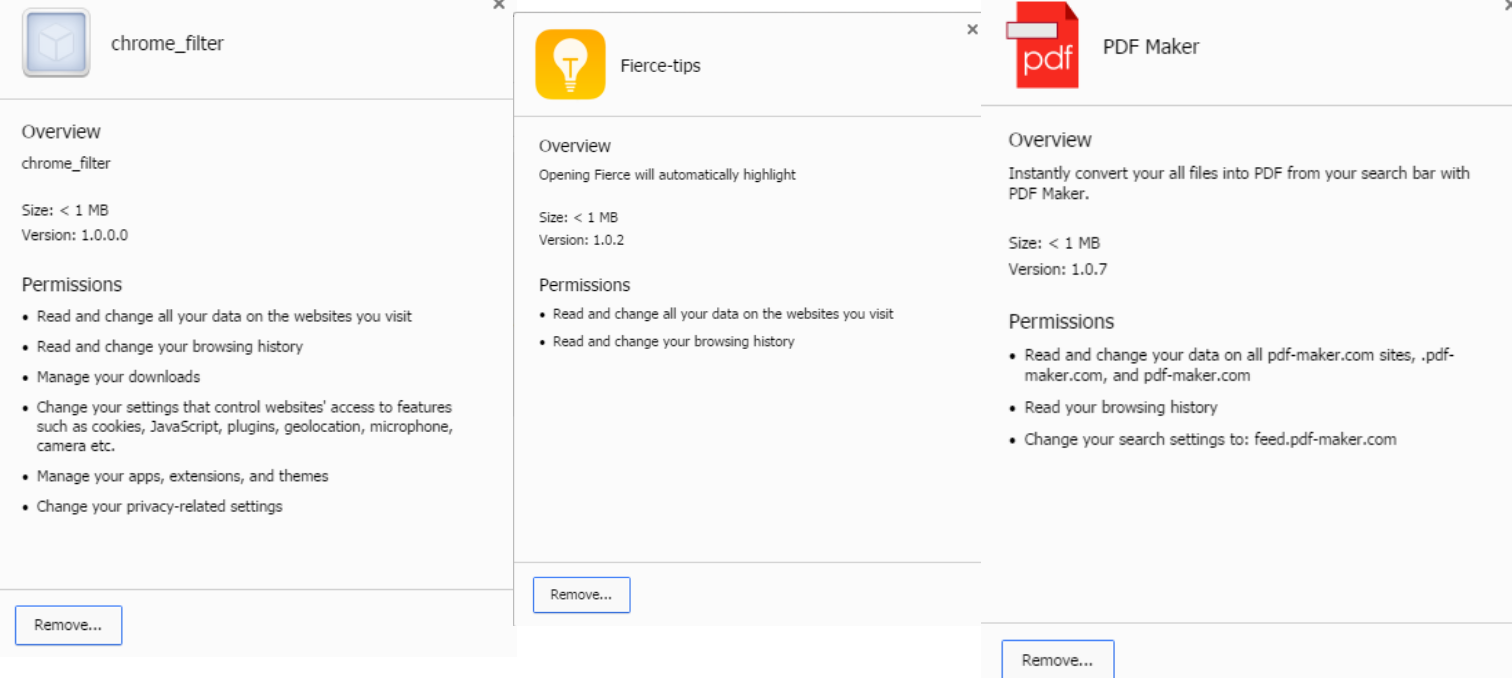
The payload for installing browser extensions targets Chrome, Opera, and Internet Explorer and is designed to add JavaScript on web pages, add context menu options, or change the default search engine.
On Chrome, it can add the extensions Chrome Filter, Fierce-tips, and PDF-Maker, the last one still being available in Chrome Web Store, installed by about 128,000 users at the moment of writing.
The Facebook spam payload is responsible for sending friend requests and phishing messages with links to suspicious Android APKs. It steals Facebook cookies from Chrome and other Chromium-based browsers, and Mozilla Firefox.
For looting the same information from Microsoft’s Edge, it relies on EdgeCookiesView, a legitimate tool from developer Nirsoft, whose products have been incorporated in the past by malware developers.
The malware for stealing information stored in Steam accounts can be included in the initial downloader that gets the rootkit but it also exists as a separate component.
It starts by resetting registry keys for remembering Steam account credentials so that the user is forced to log in. Apart from credentials, the data stolen includes a list of games installed on the system and the time when they were last played, and the games available in the Steam account.

Bitdefender researchers say that the Scranos operation is still a work in progress that continues to improve and to spread to other regions. The global infection rate at the moment is low – less than 5,000 in countries outside China, mostly on Windows 10 computers.
However, fresh activity was detected in March, when the command and control servers started to push other strains of malware, suggesting an affiliation with other parties.
To read the original article:



