The latest versions of UC Browser and UC Browser Mini Android apps with a total of over 600 million installs expose their users to URL spoofing attacks as explained by security researcher Arif Khan who found the flaw and reported it to the apps’ security team.
URL spoofing attacks are based on the attackers’ capability to change the URL displayed in the address bar of a web browser to trick their targets into thinking that the loaded website is controlled by a trusted party.
However, as is the case with the address bar spoofing vulnerability discovered by Khan in the UC Browser apps for Android, the site is actually controlled by the malicious actors behind the attack.
Unaware targets can be led to domains they control and camouflaging them as high-profile websites allowing potential attackers to steal their victims’ information using phishing landing pages or to drop malware on their computers via malvertising campaigns.
The URL spoofing issue
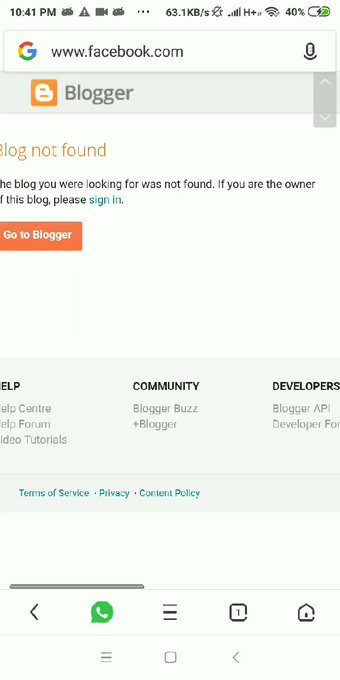
“URL Address Bar spoofing is the worst kind of phishing attack possible. Because it’s the only way to identify the site which the user is visiting,” said Khan.
As the researcher says in his advisory, UC Browser and UC Browser Mini make it possible for would-be attackers to “pose (his phishing domain) as the targeted site, for example, a domain blogspot.com can pretend to be facebook.com, by simply making a user visit www[.]google[.]com[.]blogspot.com[/?q=]www.facebook.com.”
“This is happening primarily because some mobile browsers are using bad regex checks. They are trying to enhance user UX by displaying only search term when the user searches for something on search engines like Google,” also said Khan.