Adware bundles are installing a VPN software called Pirate Chick, which then connects to a remote server to download and install malicious payloads such the AZORult password-stealing Trojan.
As adware bundles need to look as legal as possible, they require offers that they promote to have legitimate web sites with privacy policies and user agreements.
Such is the case with the Pirate Chick VPN, whose web site looks like any other VPN site and includes a free three months trial with no credit card required.
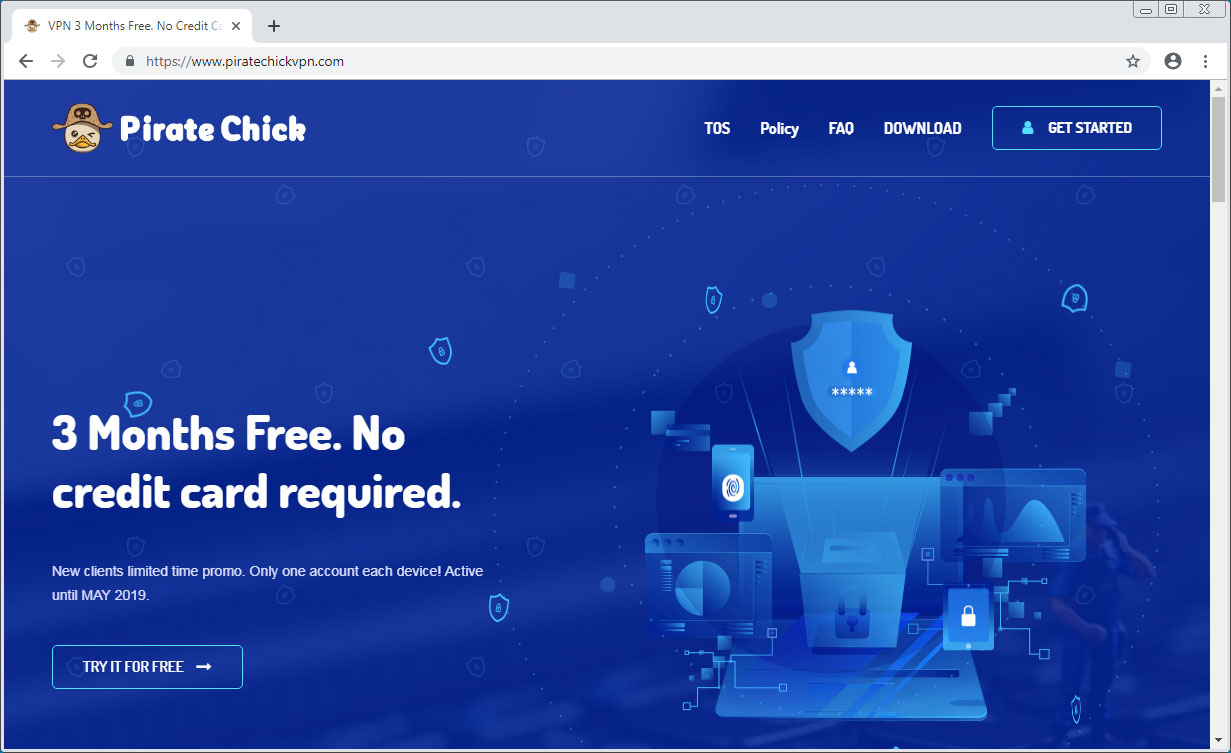
Even the executables are convincing as they are signed using a certificate from a UK company called ATX International Limited. This is becoming more normal, though, as we are finding most signed malware to be associated with UK businesses.
MalwareHunter, who discovered and shared this Pirate Chick with me, and I analyzed this sample and we both came to the same conclusion. This is a Trojan that pretends to be a legitimate VPN software, but in the background downloads and installs a malware payload on a victim.
A hidden malicious payload
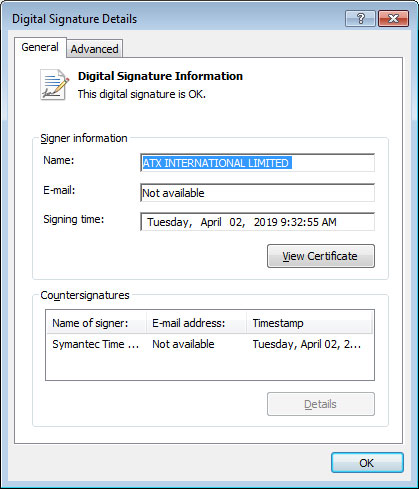
When you execute the installer for the Pirate Chick VPN, it will download and install a payload to the %Temp% folder and execute it. In the past this payload was the AZORult password-stealing Trojan as we will explain later. Currently, the payload is process monitor, which could be a temporary filler while they launch another campaign.
When first executed, the installer will combine a series of strings into process names, such as ImmunityDebugger, Fiddler, Wireshark, Regshot, and ProcessHacker. It will then check your list of running processes and if one of the processes is detected, it will skip the installation of the malware payload.
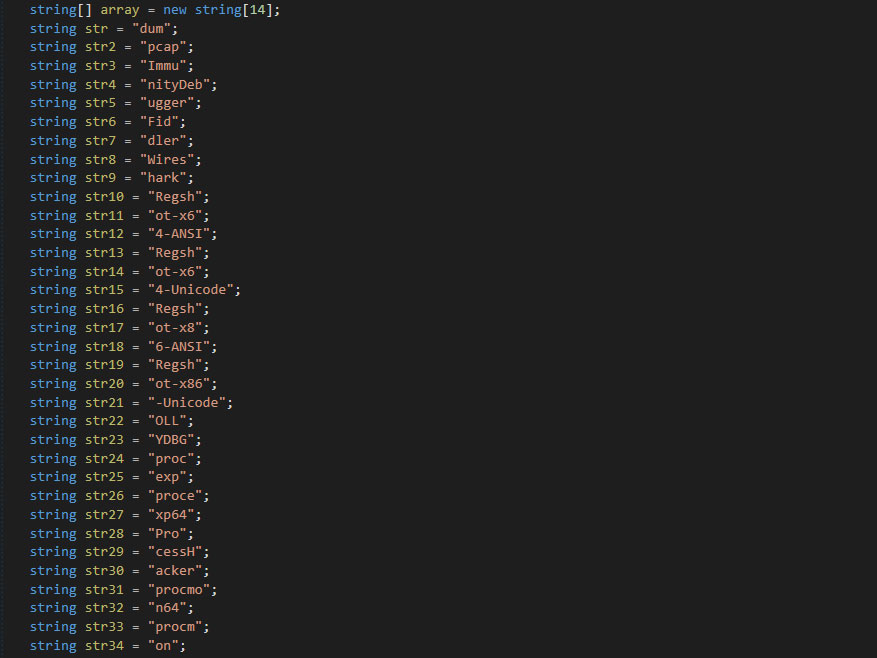
It then connect to https://www.piratechickvpn.com/collectStatistics.php, which returns the country of the visitor based on the IP address. If the user is from Russia, Belaris, Ukraine, or Kazakhstan, it will skip the malicious payload.
Next, it checks if the user is running under Vmware, VirtualBox, or HyperV. If so, it once again skips the malicious payload.
If the user passes the above checks, it will download a file from https://www.piratechickvpn.com/wohsm.txt, performs character replacements on its contents, and then base64 decode the string.
This turns the downloaded file into a working executable, which is saved to %Temp%\wohsm.exe and executed. As previously stated, this executable is currently the Sysinternals Process Monitor tool, but was previously AZORult.
Finally, the main installer for the Pirate Chick VPN is shown.
After installing the VPN, the user will be shown a splash screen asking them to signup.
Currently, this signup screen is broken, but shows how the Trojan was pretending to be a VPN program, while install a malicious payload.
Distributed through adware bundles
Based on a Any.Run session, we can see that Pirate Chick VPN is being distributed via fake Adobe Flash Players and adware bundles.
Adware bundles, especially the ones out of Russia, are increasingly becoming more aggressive in the types of “offers” that they are installing on victim’s machines.
In the past, they would install adware and unwanted extensions, but now they are installing miners, ransomware, password-stealing Trojans, and ad clickers.
In this particular case, the installer pretended to be a Flash Player installer, as can be seen from the icon below, and was most likely advertised as a Flash Player upgrade.

As you can see from the Any.Run process graph, piratechickvpnsetup.exe installs the vpnclientupdate.exe, which is AZORult.
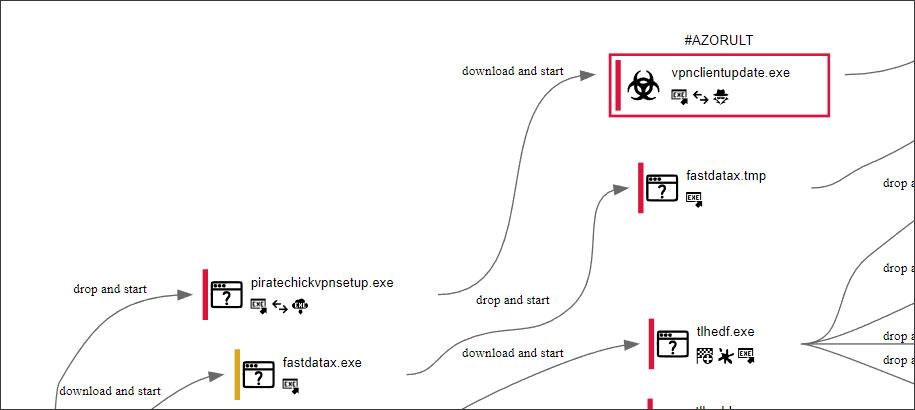
The Pirate Chick VPN is not currently installing the password-stealing Trojan, but does connect back to the site and downloads and runs an obfuscated copy of Procmon.exe.
They could just easily, though, switch it out for any malware they wish to install.
To read the original article:



