A variant of the Maze Ransomware, otherwise known as the ChaCha Ransomware, has been spotted being distributed by the Fallout exploit kit. An interesting feature of this ransomware is that it says the ransom amount will be different depending on whether the victim is a home computer, server, or workstation.
Malwarebytes security researcher Jérôme Segura discovered this ransomware being distributed by the Fallout exploit kit through a fake site pretending to be a cryptocurrency exchange app.
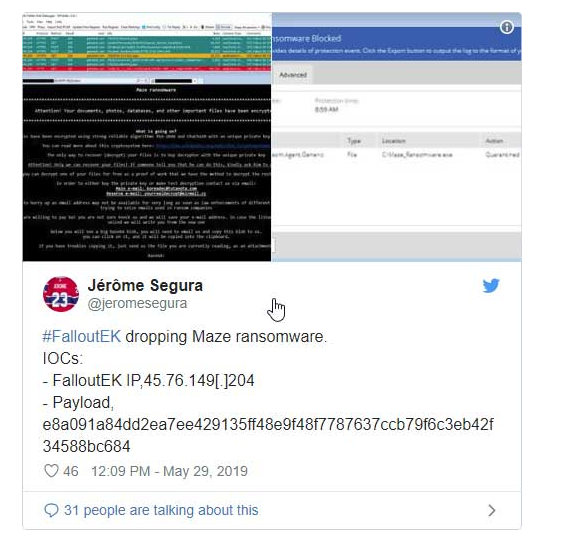
Segura told BleepingComputer that the attackers created a fake Abra cryptocurrency site in order to buy traffic from ad networks. Visitors to this site would then be redirected to the exploit kit landing page under certain conditions.
“The decoy site is used to pose as an advertiser and buy traffic from ad networks. From there, they can do conditional redirects towards the actual exploit kit landing page.”
The Maze Ransomware encryption process
According to Michael Gillespie, the Maze Ransomware utilizes RSA and ChaCha20 encryption as part of the encryption process.
“It generates an RSA pair on run, so the private of that is likely protected by a master RSA key, and the public is used to encrypt the ChaCha keys for individual files.”
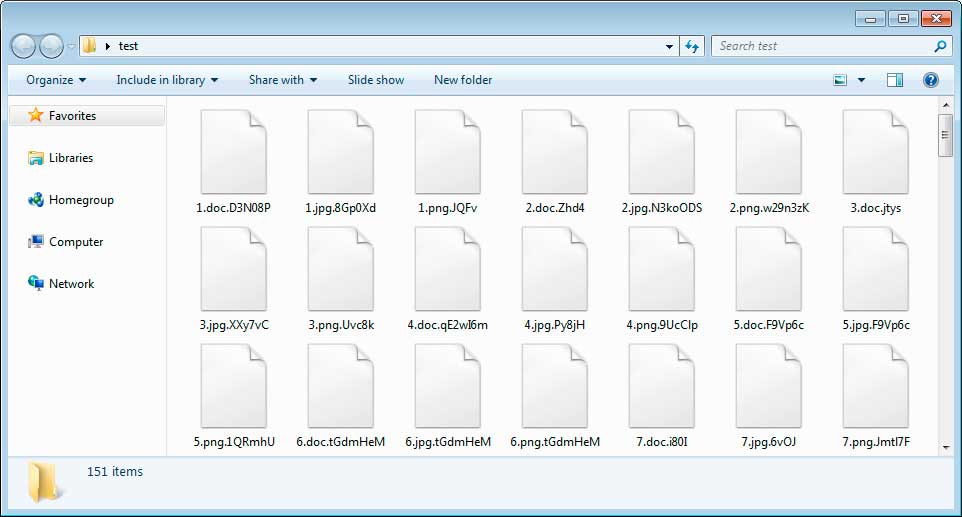
When executed, the ransomware will scan for files to encrypt and append different extensions to the files as can be seen below.
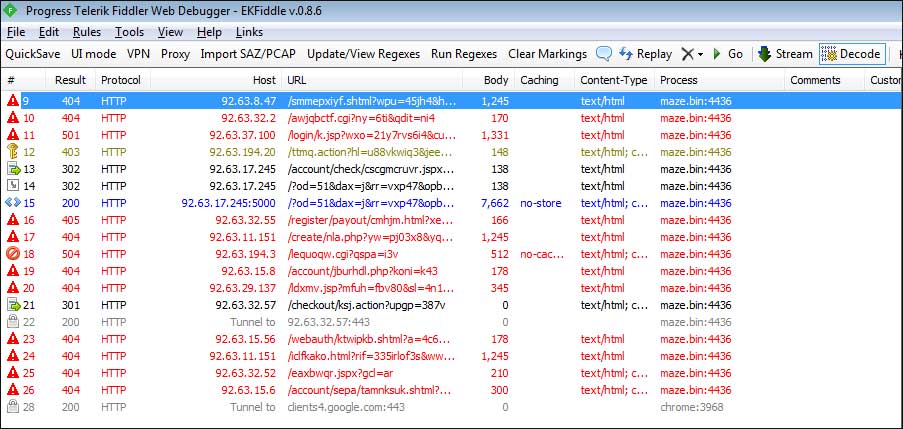
While running, the ransomware will attempt to connect to 15 sites by their IP address, which all start with 92. When connecting it will use random URLs as shown below. It is not known if these are non-functional Command & Control servers or being used for another reason.
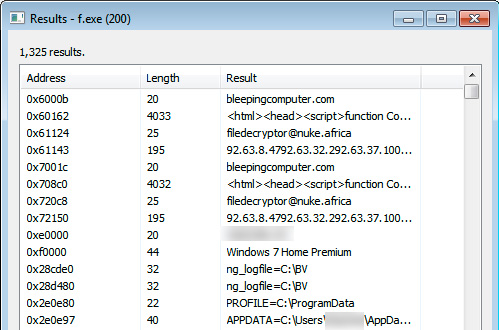
Strangely, when both I and Gillespie tested the malware, we saw the bleepingcomputer.com string in it’s memory. It is not known why it contains our domain name or how it is being used.
Finally, it will create a ransom note named DECRYPT-FILES.html that contains information on what happened to a victim’s files and an email to contact for payment instructions. This email is currently filedecryptor@nuke.africa.
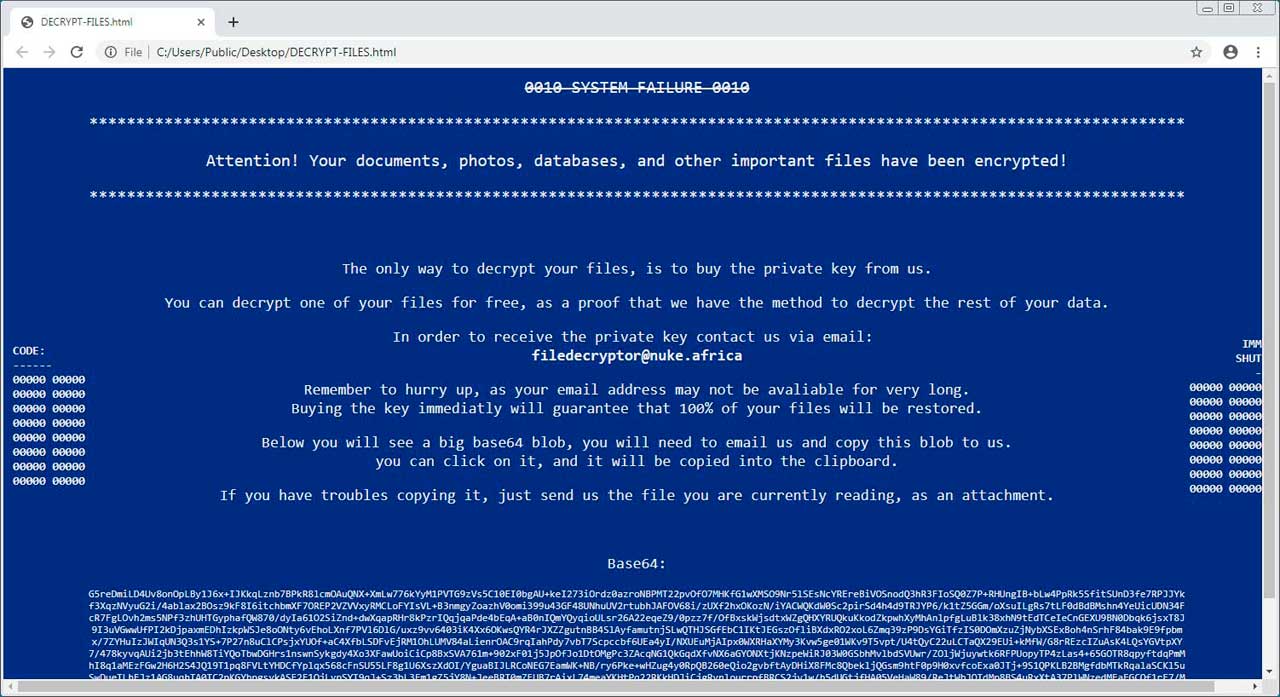
At the bottom of the ransom note will be a Base64 string, which contains an encrypted private decryption key and information about your computer, such as the computer name, logged in user, version of Windows, and other information used by the ransomware. The ransom note states that this text must be sent when emailing the ransomware developer.
At this time, there is no way to decrypt the files for free.
Detects what type of computer is infected
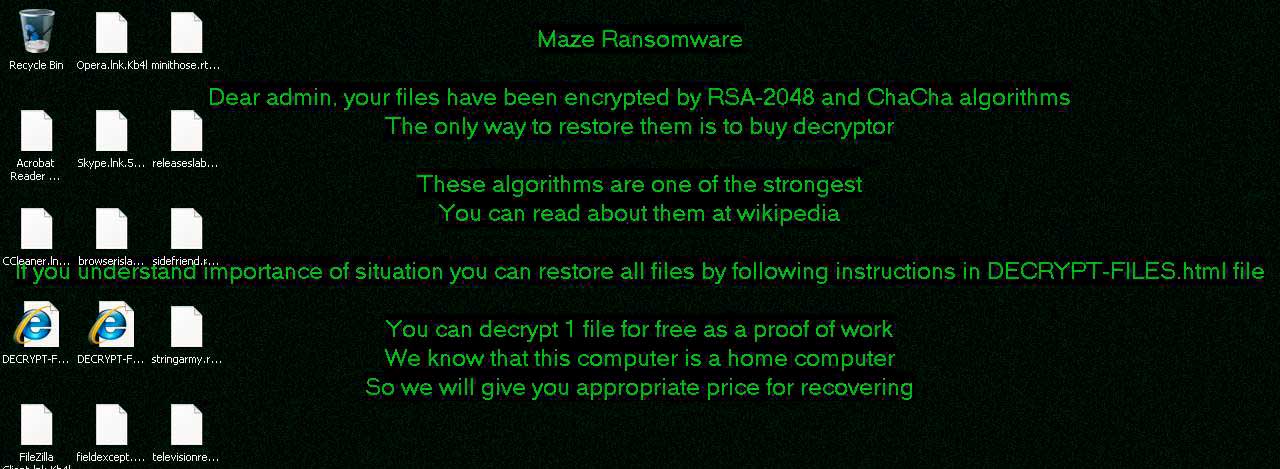
An interesting feature of this ransomware is that it will try and detect whether the computer is a home computer, workstation, domain controller, server, etc and then states it changes the ransom amounts accordingly.
This will be shown in the desktop wallpaper, which will use one of the following strings to indicate the type of computer it is:
standalone server
server in corporate network
workstation in corporate network
home computer
primary domain controller
backup server
very valuable for youAn example of a Maze wallpaper on a machine detected as a home computer from an Any.Run session can be seen below.
How to protect yourself from the Maze Ransomware
In order to protect yourself from the Maze Ransomware, or from any ransomware, it is important that you use good computing habits and security software. First and foremost, you should always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
Because Maze is being installed via exploit kits, make sure you have all the latest Windows security updates installed and that your programs are updated to the latest versions. This will prevent exploit kits from using vulnerabilities to infect your computer.
As ransomware is also known to be installed via hacked Remote Desktop services, it is very important to make sure its locked down correctly. This includes making sure that no computers running remote desktop services are connected directly to the Internet. Instead place computers running remote desktop behind VPNs so that they are only accessible to those who have VPN accounts on your network.
It is also important to setup proper account lockout policies so that it makes it difficult for accounts to be brute forced over Remote Desktop Services.
You should also have security software that incorporates behavioral detections to combat ransomware and not just signature detections or heuristics. For example, Emsisoft Anti-Malware and Malwarebytes Anti-Malware both contain behavioral detection that can prevent many, if not most, ransomware infections from encrypting a computer.
Last, but not least, make sure you practice the following good online security habits, which in many cases are the most important steps of all:
- Backup, Backup, Backup!
- Do not open attachments if you do not know who sent them.
- Do not open attachments until you confirm that the person actually sent you them,
- Scan attachments with tools like VirusTotal.
- Make sure all Windows updates are installed as soon as they come out! Also make sure you update all programs, especially Java, Flash, and Adobe Reader. Older programs contain security vulnerabilities that are commonly exploited by malware distributors. Therefore it is important to keep them updated.
- Make sure you use have some sort of security software installed.
- Use hard passwords and never reuse the same password at multiple sites.
- If you are using Remote Desktop Services, do not connect it directly to the Internet. Instead make it accessibly only via a VPN.
To read the original article:



