The Sodinokibi Ransomware has been spotted being distributed through malvertising that redirects to the RIG exploit kit. With the use of exploit kits, Sodinokibi is now using a wide stream of vectors to infect victims with the ransomware.
Last week we covered how Sodinokibi was quickly filling the vacuum left behind when GandCrab shut down by distributing through spam, server exploits, hacking sites to replace legitimate software with the ransomware, and by hacking into MSP backends.
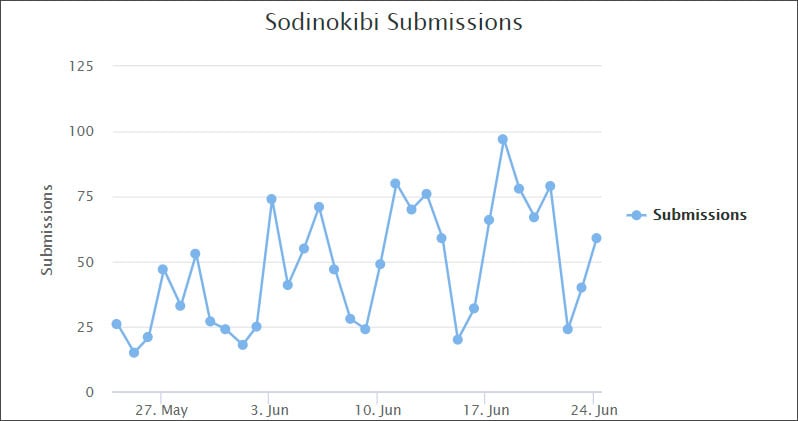
These are similar tactics that GandCrab had used in the past and you can see how Sodinokibi has been growing based on its submissions to ID-Ransomware.
Last night, exploit kit researcher nao_sec discovered that Sodinokibi, also known as REvil, is now being distributed through malvertising that leads to the RIG exploit kit.
Nao_sec told BleepingComputer that that was done through advertisements on the PopCash ad network that redirected users to the exploit kit based on certain conditions. Nao_sec was able to demonstrate how the exploit kit infected a Windows machine through this Any.run session, which is shown below.
With the addition of exploit kits to the distribution arsenal, this ransomware is poised to be a big player in the ransomware space.
As exploit kits rely on outdated software, the best defense is to make sure that you have all the latest Windows security updates installed as well as updates for Flash, Java, PDF Readers, and your browsers. Running outdated and vulnerable software will only open you up to the risks of being infected.
To read the original article:https://www.bleepingcomputer.com/news/security/sodinokibi-ransomware-now-pushed-by-exploit-kits-and-malvertising/



