Trickbot trojan now comes with a separate module for stealing browser cookies, threat researchers found on Tuesday, marking new progress in the malware’s development.
Reported in October 2016, Trickbot started as a banking trojan but constant updates turned it into a multi-purpose threat that can steal sensitive information from applications, send spam, as well as deliver other types of malware on an infected computer.
The new module is dubbed Cookie Grabber and its purpose is only to steal cookies – bits of text that websites save in the browser for various purposes like remembering the login state, the website preferences, personalized content; or for tracking a user’s browsing activity.
Trickbot’s new module was first spotted on July 2 by malware researcher Brad Duncan during a Trickbot infection that delivered the file “cookiesDLL64.”
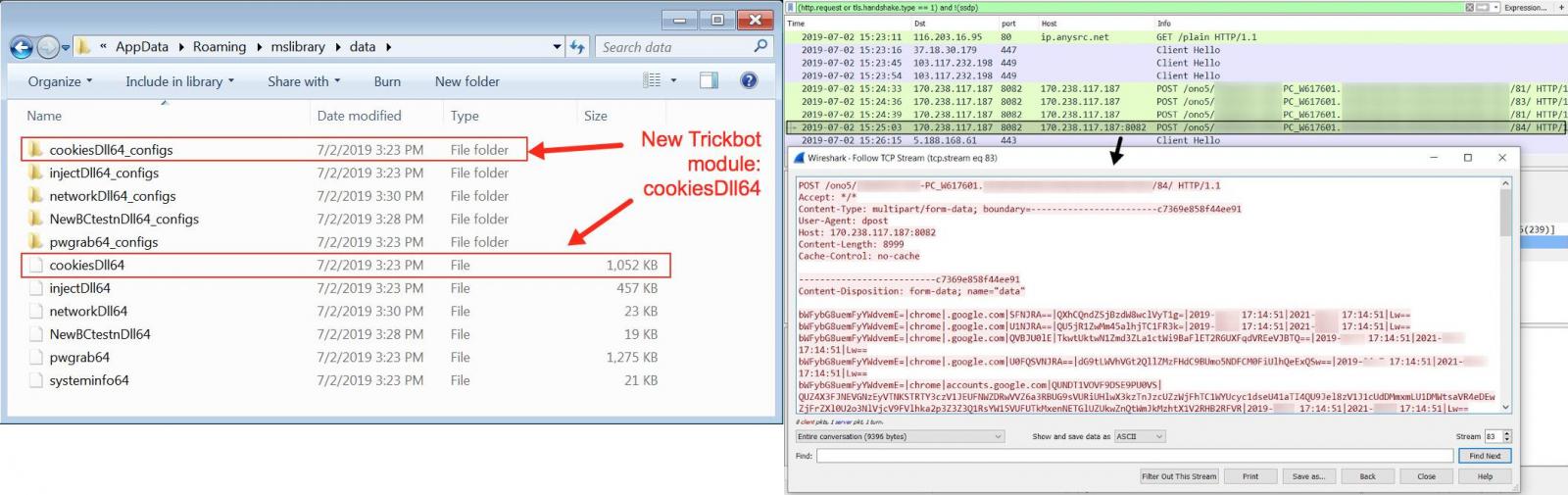
Duncan published a short post with details about the traffic generated by Trickbot’s latest module and the artifacts associated with it, as found on an infected Windows host. and the artifacts found on an infected Windows host that had the browser stealing module.
Researcher Vitali Kremez also saw Trickbot’s new Cookie Grabber module and confirmed that it functions as a separate add-on for the malware.
“Indeed, this is the new #TrickBot “#CookieGrabber” browser module (with local db parser) is released with the usual export ord (Start, Control, Release, FreeBuffer) and dpost config,” Kremez replied to Duncan’s tweet about Cookie Grabber.
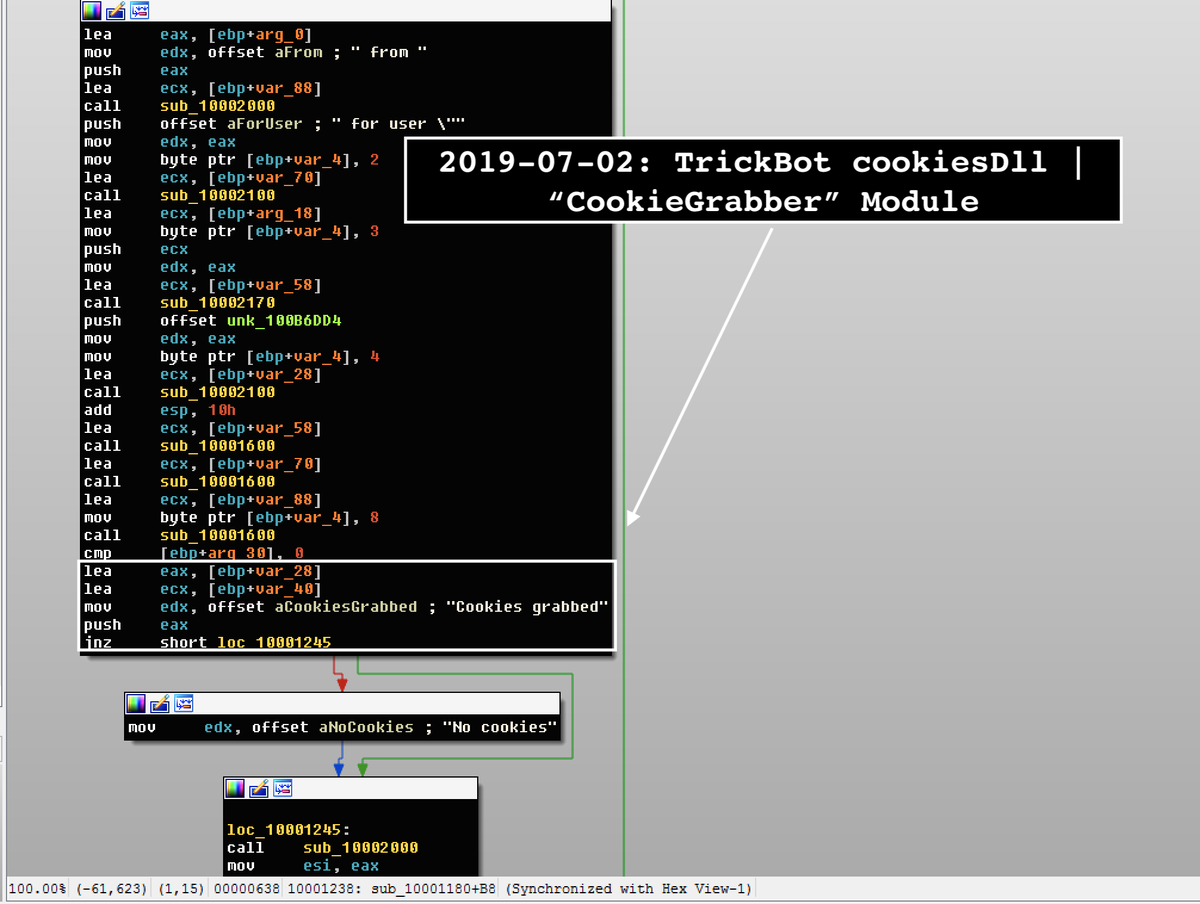
Kremez found that the new module’s build date was June 27, and it targeted the cookie storage databases of all major web browsers: Chrome, Firefox, Internet Explorer, Microsoft Edge.
The researcher told BleepingComputer that Trickbot had cookie-stealing capabilities bundled in another component but now this is completely standalone and comes with its own configuration file.
This means that once delivered to a victim host, the malware operators can control it independently of other info-stealing features.
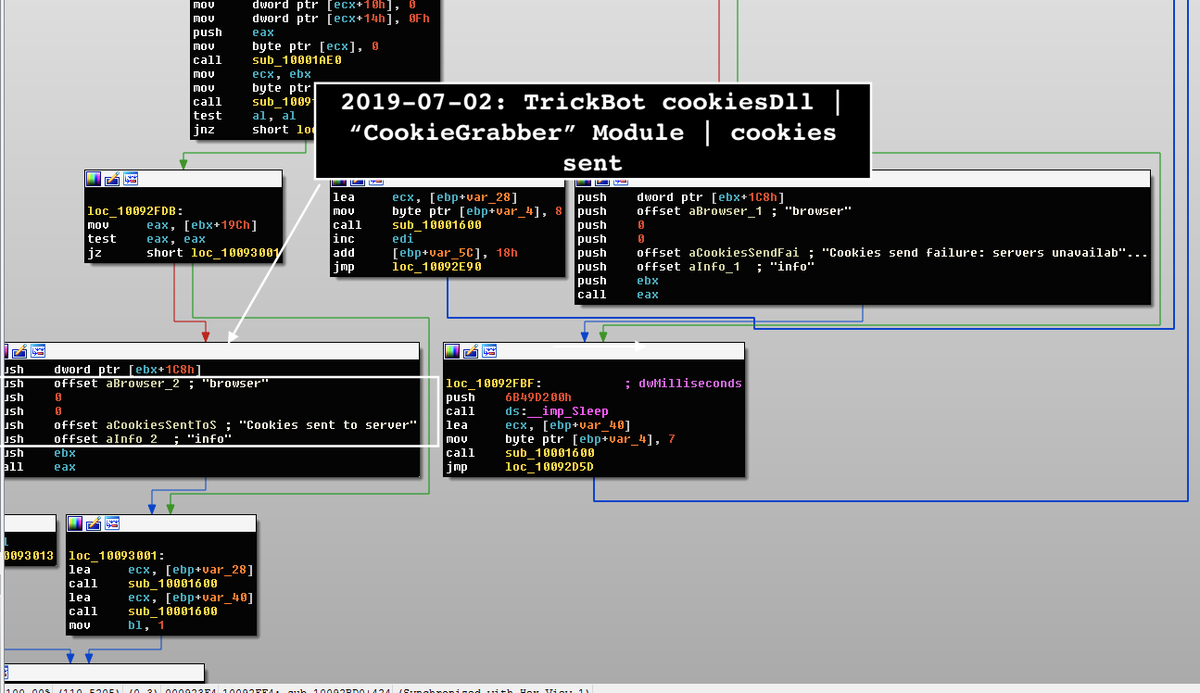
Kremez believes that the malware authors realized that the cookie grabber was not absolutely necessary in the other module. By collecting this type of info about the host the operator can better profile the victim and customize the subsequent steps of the attack.
“I think they are separating each functionality into separate modular components,” the researcher told us.
This would offer finer control over each feature and make the malware leaner. It would also allow flexibility in adjusting the malware capabilities according to the purpose of each campaign.
To read the original article:



