Over $800,000 were stolen from the City of Griffin, Georgia, by scammers in a BEC (Business Email Compromise) attack by redirecting two transactions to their own bank accounts according to local media sources.
BEC (also known as Email Account Compromise – EAC) fraud schemes are widespread scams in which crooks deceive employees of privately-held companies and public organizations into wiring money entities they trust but whose bank accounts were changed with ones controlled by the criminals before the attacks.
Following the standard BEC attack “procedure,” the attackers used a phishing email to trick City of Griffin Finance Department official Chuck Olmstead into wiring a payment to their account instead of the one of the legitimate vendor who was supposed to receive those funds.
Attackers stole the money in two separate transactions
“He (Olmstead) stated that a company they use for the water treatment facilities (PF Moon) sent an email requesting an account change and needed to update information. Everything looked accurate on the email so the information was exchanged,” said Griffin Police Department Master Patrol Officer Chip Johns according to The Grip.
“The first transaction went through on June 21 for $581,180.51 (reference case #19-005312). The second transaction went through on June 26, 2019 for $221,318.78. It was found later that the email address used was not the correct email. He stated that SunTrust believes they can recover the money in the next few days.”
The county seat of Spalding County, Georgia, has not yet recovered the stolen funds and the incident discovered on June 26 is currently being investigated by the Federal Bureau of Investigation (FBI) according to Griffin City Manager Kenny L. Smith.
“The actual true vendor called wanting to know where their payment was, and we told them we’d already paid them. They said they hadn’t received it, so we went back and looked,” said Smith. “Once we discovered there was a slight differentiation in the emails, that’s when we learned what had happened.”
Vendor’s systems possibly breached before the attack
Smith also mentioned suspicions about the P.F. Moon’s systems being infiltrated prior to the attack seeing that the scammers knew very specific information such as invoice amounts:
We thought someone had hacked the vendor’s system, and we still suspect that. We received an electronic invoice that appeared to be from a vendor we do business with. Whoever fraudulently sent that invoice knew that we did business with that company, knew the project done by this company and the cost of that project. They knew the invoice amounts in relation to the project worked on. We feel like for them to know all that information, someone had to have gotten into the vendor’s system, so I guess that’s what needs to be investigated by authorities – how they got ahold of that information in order to send the fraudulent invoices.
Critical Path Security researcher Patrick Kelley told BleepingComputer that he was able to quickly find the credentials bad actors would need to infiltrate both the City of Griffin and P.F. Moon’s systems with the help of several OSINT tools and techniques such as Shodan, RiskIQ’s PassiveTotal, data dumps, and pastes.
“I work heavily with small governments. Very similar issues across all municipalities. Small budgets. High expectations. I was VERY happy that the City of Griffin was doing Security Awareness Training. It’s quite rare,” added Kelley.
“The biggest thing we’ve been pushing that works are phone, text, some sort of additional factor to authorize a payment change. We’ve had Commissioners payments re-routed several times.”
According to 11 Alive, the Griffin City Manager also stated that “The City has the highest degree of firewall protection and constantly trains employees on the latest methods that hackers use, however the criminals seem to always be one step ahead.”
“This unfortunate incident resulted in a large sum of money being misappropriated to a fraudulent account, however, a thorough criminal investigation has ensued and we are confident the funds will be restored. Let this be a warning to all businesses and citizens to be extremely diligent with on-line financial transactions.”
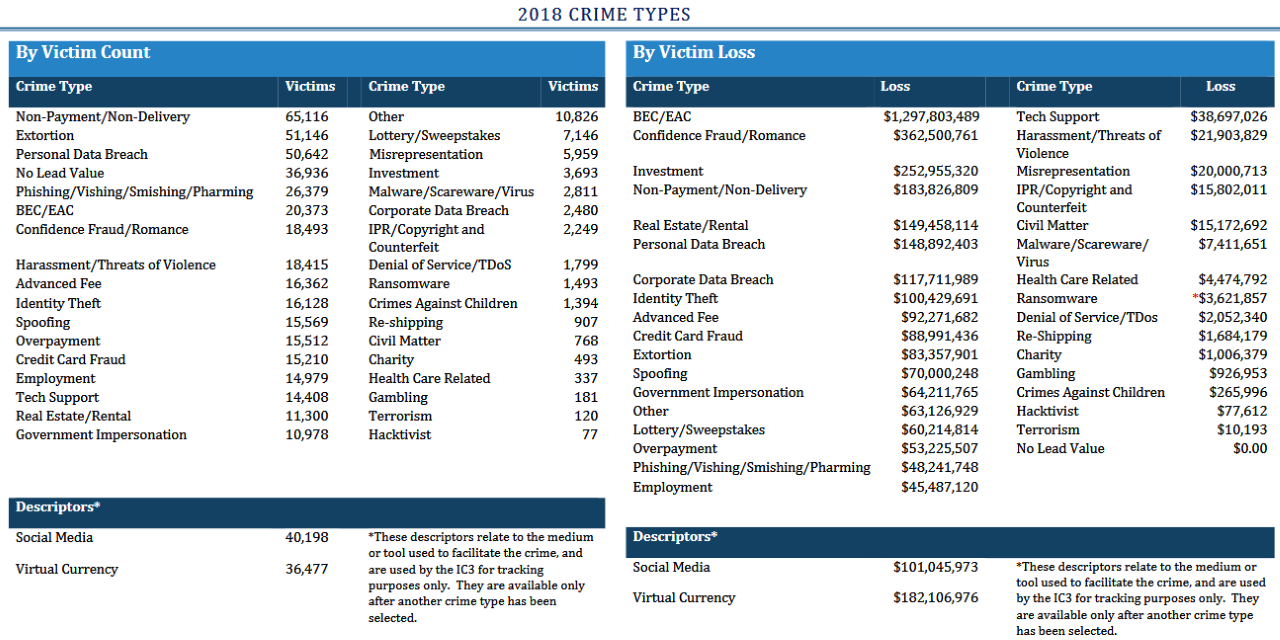
The City of Griffin incident follows a trend reported by the FBI’s Internet Crime Complaint Center (IC3) in its 2018 Internet Crime Report which shows that cybercriminals behind BEC scams made a staggering $1,2 billion in yearly profits by targeting wire transfer payments of individuals and businesses.
As IC3 explains , “Through the years, the scam has seen personal emails compromised, vendor emails compromised, spoofed lawyer email accounts, requests for W-2 information, and the targeting of the real estate sector.”
Also, as detailed in a Proofpoint report from January, BEC attacks have seen an explosive 476% growth between Q4 2017 and Q4 2018, with the total number of email fraud attempts against commercial entities increasing by 226% QoQ.
BleepingComputer has reached out to City of Griffin officials and P.F. Moon for comment but had not heard back at the time of this publication. This article will be updated when a response is received.
To read the original article:



