Researchers Say Campaign Uses Email Hyperlink Splits to Evade URL Filters.
Researchers stumbled across one phishing email held in an inbox using Microsoft’s Office 365 Advanced Threat Protection, according to Cofense.
What makes this phishing attack different is that instead of using a hyperlink to send victims to a malicious landing page, this scheme deploys an embedded “base href” URL to help hide the true intent from anti-virus and other security tools, Cofense says.
The attackers behind this phishing campaign also sought out as many American Express users as possible and did not discriminate between corporate users or consumers, according to Milo Salvia, a researcher at Cofense, who wrote about the issue this week. The attack targeted users four types of American Express accounts: actual credit cards, membership reward accounts, merchant accounts and American Express @Work accounts, Salvia notes.
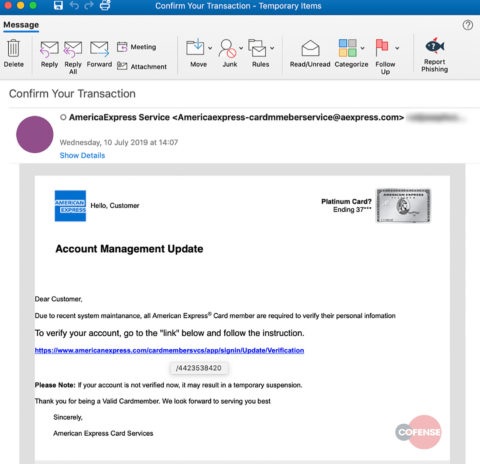 Phishing email targeting American Express customers (Image: Cofense)The number of affected customers, the date of the attack or whether any data has appeared on dark net forums remains unknown. But Salvia says this type of scheme is an efficient way to target customers in bulk, especially when the emails are sent in such high volumes.
Phishing email targeting American Express customers (Image: Cofense)The number of affected customers, the date of the attack or whether any data has appeared on dark net forums remains unknown. But Salvia says this type of scheme is an efficient way to target customers in bulk, especially when the emails are sent in such high volumes.
“The broad stroke attack would be very efficient when sent en masse, especially with its clever technique for bypassing URL filters and email gateways, Salvia wrote in a blog.
In 2018, American Express added about 12 million card members, and card activity increased about 9 percent last year compared to the previous year, according to the company’s 2018 revenue report.
A spokesperson for American Express did not reply to a request for comment.
Twofold Setback
As part of this new phishing campaign, attackers used the base HTML links to split the phishing URL into two pieces, which allowed the malicious URL to evade filters. Current scanning devices do not have the ability to detect it as one malicious entity, according to Cofense.
At the same time, the base URL acted as the building block for other URLs within the phishing message, Cofense reports.
“This tactic helps the attacker evade URL filters and gateways that have active URL scanning services, which currently do not have the capability to combine these inert pieces into a scannable malicious URL,” Salvia says.
Gone Phishing
Cofense researchers found that the attackers in this campaign targeted card holders with a phishing email requesting they update their card details for system maintenance or face a temporary shutdown of their account. Despite many grammatical and spelling mistakes, the message created a sense of urgency, Cofense says.
The campaign is just one example of how attackers are blurring the lines between consumers and business users.
Amazon Prime users also were recently targeted in a similar way by a phishing kit called 16Shop (see: Phishing Campaign Tied to Amazon Prime Day).
The phishing kit sent an email requesting Amazon Prime account holders update their information ahead of the Amazon Prime Day. In 2018, 16Shop had targeted Apple users in the same way.
Increasing Concerns
In the 2019 Internet Security Threat Report, researchers from Symantec found that spear-phishing emails remained the most popular mechanism for attack, used by 65 percent of cybercriminal groups during 2018.
The study also noted that for almost 96 percent of these groups, intelligence gathering was the main focus.
David Finn, a former healthcare CIO who is now executive vice president of security consulting firm CynergisTek, previously told Information Security Media Group that phishing is one of the top causes for data breaches. “We will certainly need the [security] technology, but the phishers or spammers are actually relying on the human frailties of trust,” Finn said (see: Phishing: Mitigating Risk, Minimizing Damage).
On Thursday, Barracuda Networks published a report that found so-called lateral phishing, where attackers use hijacked accounts they’ve recently compromised to send phishing emails to an array of recipients, is a problem for one in seven organizations in the U.S.
To read the original article:
https://www.bankinfosecurity.com/new-phishing-scheme-targets-amex-card-holders-a-12796



