BSI, the German national cybersecurity authority, has issued a warning regarding a malspam campaign that distributes the Sodinokibi ransomware via emails designed to look like official BSI messages.
The mails are sent from the meldung@bsi-bund.org email address and, according to the BSI, the individuals targeted by this attack should not “open mails, links and attachments from this sender!” The official BSI email domain is bsi.bund.de as per CERT-Bund.
By using “Warnmeldung kompromittierter Benutzerdaten” as the subject line — which translates to “Warning message of compromised user data” — the attackers are trying to trick their targets into reacting to the bait out of curiosity and to open the infected attachments without giving it a second thought.
BleepingComputer independently tested and confirmed that the ZIP attachment delivered by this campaign will infect the targets after launching the Windows shortcut camouflaged as a PDF document within the archive.
Once executed, the shortcut launches a remote HTA file (short for HTML Application) available at http://grouphk[.]xyz/out-1308780833.hta using a PowerShell command which simply prepends HTTP to the URL of the domain used to host the HTA payload.
Spam email (German)
Subject: Warnmeldung kompromittierter Benutzerdaten - Bundesamt für Sicherheit in der Informationstechnik
Content:
Sehr geehrte Damen und Herren,
der europäische Rechtsakt zur Cyber-Sicherheit ("Cybersecurity Act") ist am 27. Juni 2019 in Kraft getreten. Das Bundesamt für Sicherheit in der Informationstechnik ist seitdem verpflichtet Sie über möglichen Missbrauch Ihrer Daten zu informieren.
Am 14. Juli 2019 wurden mehrere Schwachstellen auf hoch frequentierten Internetseiten identifiziert, welche zu Verlust von persönlichen Daten geführt haben. Nach sorgfältiger Analyse der uns vorliegendenden Datensätzen. können wir bestimmend sagen, dass Ihre Daten teil des vorliegenden Datensatzes sind, wir raten Ihnen deshalb umgehend kompromittierte Passwörter zu ändern. Spam email (English)
Subject: Warning message of compromised user data - Federal Office for Information Security
Content:
Dear Sirs and Madames,
The European Cybersecurity Act entered into force on 27 June 2019. Since then, the Federal Office for Information Security has been obliged to inform you about possible misuse of your data.
On July 14, 2019, several vulnerabilities were found on high-traffic websites, which led to the loss of personal information. After careful analysis of the datasets available to us, we can say that your data is part of this dataset, so we advise you to immediately change compromised passwords.The HTA file will be opened using a Living off the Land (LotL) tactic that employs the legitimate mshta.exe Windows binary as a simple method to avoid detection.
Sodinokibi (also known as REvil and Sodin), the final malicious payload in the attack according to the German cyber-security agency, is downloaded from the same domain used to host the malicious HTA file.
The file-encrypting malware was discovered in April by the Cisco Talos group when it was used in attacks that exploited an Oracle WebLogic critical vulnerability.
After the ransomware is executed on a compromised computer, it will run the following commands to delete shadow volume copies and to disable Windows startup repair:
"C:\Windows\System32\cmd.exe" /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set {default} recoveryenabled No & bcdedit /set {default} bootstatuspolicy ignoreallfailuresSodinokibi will then encrypt the victims’ files, appending a random and unique extension for each of the infected machines.
The malware will also create ransom notes named using the [extension]-HOW-TO-DECRYPT.txt format for all scanned folders, with the ransom notes also featuring unique keys and links to the payment site.
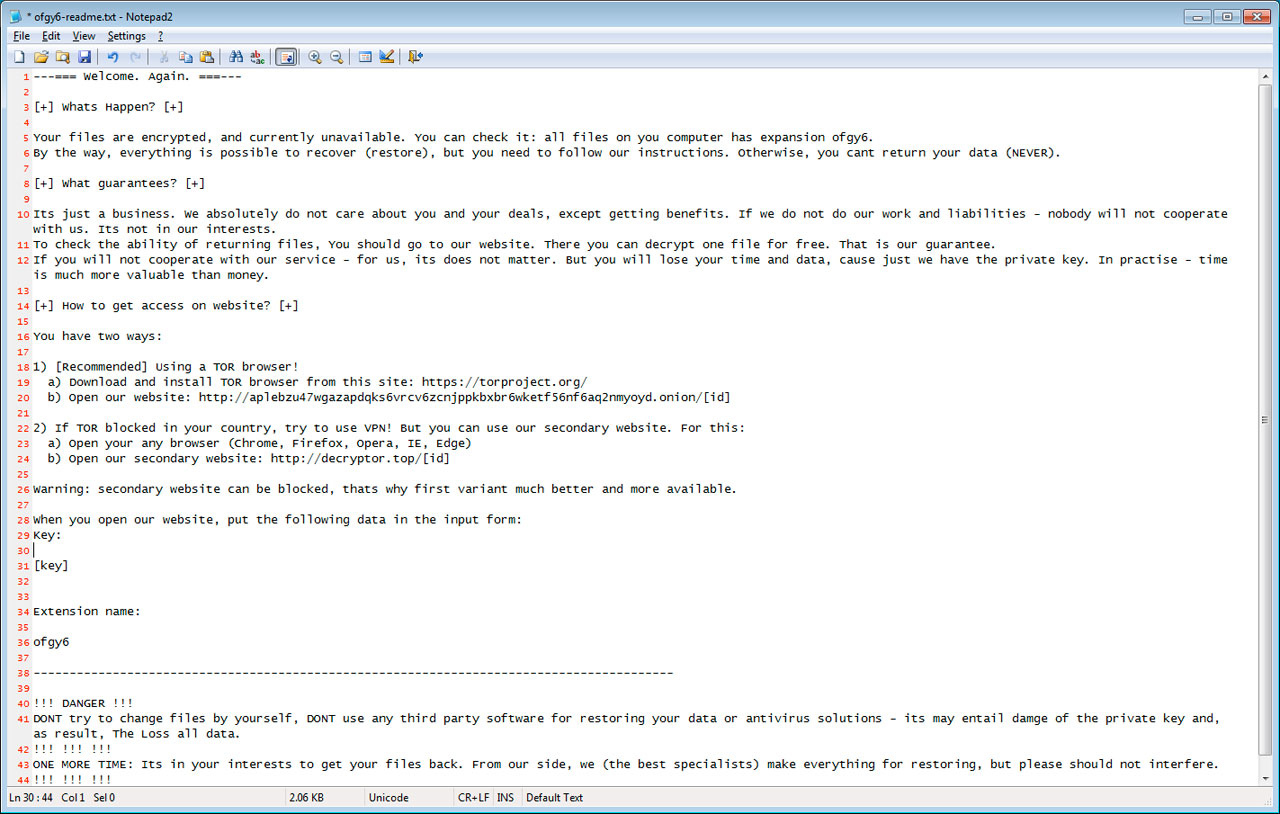
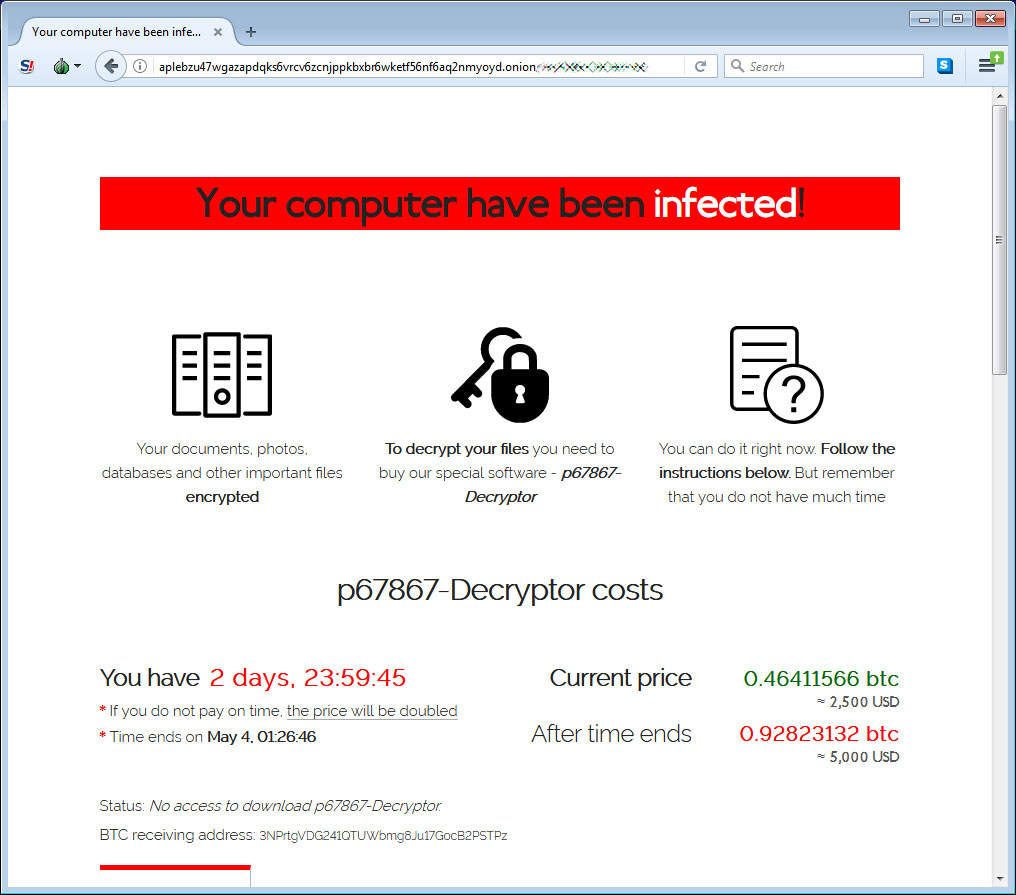
When the victims visit the payment sites supplied by the attackers, they will have to enter their unique extension and key to get to the ransom request page.
The page which displays the ransom amount — $2500 worth of Bitcoin and $5000 it the two-day timer expires — and the Bitcoin address that should be used to make the payment.
The Sodinokibi ransomware was also used by cyber-criminals to target German users in May when another malspam campaign actively distributed the malware via emails disguised as foreclosure notifications.
Sodinokibi was also observed while increasing its privileges on compromised machines by exploiting the CVE-2018-8453 vulnerability in the Win32k component present on Windows 7 through 10 and Server editions, as Kaspersky found.
To read the original article:



