A new version of the TrickBot banking Trojan continues its evolution of targeting security software in order to prevent its detection and removal. In this new version, TrickBot has set its sights on Windows Defender, which for many people is the only antivirus installed on a Windows 10 machine.
TrickBot is a banking Trojan that attempts to steal online banking credentials, cryptocurrency wallets, browser information, and other credentials saved on your PC and browser.
When TrickBot is executed it first starts a loader that gets the system ready by disabling Windows services and processes associated with security software and performing elevation to gain higher system privileges. When that is completed, it will load the “core” component by injecting a DLL that then downloads modules used to steal information from the computer, contains the communication layer, and perform other tasks.
Prior to this version, the TrickBot loader would perform a basic targeting of Windows Defender, soon to be called Microsoft Defender, by performing the following steps:
- Disable and then delete the WinDefend service.
- Terminates the MsMpEng.exe, MSASCuiL.exe, and MSASCui.exe processes.
- Adds the DisableAntiSpyware Windows policy and sets it to true to disable Windows Defender and possibly other software.
- Disables Windows Security notifications.
- Disables Windows Defender real-time protection.
Because that wasn’t enough, in a new TrickBot sample found by security researchers MalwareHunterTeam and Vitali Kremez, who reverse engineered it, it is seen that the Trojan has added further attempts to disable Windows Defender.
As you can see below, TrickBot has now added 12 additional methods to target and disable Windows Defender and Microsoft Defender APT in Windows as shown below. These methods utilize either Registry settings or the Set-Mp
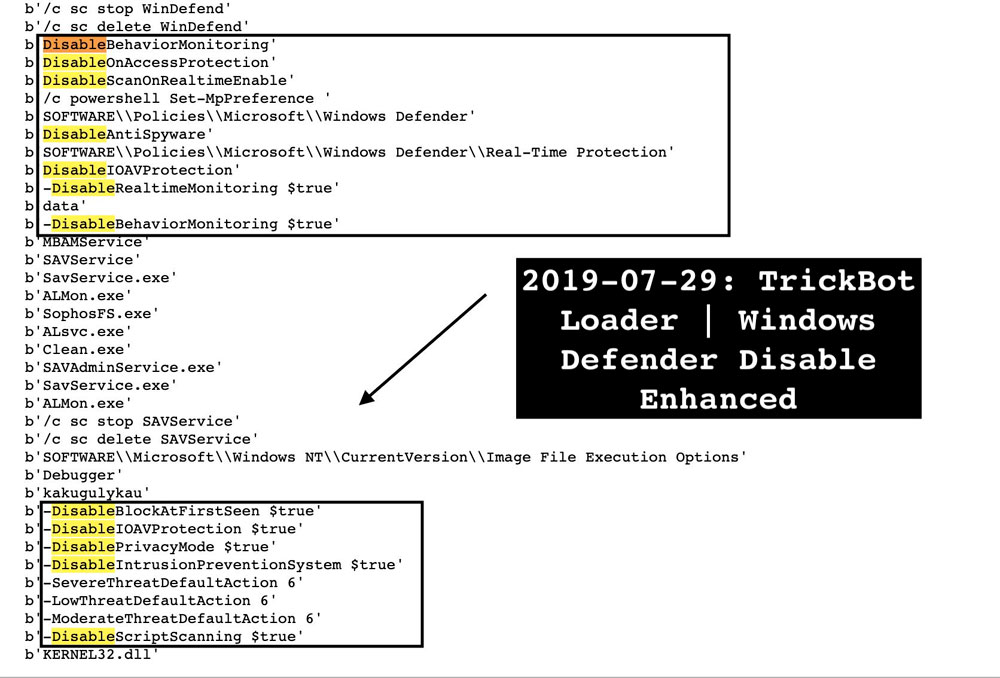
These new methods perform the following steps, with most, if not all, being blocked by TamperProtection if enabled:
- Add policies to SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection for the following:
- DisableBehaviorMonitoring: Disables behavior monitoring in Windows Defender.
- DisableOnAccessProtection: Disables scanning when you open a program or file.
- DisableScanOnRealtimeEnable: Disabled process scanning.
- Configures the following Windows Defender preferences via PowerShell:
- -DisableRealtimeMonitoring: Disables real time scanning.
- -DisableBehaviorMonitoring: Same as above, except as a Windows Defender preference.
- -DisableBlockAtFirstSeen: Disables Defender’s Cloud Protection feature.
- -DisableIOAVProtection: Disables scans of downloaded files and attachments.
- -DisablePrivacyMode: Disables privacy mode so all users can see threat history.
- -DisableIntrusionPreventionSystem: Disables network protection for known vulnerability exploits.
- -DisableScriptScanning: Disables the scanning of scripts.
- -SevereThreatDefaultAction: Set the value to 6, which turns off automatic remediation for severe threats.
- -LowThreatDefaultAction: Set the value to 6, which turns off automatic remediation for low threats.
- -ModerateThreatDefaultAction: Set the value to 6, which turns off automatic remediation for moderate threats.
When TrickBot detects certain security programs installed, it will configure a debugger for that process using the Image File Execution Options Registry key. This causes the debugger to launch before the program that is executed, and if that debugger does not exist, the expected program will fail to launch.
While not related to Windows Defender, in this version the name of the process used as the debugger has been changed to “kakugulykau”, which will cause the programs to not be able to launch.
The programs that have an IFEO debugger configured are:
MBAMService
SAVService
SavService.exe
ALMon.exe
SophosFS.exe
ALsvc.exe
Clean.exe
SAVAdminService.exe
SavService.exe
ALMon.exe
As you can see, the developers of TrickBot are constantly monitoring for new tricks and methods to bypass security and keep researchers on their toes and we should expect to see this behavior continue.
To read the original article:



