Command and control (C2) servers for the Emotet botnet appear to have resumed activity and deliver binaries once more. This comes after being inert since the beginning of June.
Although it started as a banking trojan in 2014, Emotet changed its course to becoming a botnet that delivers various malware strains.
Emotet is now one of the top threats, its infrastructure being used to distribute Trickbot, another banking trojan, and then spread the Ryuk ransomware. This combination is dubbed ‘triple threat’ and has affected public administrations in the U.S.
Emotet break is over
Researchers noticed that Emotet operators took a break at the beginning of June and correctly assumed that it would not be for long. No new campaigns were observed since then, and the general consensus in the infosec community was that the servers were down for maintenance.
The botnet’s C2 infrastructure revived a couple of days ago, at 3PM EST, Cofense Labs noticed.
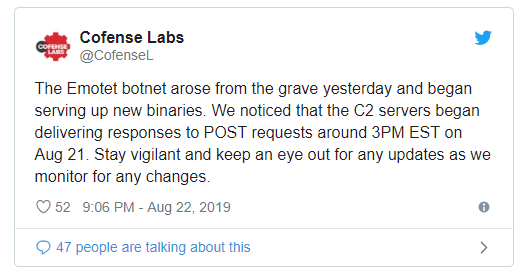
A list of servers seen to be active is available here and at the end of the article, seen online by Black Lotus Labs on August 22. Malware analysts are already tracking them.
According to MaxMind geo-IP service, the addresses are from the U.S., Hungary, France, Germany, India, Belgium, Poland, Mexico, Argentina, and Australia.
Security researcher MalwareTech noticed the new activity and says that there he did not record new bot binaries until now, just fresh activity from the servers.
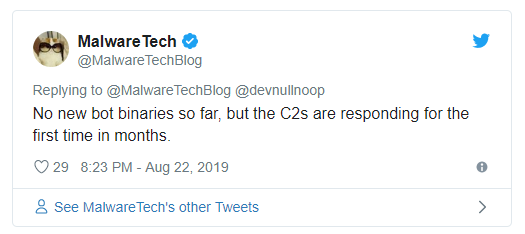
Joseph Roosen, part of the Cryptolaemus Team tracking Emotet activity confirmed that the botnet does not spew new binaries at the time being. The reason is that resuming operations requires time to rebuild the botnet, clean it of bots from security researchers, and prepare the spam campaigns.4
[…]
To read the original article:



