Cybersecurity researchers have discovered over 80 Magecart compromised e-commerce websites that were actively sending credit card information of online shoppers to the attackers-controlled servers.
Operating their businesses in the United States, Canada, Europe, Latin America, and Asia, many of these compromised websites are reputable brands in the motorsports industry and high fashion, researchers at Aite Group and Arxan Technologies revealed today in a report shared with The Hacker News.
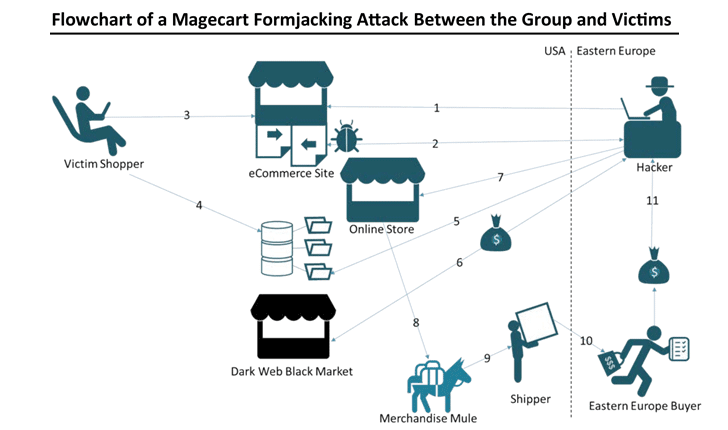
In a world that’s growing increasingly digital, Magecart attacks have emerged as a key cybersecurity threat to e-commerce websites.
Magecart is an umbrella term given to different cybercriminal groups that are specialized in secretly implanting online credit card skimmers on compromised e-commerce websites with an intent to steal payment card details of their customers.
These virtual credit card skimmers, also known as formjacking attack, are basically JavaScript code that hackers secretly insert into a compromised website, often on the shopping cart page, designed to capture payment information of customers in real-time and send it to a remote attacker-controlled server.
Magecart is in the news a lot lately for conducting several high-profile heists against major companies including British Airways, Ticketmaster, Newegg, and others.
The newly disclosed campaign doesn’t belong to a single group of Magecart hackers; instead, researchers used a source code search engine to search for obfuscated JavaScript on the Internet with malicious patterns that were previously seen in the Magecart’s virtual credit card skimmers.
According to the researchers, the technique allowed them to quickly uncover more than 80 e-commerce websites compromised by Magecart groups, most of which were found running over outdated versions of Magento CMS that’s vulnerable to an unauthenticated upload and remote code execution vulnerabilities.
“The absence of in-app protection, such as code obfuscation and tamper detection, makes web apps vulnerable to a type of cyberattack called formjacking,” the researchers said.
“Many of the compromised sites are running version 1.5, 1.7, or 1.9. The arbitrary file upload, remote code execution, and cross-site request forgery vulnerabilities all affect Magento version 2.1.6 and below. While it can’t be stated authoritatively that this is what led to the breach of these sites, these are vulnerable versions of Magento that allow adversaries to inject the formjacking code into the site.”
Though the researchers have not named the compromised companies in its report, they worked with federal law enforcement to notify all affected organizations as well as off-site servers prior to publishing their report.
[…]
To read the original article:
https://thehackernews.com/2019/08/magecart-hacking-credit-card.html