The cybercriminals behind BRATA use few infection vectors. For example, they use push notifications on compromised websites; and also spread it using messages delivered via WhatsApp or SMS, and sponsored links in Google searches.
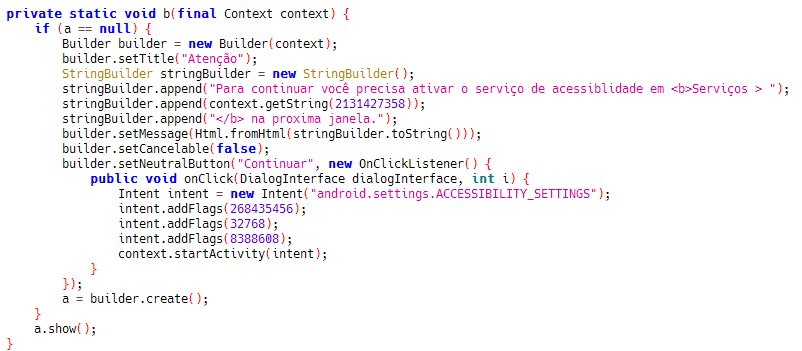
The first samples we found in the wild date to January and February 2019, while so far over 20 different variants have appeared in the Google Play Store, the majority of these pose as an update to the popular instant messaging application WhatsApp. The CVE-2019-3568 WhatsApp patch is one of the topics abused by BRATA threat actor. Once a victim’s device is infected, “BRATA” enables its keylogging feature, enhancing it with real-time streaming functionality. It uses Android’s Accessibility Service feature to interact with other applications installed on the user’s device.
| COMMAND | DESCRIPTION |
| Start/Stop Streaming | Capture and send user’s screen output in real-time. |
| Turn Off/Fake Turn Off | Can be used to turn off the screen or give the user the impression that the screen is off while performing actions in the background. |
| Device Information | Retrieves Android system information, logged user and their registered Google accounts, but missing permissions to properly execute the malware, and hardware information. |
| Request Unlock/Unlock Device | Request the user to unlock the device or perform a remote unlock. |
| Start Activity | Launch any application installed with a set of parameters sent via a JSON data file. |
| Send Text | Send a string of text to input data in textboxes. |
| Launch/Uninstall | Launch any particular application or uninstall the malware and remove traces of infection. |
It is worth mentioning that the infamous fake WhatsApp update registered over 10,000 downloads in the official Google Play Store, reaching up to 500 victims per day.
Kaspersky products detect this family as “HEUR:Backdoor.AndroidOS.Brata”
In general, we always recommend carefully review permissions any app is requesting on the device. It is also essential to install an excellent up-to-date anti-malware solution with real-time protection enabled.
Reference md5 hashes:
- 1d8cf2c9c12bf82bf3618becfec34ff7
- 4203e31024d009c55cb8b1d7a4e28064
- 4b99fb9de0e31004525f99c8a8ea6e46
To read the original article: https://securelist.com/spying-android-rat-from-brazil-brata/92775/