Users of utilities that reclaim disk space should think twice if someone tries to get them to download BleachBit. Cybercriminals have created a web page that purports to be the official website of the tool, but instead spreads the AZORult information stealer.
BleachBit is a tool that can help Windows, Linux, and macOS users reclaim disk space by deleting disposable data. It has over one million downloads on Sourceforge since its original release and is also available straight from the developer’s website.
AZORult is a longstanding info stealer selling for about $100 on Russian underground forums. It can collect various types of sensitive data from an infected computer such as browser history, saved logins, stored credentials in FTP clients, desktop and text files, and more.
Clean-looking impersonation
When designing the site, the bad actors paid attention to the general details and used the domain bleachbitcleaner[.]com – last updated on August 27 – in order to fool a lot of users into thinking it is the legitimate home of the utility.
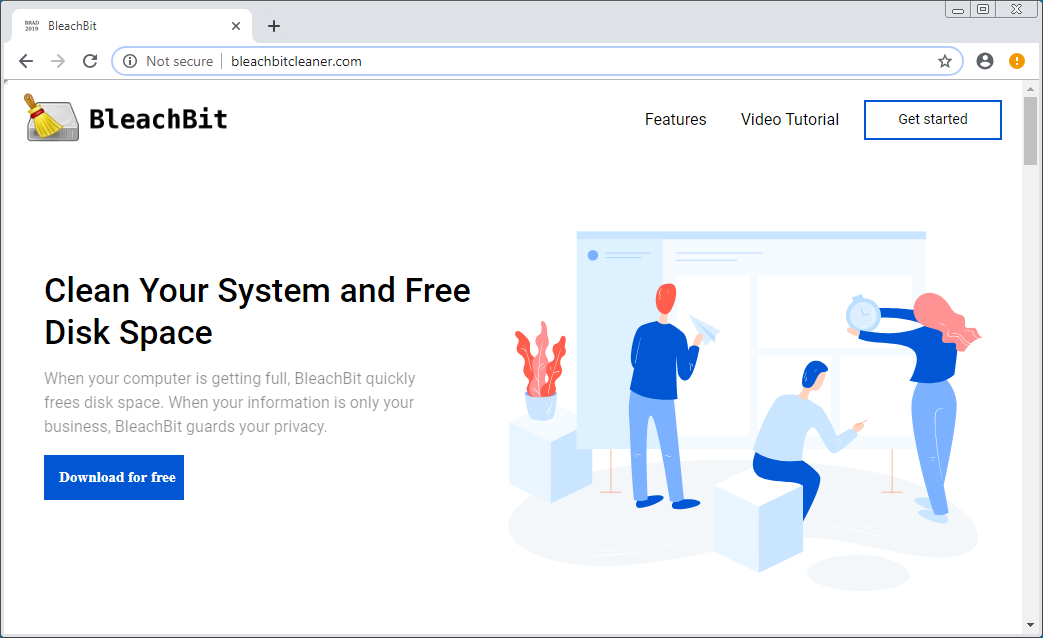
They also created a webpage that looks appealing enough, despite having only one link available, the one leading to AZORult. This, along with the embedded video tutorial for a beta version of the program released in 2009, should ring some alarm bells.
Security researcher Benkow made the discovery and followed the payload trail to the Dropbox file sharing platform.
He also tracked the server that received the data taken from infected computers to twooo[.]cn.
The binary of the malicious doppelgänger may have the same name as the original file but lacks the official icon.
Uploading stolen data
Once installed, AZORult contacts its command and control (C2) server for instructions. It can collect browser history, login credentials, cookies, and files in specific locations.
Users falling for the trick will download a ZIP archive from Dropbox and when launched will automatically harvest a victim’s data and upload it to the attacker’s command and control servers.
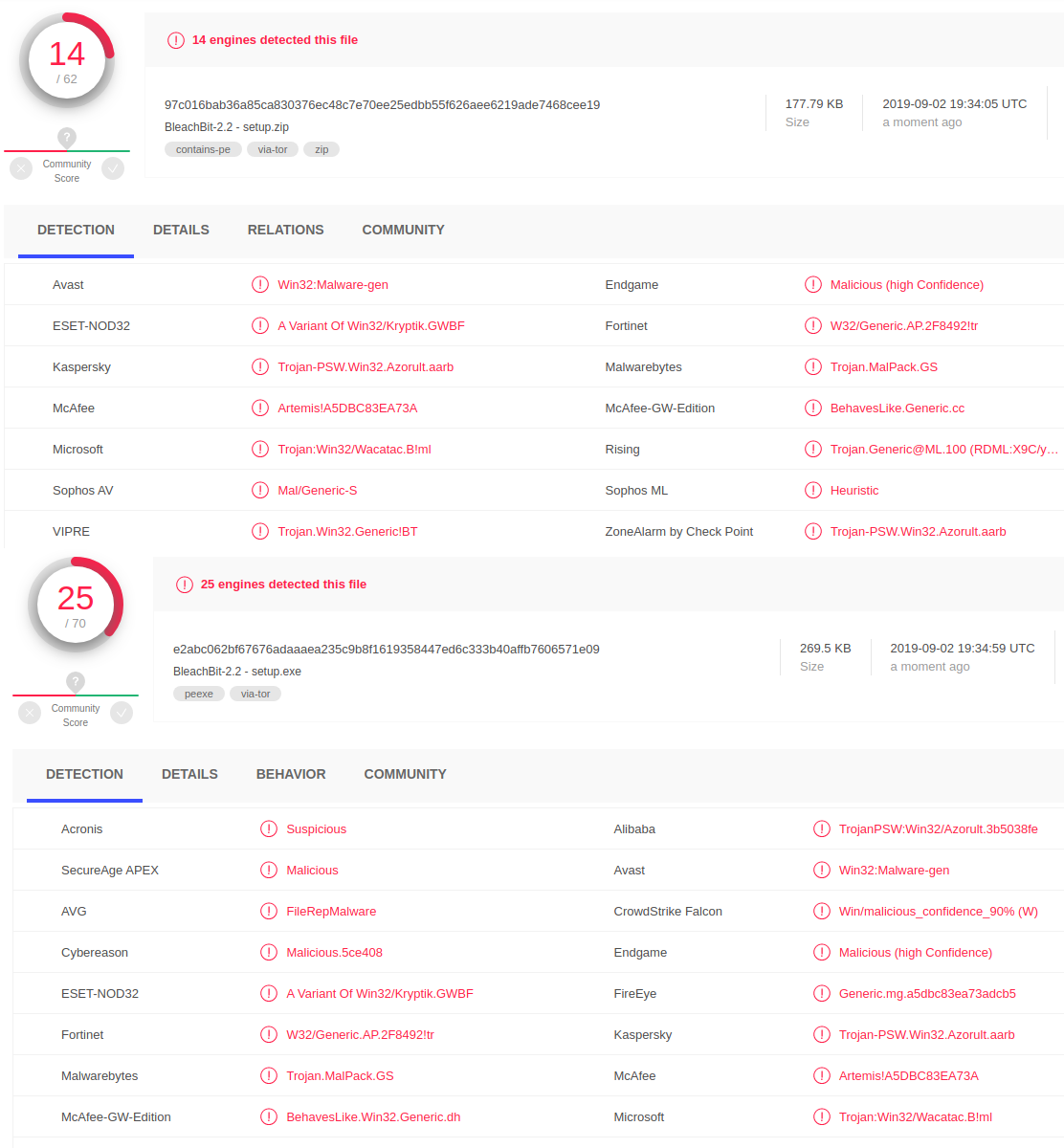
Both the ZIP archive and the executable are picked up by various antivirus engines on the VirusTotal scanning platform. The detection rate is not high though; the container was flagged by 14 products while the binary was identified by 25.
It is unclear how crooks direct victims to the fake website. Given BleachBit’s profile, though, the attacker might hope it ranks well in search engines or manually push the fake website on support forums or to users looking to securely erase sensitive data.



