The world of connected consumer electronics, IoT, and smart devices is growing faster than ever with tens of billions of connected devices streaming and sharing data wirelessly over the Internet, but how secure is it?
As we connect everything from coffee maker to front-door locks and cars to the Internet, we’re creating more potential—and possibly more dangerous—ways for hackers to wreak havoc.
Believe me, there are over 100 ways a hacker can ruin your life just by compromising your wireless router—a device that controls the traffic between your local network and the Internet, threatening the security and privacy of a wide range of wireless devices, from computers and phones to IP Cameras, smart TVs and connected appliances.
In its latest study titled “SOHOpelessly Broken 2.0,” Independent Security Evaluators (ISE) discovered a total of 125 different security vulnerabilities across 13 small office/home office (SOHO) routers and Network Attached Storage (NAS) devices, likely affecting millions.
“Today, we show that security controls put in place by device manufacturers are insufficient against attacks carried out by remote adversaries. This research project aimed to uncover and leverage new techniques to circumvent these new security controls in embedded devices,” the researchers said.
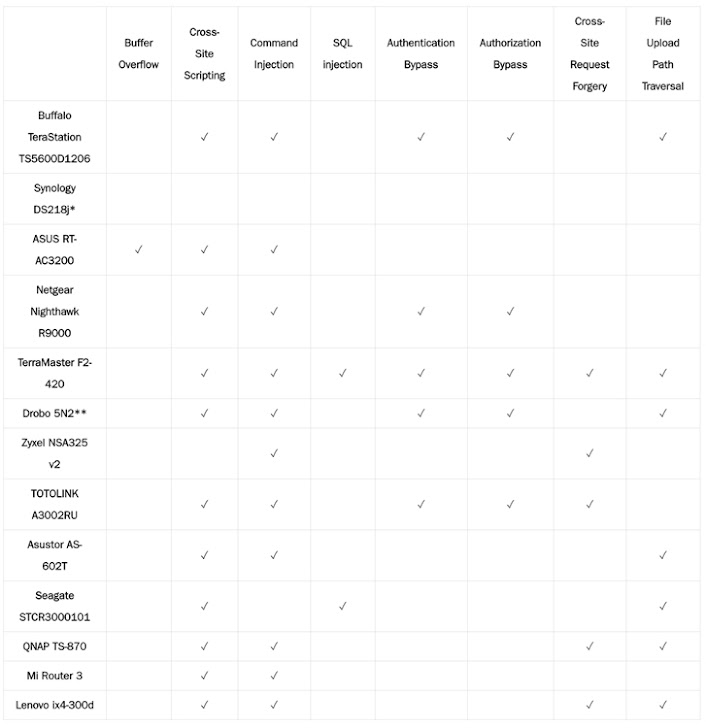
List of Affected Router Vendors
SOHO routers and NAS devices tested by the researchers are from the following manufacturers:
- Buffalo
- Synology
- TerraMaster
- Zyxel
- Drobo
- ASUS and its subsidiary Asustor
- Seagate
- QNAP
- Lenovo
- Netgear
- Xiaomi
- Zioncom (TOTOLINK)
According to the security researchers, all of these 13 widely-used devices they tested had at least one web application vulnerability that could allow a remote attacker to gain remote shell access or access to the administrative panel of the affected device.
These vulnerabilities range from cross-site scripting (XSS), cross-site request forgery (CSRF), buffer overflow, operating system command injection (OS CMDi), authentication bypass, SQL injection (SQLi), and file upload path traversal vulnerabilities.
Full Control Over Devices Without Authentication
Researchers said they successfully obtained root shells on 12 of the devices, allowing them to have complete control over the affected devices, 6 of which contained flaws that would enable attackers to gain full control over a device remotely and without authentication.
These affected business and home routers are Asustor AS-602T, Buffalo TeraStation TS5600D1206, TerraMaster F2-420, Drobo 5N2, Netgear Nighthawk R9000, and TOTOLINK A3002RU.
This new report, SOHOpelessly Broken 2.0, is a follow-up study, SOHOpelessly Broken 1.0, published by the ISE security firm in 2013, when they disclosed a total of 52 vulnerabilities in 13 SOHO routers and NAS devices from vendors including TP-Link, ASUS, and Linksys.
Since SOHOpelessly Broken 1.0, researchers said they found a few newer IoT devices implementing some useful security mechanisms in place, like address-space layout randomization (ASLR), functionalities that hinder reverse engineering, and integrity verification mechanisms for HTTP requests.
However, some things have not changed since SOHOpelessly Broken 1.0, like many IoT devices still lack basic web application protection features, like anti-CSRF tokens and browser security headers, which can greatly enhance the security posture of web applications and the underlying systems they interact with.
ISE researchers responsibly reported all of the vulnerabilities they discovered to affected device manufacturers, most of which promptly responded and already took security measures to mitigate these vulnerabilities, which have already received CVE Ids.
However, some device manufacturers, including Drobo, Buffalo Americas, and Zioncom Holdings, did not respond to the researchers’ findings.
To read the original article: