The Emotet botnet has switched to a new template used by malicious attachments that pretend to be a Microsoft Office Activation Wizard.
When conducting spam campaigns, the actors behind Emotet will use malicious Word document templates that are designed to trick recipients into enabling macros in the document. Once these macros are enabled, a script will be executed that downloads and installs the Emotet Trojan and possibly other malware onto the recipient’s computer.
While the spam emails are still using a mix of reply-chain and direct emails pretending to be fake invoices, order confirmations, payment confirmations, and shipping issues, they have now switched to a new document template that pretends to be a Microsoft Office Activation Wizard.
Discovered by security researcher ps66uk, this new template prompts the victim to click on the Enable Editing and Enable Content buttons in order to complete the activation of Microsoft Office.
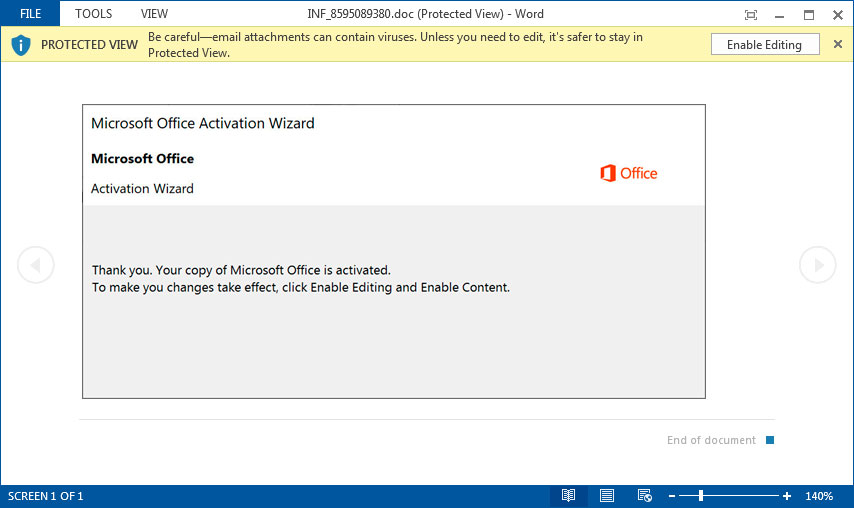
Ps66uk has told BleepingComputer that this is the first time the researcher has seen this particular document template being used by Emotet.
Once the user clicks the Enable Editing and Enable Content buttons, embedded macros will launch a PowerShell command that connects to a remote site, downloads the Emotet Trojan to the victim’s %UserProfile%, and executes it.
Once infected, the Emotet Trojan will send out further spam emails to the victim’s contact lists and will also download other malware onto the computer.
Protecting yourself from malicious attachments
When the Emotet botnet sends out spam emails, they will appear to be from senders you know and will sometimes act as replies to existing emails that you were involved in.
Therefore, it makes sense that a recipient would think that an email is legitimate and thus it’s ok to open the attachment.
Unfortunately, replay-chain attacks as described above make it difficult to trust any attachments you receive.
Due to this, I suggest that when you receive an attachment via email, you call the sender directly to confirm that they actually sent it. Otherwise, you should not open it.



