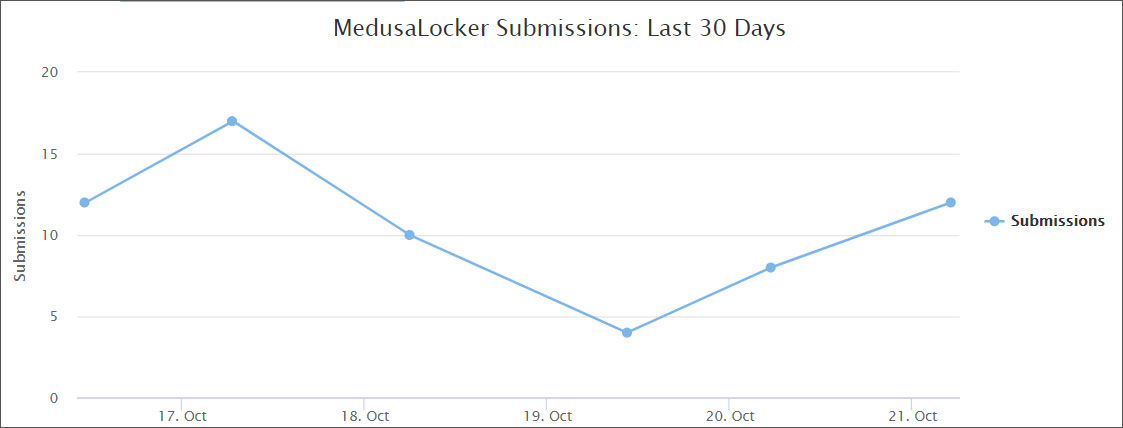
A new ransomware called MedusaLocker is being actively distributed and victims have been seen from all over the world. It is not known at this time, how the attacker is distributing the ransomware.
This new ransomware was found by MalwareHunterTeam at the end of September 2019, and while it is not currently known how the ransomware is being distributed, there has been a steady amount of submissions to the ID Ransomware site since then.
When the ransomware is installed, it will perform various startup routines in order to prep the computer for encryption.
It will create the Registry value EnableLinkedConnections under the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System registry key and set it to 1. This is done to make sure mapped drives are accessible even in a UAC launched process.
It will also restart the LanmanWorkstation service in order to make sure that Windows networking is running and that mapped network drives are accessible.
It will then look for and terminate the following processes in order to shut down security programs and to make sure all data files are closed and accessible for encrypting:
wrapper, DefWatch, ccEvtMgr, ccSetMgr, SavRoam, sqlservr, sqlagent, sqladhlp, Culserver, RTVscan, sqlbrowser, SQLADHLP, QBIDPService, Intuit.QuickBooks.FCS, QBCFMonitorService, sqlwriter, msmdsrv, tomcat6, zhudongfangyu, SQLADHLP, vmware-usbarbitator64, vmware-converter, dbsrv12, dbeng8
wxServer.exe, wxServerView, sqlservr.exe, sqlmangr.exe, RAgui.exe, supervise.exe, Culture.exe, RTVscan.exe, Defwatch.exe, sqlbrowser.exe, winword.exe, QBW32.exe, QBDBMgr.exe, qbupdate.exe, QBCFMonitorService.exe, axlbridge.exe, QBIDPService.exe, httpd.exe, fdlauncher.exe, MsDtSrvr.exe, tomcat6.exe, java.exe, 360se.exe, 360doctor.exe, wdswfsafe.exe, fdlauncher.exe, fdhost.exe, GDscan.exe, ZhuDongFangYu.exe
Finally, it clears the Shadow Volume Copies so that they cannot be used to restore files, removes backups made with Windows backup, and disables the Windows automatic startup repair using the following commands:
vssadmin.exe Delete Shadows /All /Quiet
wmic.exe SHADOWCOPY /nointeractive
bcdedit.exe /set {default} recoveryenabled No
bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
wbadmin DELETE SYSTEMSTATEBACKUP
wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest
MedusaLocker will now begin to scan the computer’s drives for files to encrypt. When encrypting files, it will skip all files that have the extensions .exe, .dll, .sys, .ini, .lnk, .rdp, .encrypted (or other extension used for encrypted files) as well as files in the following folders.
USERPROFILE
PROGRAMFILES(x86)
ProgramData
\AppData
WINDIR
\Application Data
\Program Files
\Users\All Users
\Windows
\intel
\nvidia
When encrypting files, it will use AES encryption to encrypt the file and then the AES key will be encrypted by a RSA-2048 public key included in the ransomware executable.
For each file that is encrypted, it will append one of the following extensions depending on the variant of the ransomware.
.encrypted, .bomber, .boroff, .breakingbad, .locker16, .newlock, .nlocker, .skynet
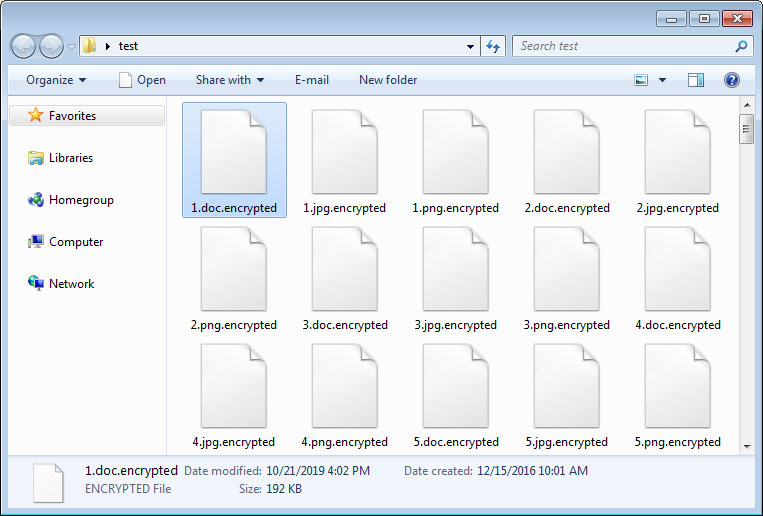
When done, the ransomware will sleep for 60 seconds and then scan the drives again for new files to encrypt.
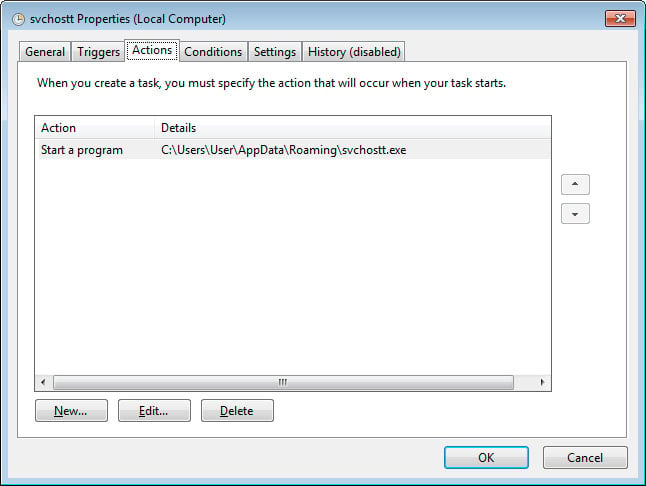
When installed, this ransomware will also copy itself to %UserProfile%\AppData\Roaming\svchostt.exe and create a scheduled task that launches the program every 30 minutes in order to remain resident.
In each folder that a file is encrypted, MedusaLocker will create a ransom note named HOW_TO_RECOVER_DATA.html or Readme.html that contains two email addresses to contact for payment instructions.
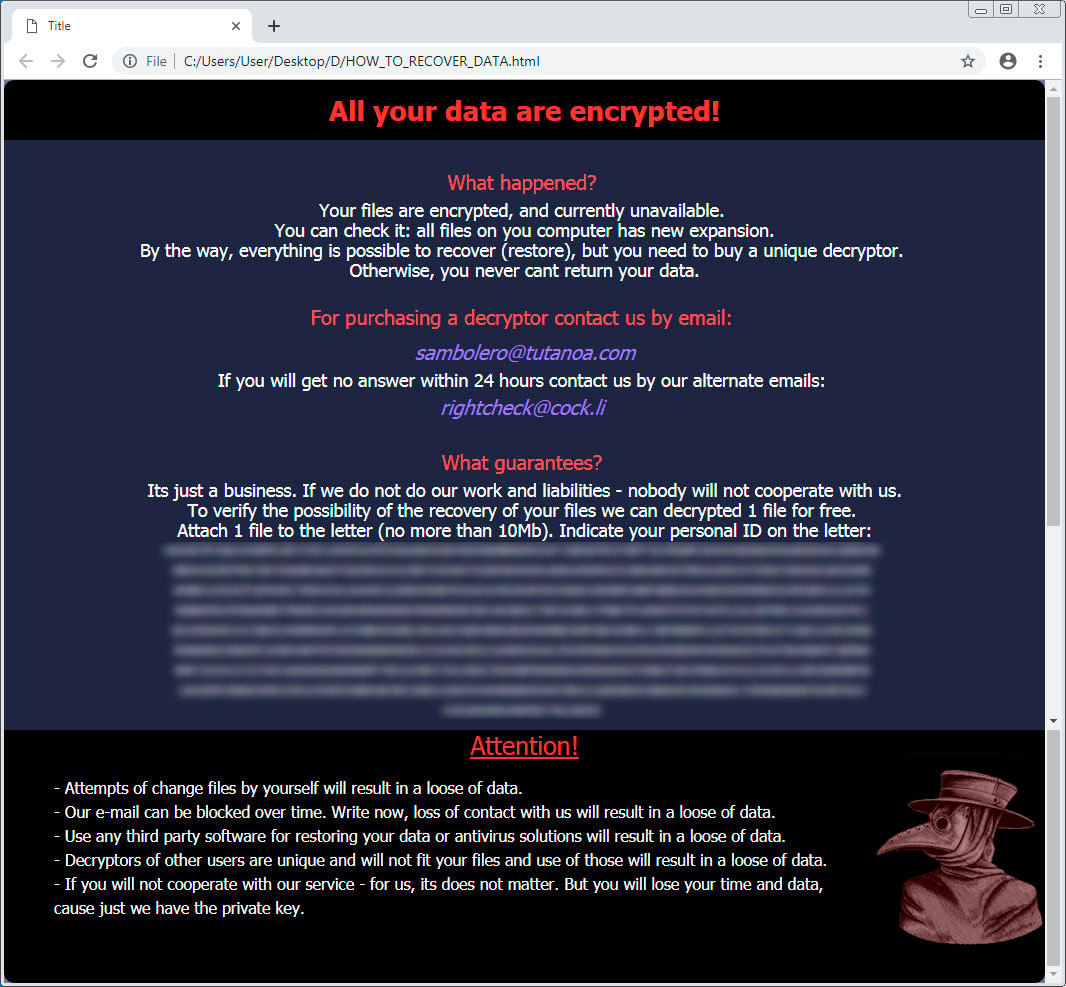
It is not known at this time how much the attackers are demanding for a decryptor or if they actually provide one after paying.
To read the original article:



