A new phishing campaign is actively targeting Microsoft Office 365 administrators with the end goal of compromising their entire domain and using newly created accounts on the domain to deliver future phishing emails.
The attackers use phishing emails designed to look like they are coming from Microsoft, with the Office 365 logo shown at the top, and delivered using “validated domains” “from a legitimate organization’s Office 365 infrastructure” as PhishLabs found.
They also use “Services admin center” as the sender name for the phishing messages delivered through this ongoing campaign as an attempt to spoof the legitimate Microsoft 365 admin center support team, and “Action Required” or “We placed a hold on your account” subjects to persuade their targets to act first and think later.
With the help of this tactic, the threat actors take advantage of a common email filtering solution feature that uses the sender domain’s reputation to decide if an email should be blocked or not.
“Well established domains with a track record of sending benign messages are less likely to be quickly blocked by these systems,” PhishLabs says. “This increases the deliverability and efficiency of phishing lures.”
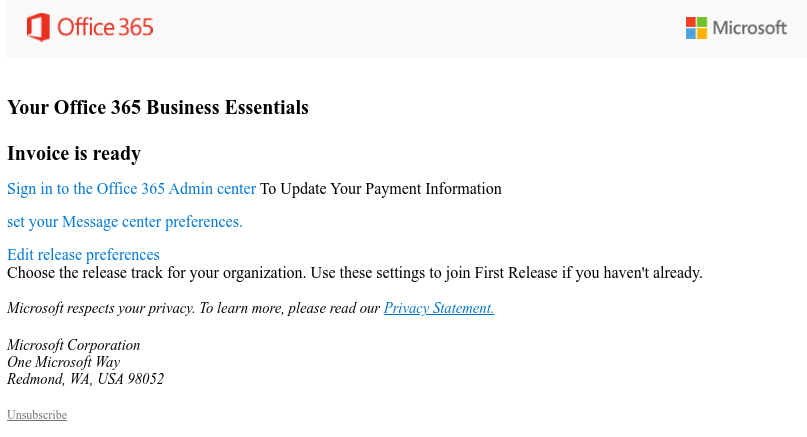
The phishing emails ask the targets to sign into their account on the Office 365 Admin center to update their payment information, and it even has links to Microsoft’s privacy statement and an unsubscribe option at the bottom of the message.
Admins are also invited to choose the release track for their org and use the settings to join “First Release” if they haven’t done it already.
Once they click the sign-in link embedded in the phishing email, the targets are sent to a fake Microsoft login page that requires them to enter their email or phone to proceed.
The attackers used accounts they created on previously compromised Office 365 domains for sending the phishing messages, this strategy allowing them to both evade detection by secure email gateways (SEGs) and avoid being spotted while maintaining their presence on a legitimate org’s domain.
Using a freshly created Office 365 account, makes it possible for them to go about their business without having to worry that the other users can spot their malicious activity “either by observing outgoing mail or receiving automated responses from failed delivery attempts.”
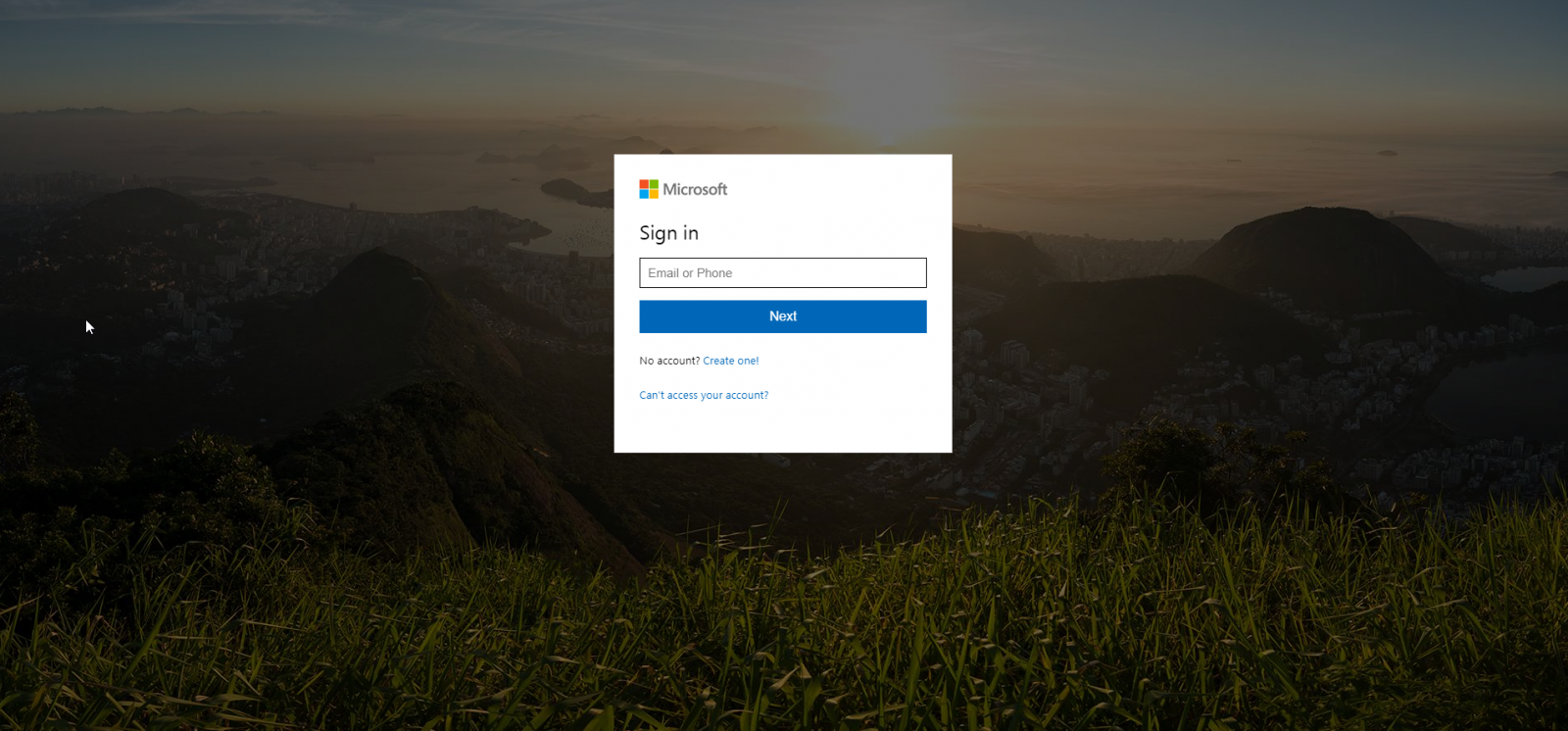
Having already used compromised Office 365 domains to spread their phishing scam to more targets hints at the possibility that any domains they manage to infiltrate using this method will also be utilized to launch new attacks, abusing the identity of the successfully compromised organization to spoof future spam messages.
To read the original article:



