A payment service platform’s checkout page was recently cloned by the threat actors behind a web skimming campaign that harvested and stole credit card information from an online shop’s customers.
Web skimming (also known as e-skimming) is the process through which fraudsters can harvest and steal customers’ payment or personally identifiable information (PII) after injecting malicious code in the form of payment card skimmer scripts within a compromised e-commerce site’s payment processing platform (PSP).
The e-skimming campaign observed by Malwarebytes Director of Threat Intelligence Jérôme Segura didn’t bother with trying to scrape the info entered by buyers into the store’s forms but went straight to the PSP, effectively replacing its checkout page with a cloned one to intercept and collect the shoppers’ credit card data.
This makes this attack a hybrid between skimming and phishing operations since the attackers didn’t just limit their attacks to the store’s PSP to harvest financial info but effectively phished it out of the virtual hands of their targets using an external PSP’s cloned checkout page.
Cloned payment pages
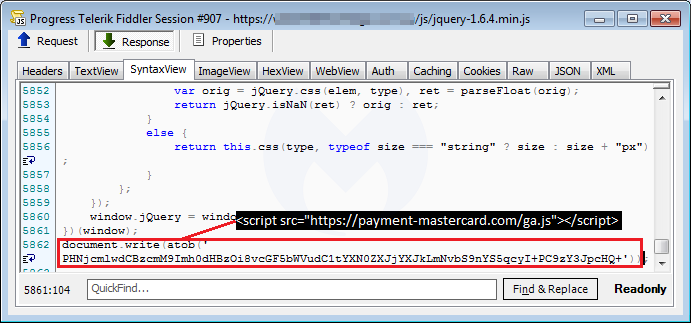
To do this, this campaign’s operators load their payment card data skimmer from payment-mastercard[.]com/ga.js, camouflaged it as a Google Analytics library.
The ga.js file is injected within the web store they managed to preciously infiltrate “by inserting a one-line piece of code containing the remote script in Base64 encoded form.”
The fake checkout page displayed by the skimmer is very similar to a phishing landing page since given that it is a cloned payment page template from CommWeb, a Commonwealth Bankpayments acceptance service.
However, like the text displayed on the payment info on the skimmer page states, the “details will be sent to and processed by The Commonwealth Bank of Australia and will not be disclosed to the merchant,” effectively making a phishing page designed specifically for harvesting and exfiltrating financial data to attacker-controlled servers.
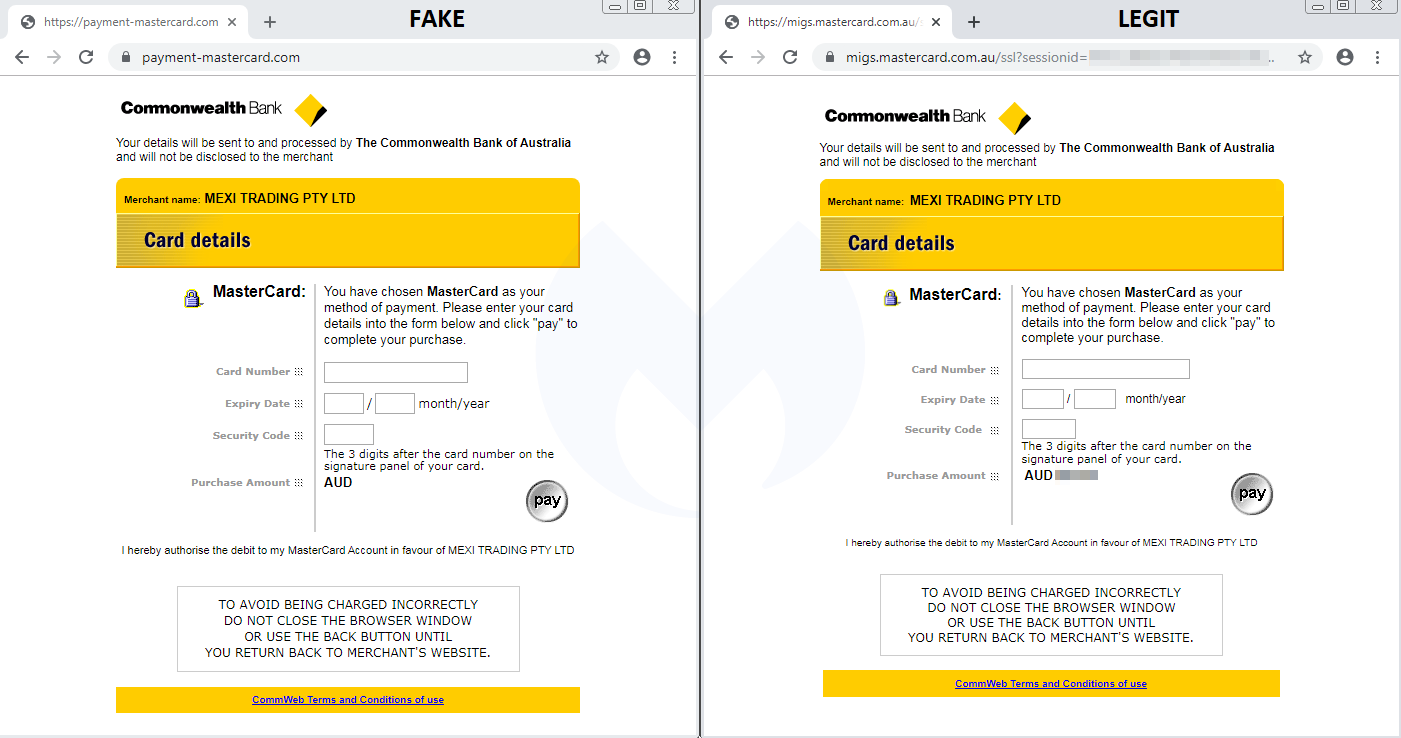
This page was specifically created by the threat actors behind this targeted e-skimming attack to go after the customers of an Australian store running a PrestaShop Content Management System (CMS) instance.
The CommWeb payment page was chosen for the phishing stage of the attack because the Commonwealth Bank was one of the accepted payment methods on the compromised online store.
The fraudsters took things a step further since, as Segura observed, they also added data validation capabilities to their phishing form, alerting their victims to enter the correct data if anything was out of order.
After the Pay button has been hit, all the validated payment card data is exfiltrated and the victims get automatically redirected to Commonwealth Bank’s legitimate PSP service, with the total amount needed to be paid being displayed and all the card data being requested again.
Escalating attacks against PSPs
This is not the first time skimmers messed around with PSPs but it never at this level, as the attackers have never created fake pages to replace legitimate PSP ones.
For instance, in May 2019, they upgraded their credit card skimming scripts to use iframes designed to phish for credit/debit card info from Magento-powered store customers.
At the time, the cybercriminals injected the card data-stealing scripts within every page of online shops they hacked and configured them to pop-up as a form that would ask the patrons to provide the info themselves.
Web skimmer groups who used phishing to steal credit card data are not revolutionary as detailed by RiskIQ’s head of threat research Yonathan Klijnsma in an analysis of Magecart Group 4’s overlay payment phishing system from February 2019, with the crooks being observed while replacing online stores’ legitimate payment forms with their own.
In related news, Macy’s announced on Monday that they suffered a data breach after their web site was hacked.
As the company said, malicious credit card skimming scripts that stole their customers’ payment info were injected in their store’s checkout and the users’ wallet page, and successfully harvested data for about a week between October 7 and October 15 when the hack was noticed.
The U.S. Federal Bureau of Investigation (FBI) also issued a warning on October 23 to increase awareness on current e-skimming threats targeting businesses and government agencies that process online payments, as well as a long list of defense tips to fend them off.
To read the original article:



