Maze Crew Reportedly Threatens to Release More of Allied Universal’s Data Unless Ransom Paid.
Ransomware attacks have taken an unwelcome turn: The Maze gang reportedly has begun leaking a victim’s files to create pressure to pay a ransom.
Security experts say that leaking data as part of a ransomware shakedown isn’t a surprising turn of events. But it’s unclear whether this tactic will catch on, they say, because simpler ransomware attacks tend to be much more lucrative than attacks that involve data exfiltration.
Even so, the group using Maze ransomware published almost 700 MB of data that it stole from Allied Universal, a California-based security services firm with a valuation of about $7 billion, Bleeping Computer reports.

The “Maze Crew” tells Bleeping Computer that the leak only represents a fraction of the 5 GB of data they stole, and that they’ll dump the rest – sending it to WikiLeaks – unless Allied Universal coughs up a ransom of 300 bitcoins, currently worth about $2.1 million.
The attackers also claim to still have access to Allied’s site and to have stolen TLS and email certificates that they could use to impersonate the security firm via email spam campaigns.
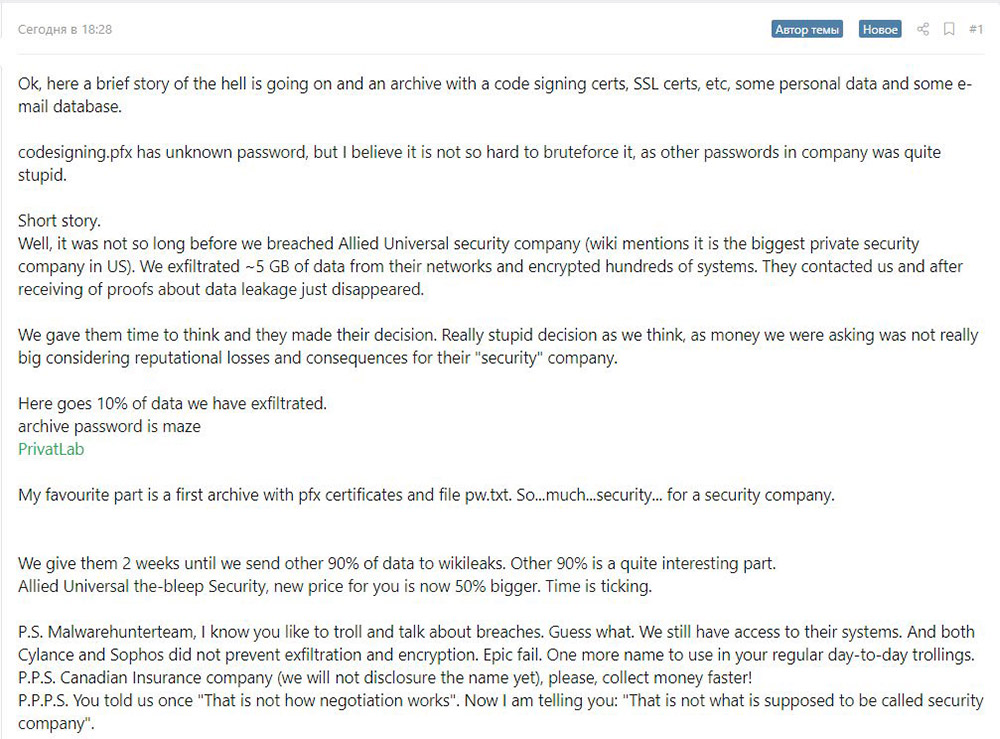 Post to a Russian hacker forum by the Maze gang about the Allied Universal intrusion (Source: Bleeping Computer)
Post to a Russian hacker forum by the Maze gang about the Allied Universal intrusion (Source: Bleeping Computer)
After attackers uploaded what it said was a sample of the stolen data to Bleeping Computer’s forums, the publication said it immediately deleted the data, but it noted that attackers had also uploaded it to a Russian language cybercrime forum and reported that they’re now demanding closer to $4 million. Allied Universal had said it would pay no more than $50,000, the publication reports.
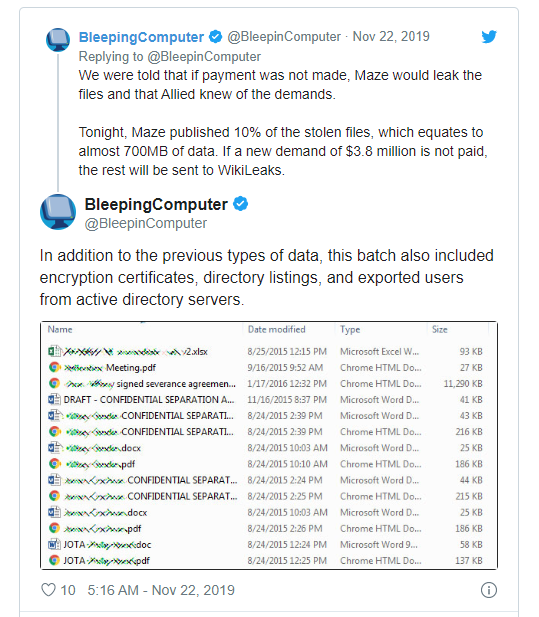
Allied Universal wasn’t immediately available for comment. But it told Bleeping Computer that its IT team, working with external information security experts, is investigating the potential “unauthorized access to our systems” and working “to mitigate any potential impact.”
Maze Ransomware
The relatively new Maze ransomware, also known as ChaCha, has been tied to a number of attacks that since October have targeted organizations in Germany, Italy and the United States. Spam emails sent by the Maze group often lead to domains that impersonate legitimate government websites – including the German Federal Ministry of Finance, the Italian Revenue Agency and the U.S. Postal Service – according to Proofpoint, which refers to the Maze gang as TA2101.
In some cases, the attackers have emailed malicious Microsoft Word attachments to victims with macros which, if run, execute a PowerShell script that downloads Cobalt Strike, a legitimate penetration testing tool that’s been repurposed by the attackers. In other cases, Proofpoint says, the malicious payload has been Maze, or, in the U.S., the IcedID banking Trojan.
In July, VMware’s Carbon Black noted that Maze was being distributed by the Fallout exploit kit. Fallout has also been tied to distributions of Sodinokibi, as well as AZORult, Kpot, Raccoon and Danabot, according to Malwarebytes (see: Sodinokibi Ransomware Gang Appears to Be Making a Killing).
In October, an independent security researcher found Maze being distributed via the Spelevo exploit kit, which was targeting a Flash vulnerability for which a patch is available.[…]
To read the original article:
https://www.bankinfosecurity.com/ransomware-attackers-leak-stolen-data-a-13438



