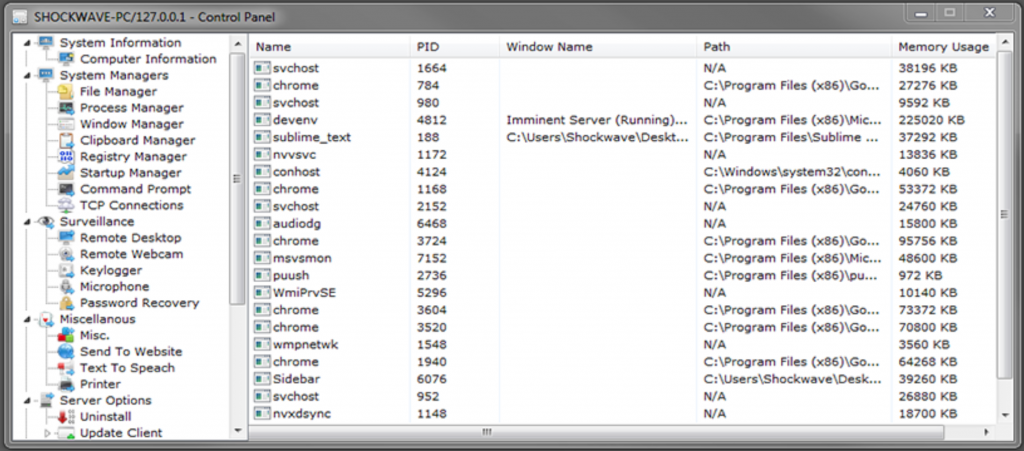
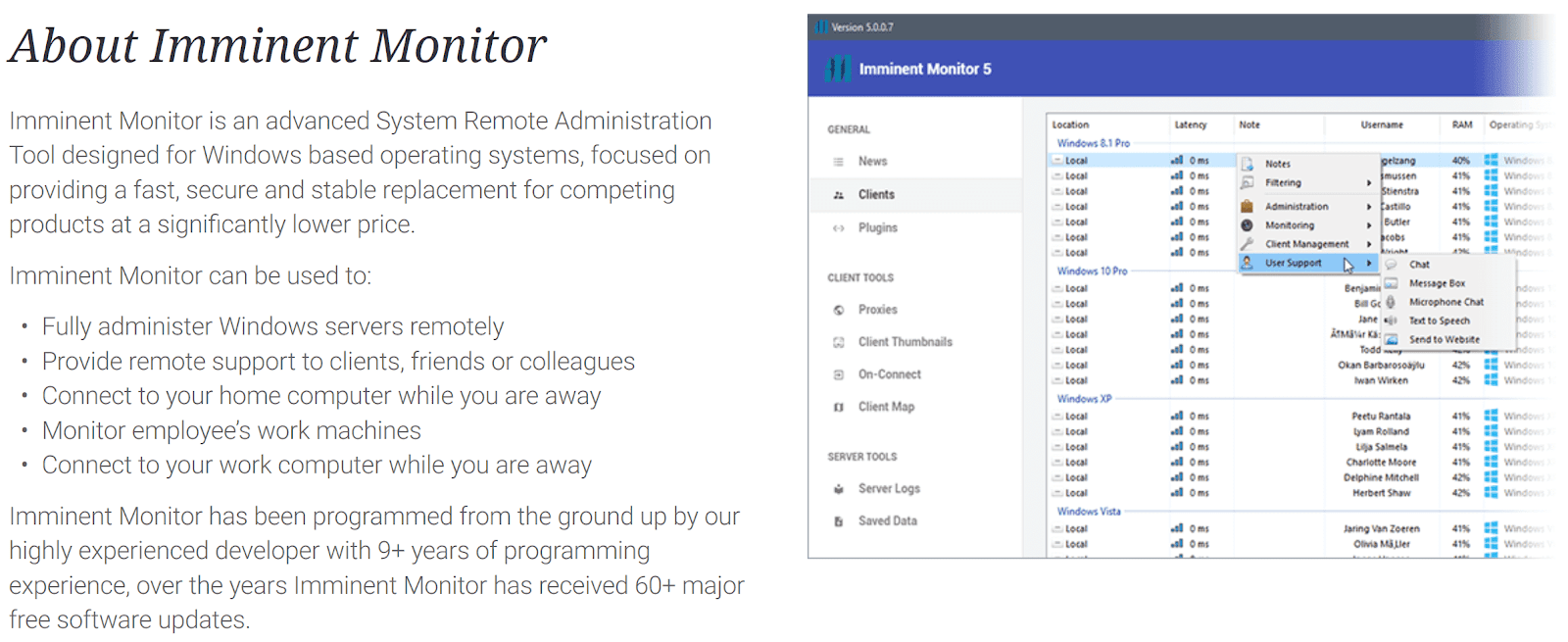
Researchers from Palo Alto Networks break down the illegitimate remote access tool “Imminent Monitor” that allows an attacker to gain full control of the Windows operating system and windows server.
There are 65,000 samples of Imminent Monitor were observed, and it’s used for more than 115,000 unique attacks, in which attackers mostly using the same samples.
The Imminent Monitor believed to be developed by Shockwave who has registered the domain imminentmethods[.]info (later “imminentmethods[.]net”) in 2012, and started selling the RAT Since 2013 via various online forums.
The developers claim that the Imminent Monitor is the fastest remote administration tool ever created using new socket technology with various sophisticated features to gain full control of the target with the following operation.
- File manager
- Process manager
- Window manager
- Clipboard manager
- Registry manager
- Startup manager
- Command prompt
- TCP connection
- Remote webcam monitoring
- Remote microphone monitoring
- Password recovery
The RAT has also supported the Third-party plugins in 2014, which added the extra feature such as the ability to turn the webcam light off while monitoring.
Shockwave, the developer who behind the RAT attempt to profess innocence and distance themselves from the illegitimate features by claiming the following,
” our tools are made for educational purpose, so we do not take any responsibility for any damage caused by any of or tools or services. Misuse of our tools or services can be very illegal. Certain misuse could cause possible jail time or fines, which differ depending on your local laws.” … “You agree that you will NOT distribute malicious files created with any of our services over the internet with the intent of harming/using machines of innocent people. “
Imminent Monitor RAT Usage & Prosecution
Researchers observed an online comment from the Shockwave stats that the tool also has a keylogger feature and ” The logs are hidden and encrypted, fast transfer of the logs as well, with progress indicating how much of the log is downloaded”
Also, they claim “ The crypter is really just a bonus feature, not always FUD but I try and do my best to keep it FUD.”
If the tool is only used for a legitimate purpose, then they to don’t need to hide and encrypt their logs, and this crypter feature will allow the attackers to bypass the Antivirus detection.
Developers behind Imminent Monitor RAT added a new feature called “protection ” in the new version included that helps avoids detection/removal.
But still, they continued to profess the legitimacy of Imminent Monitor in recent sales page they hiding the client and maintaining persistence.
Another recent version offered “HRDP” – Hidden Remote Desktop Protocol that provides a non-interactive remote desktop connection, hidden from the victim.

Imminent Monitor version 3 released with a feature that allows attackers to run a cryptocurrency miner on the victim machine, which is considering as one of the hardly the feature of a legitimate remote access tool.
According to Palo Alto network Unit 42 research ” Imminent Monitor was originally licensed to each customer for a $25 fee. Six years later, the price has remained static, though new multi-license options are also offered “

Researchers believe that the RATs employed illicitly by financially-motivated actors, or for data theft. AFP’s operation also disabled the licensing system of Imminent Monitor, removing users’ access to victims of the software.
Unit 42 reported the Shockwave malicious activities and its Imminent Monitor RAT features to Australian Federal Police (AFP) Cybercrime Operations teams and other authorities including the United States Federal Bureau of Investigation (FBI) who have investigated the development and management of this malware.
Recently Authorities take down the Imminent Monitor Remote Access Trojan (IM-RAT) that used by cybercriminals and arrested more than 13 users who involved in the development of the RAT.
To read the original article:



