Malwarebytes: Platform Used to Host Card Skimmer Infrastructure, Payment Data
Several e-commerce sites were targeted with a card skimming campaign that used the Salesforce-owned Heroku cloud platform to host skimmer infrastructure and stolen credit card data, according to a new report from the security firm Malwarebytes.
It appears that members of Magecart were using Heroku, according to a Wednesday blog post by Jérôme Segura, Malwarebytes’ director of threat intelligence. Over the last 18 months, Magecart – an umbrella organization comprising several groups, has attacked the e-commerce check-out sites of several major companies, including British Airways, Ticketmaster and Newegg
Over the past year, security firm RiskIQ has detected Magecart-linked code over 2 million times and over 18,000 domains have been breached as a result.
Four Sites Targeted
In the latest campaign, the attackers used Heroku’s free registration service to create and host skimming apps that targeted check-out and payment URLs of several online shopping websites for scrapping credit card data, Segura notes. His blog post does not identify the affected websites.
Although the researcher is unsure when the campaign began or the extent of the attack, Segura notes that several Heroku-hosted skimmers were detected in the past week. Heroku took down all the malicious installations after being notified by the Malwarebytes, Segura says.
“Threat actors are leveraging the service not only to host their skimmer infrastructure, but also to collect stolen credit card data,” Segura notes in the blog. “All instances of abuse found have already been reported to Heroku and taken down.”
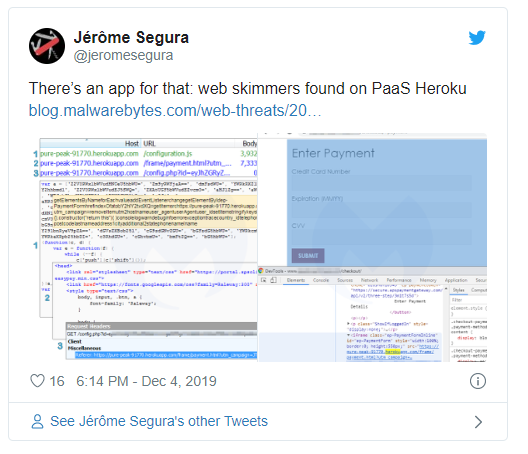
Scrapping Data Using IFrame
Skimming attacks usually start with cybercriminals injecting malicious JavaScript code into the check-out and payment pages of online retail sites to steal payment card information from customers.
In the latest Magecart campaign, according to Segura, the websites were targeted by the skimming app by injecting JavaScript code for detecting the check-out and payment URLs of the affected websites.
Next, the app injected an iFrame identical to the legitimate payment gateway, thus tricking its users to enter the payment card data, the researchers add.
Once the data has been harvested, the attackers then sent the exfiltrated data in an encrypted format to the Magecart skimmer web app for storage in Heroku, Segura notes.
“Finally, the stolen data is exfiltrated, after which victims will receive an error message instructing them to reload the page,” the researcher says in his blog. “This may be because the form needs to be repopulated properly, without the iframe this time.”
Switch in Tactics
Magecart’s use of iFrame is a relatively new skimming tactic.
In May, Malwarebytes uncovered a potential Magecart attack that targeted e-commerce websites by injecting their malicious code to steal payment card details (see: E-Commerce Skimming Attacks Evolve Into iFrame Injection).
In that case, the attackers infected an e-commerce site with code that caused it to pop up a malicious iFrame at payment time.
To read the original article:
https://www.bankinfosecurity.com/skimming-campaign-leveraged-heroku-cloud-platform-report-a-13472



