A new ransomware known as Try2Cry is trying to worm its way onto other Windows computers by infecting USB flash drives and using Windows shortcuts (LNK files) posing as the targets’ files to lure them into infecting themselves.
The Try2Cry ransomware was discovered by G DATA malware analyst Karsten Hahn when a detection signature designed to spot USB worm components got triggered while analyzing an unidentified malware sample.
Try2Cry is a .NET ransomware and another variant of the open-source Stupid ransomware family as Hann found after analyzing a sample obfuscated with the DNGuard code protection tool.
Stupid ransomware variants are commonly known to be created by less skilled malware developers and are regularly using law enforcement and pop culture themes.
Ten other Try2Cry malware samples were found by the researcher on VirusTotal while hunting down for a variant that wasn’t obfuscated to make the analysis easier, some of them also lacking the worm component.
Decryptable ransomware with a failsafe
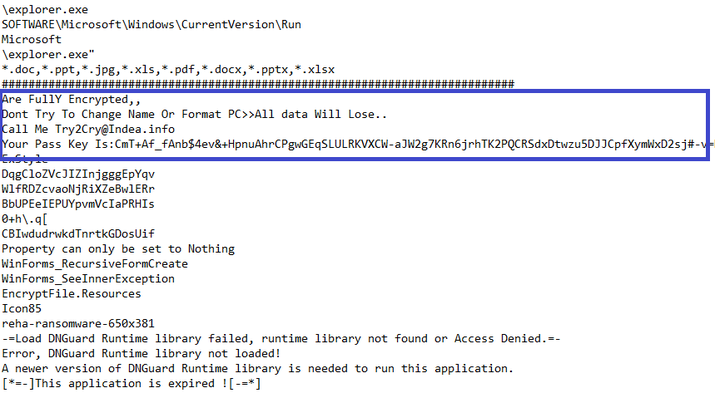
After infecting a device, Try2Cry ransomware will encrypt .doc, .ppt, .jpg, .xls, .pdf, .docx, .pptx, .xls, and .xlsx files, appending a .Try2Cry extension to all encrypted files.
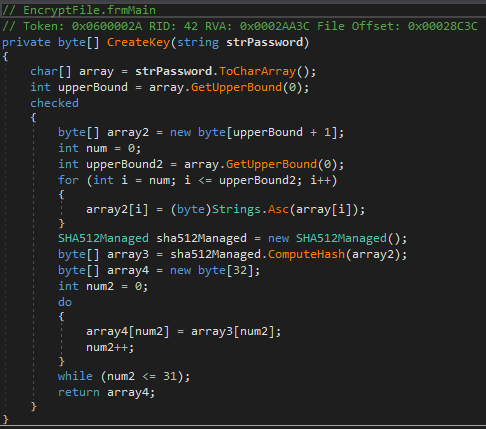
The victims’ files are encrypted using the Rijndael symmetric key encryption algorithm and a hardcoded encryption key.
“The encryption key is created by calculating a SHA512 hash of the password and using the first 32 bits of this hash,” Hahn explains.
“The IV creation is almost identical to the key, but it uses the next 16 bits (indices 32-47) of the same SHA512 hash.”
Try2Cry’s developer has also included a failsafe within the ransomware’s code designed to skip encryption on any infected systems with DESKTOP-PQ6NSM4 or IK-PC2 machine names.
This is most probably a safeguard measure designed to allow the malware’s creator to test the ransomware on his own devices without risking inadvertently locking his own files.
Worming its way through USB drives
Try2Cry’s most interesting feature is its capability to infect and attempt to spread to other potential victims’ devices via USB flash drives.
To do this it uses a similar technique to that used by the Spora ransomware and the Andromeda (Gamarue or Wauchos) botnet malware.
Try2Cry first looks for any removable drives connected to the compromised computer and it will send a copy of itself named Update.exe to the root folder of each USB flash drive it finds.
Next, it will hide all files on the removable drive and will replace them with Windows shortcuts (LNK files) with the same icon.
When clicked, all these shortcuts will open the original file and will also launch the Update.exe Try2Cry ransomware payload in the background.
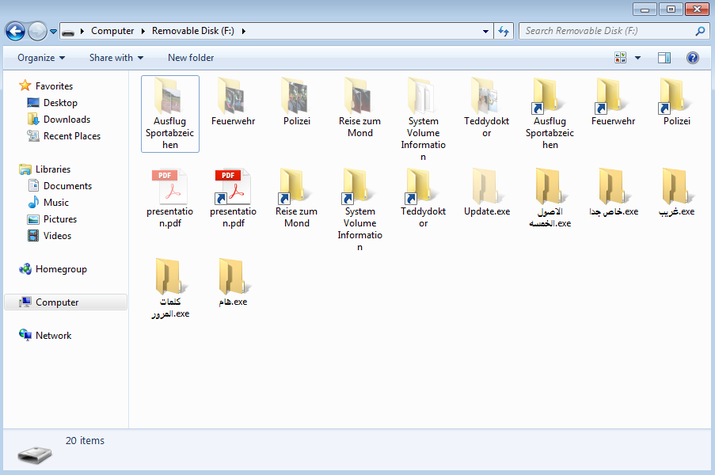
The ransomware also creates visible copies of itself on the USB drives, using the default Windows icon folder and Arabic names, in the hope that’s curious victims will click on them and infect themselves.
Unlike Spora, Try2Cry’s Windows shortcuts also feature the arrows on the side of the shortcut icons which makes it a lot easier to spot after infecting a flash drive.
The use of Arabic names is also a dead giveaway that something is not right if it infects USB devices used by targets who don’t speak Arabic.
Luckily, just as multiple other Stupid ransomware variants, Try2Cry ransomware is also decryptable, a sure sign that it was also created by someone with very little programming experience.
Thanos is yet another ransomware found to have a built-in automated spreading feature, a ransomware strain that uses the PSExec program bundled with the SharpExec offensive security toolkit to copy and launch the ransomware executable on other computers on the same network.
Just last month, a Thanos campaign targeting mid-level employees of several organizations from Germany, Austria, and Switzerland was met by the victims’ refusal to pay ransoms to have their data decrypted.
To read the original article:



