Hackers from North Korea have been stealing payment card information from customers of large retailers in the U.S. and Europe for at least a year, reveals new research released today.
The fraudulent activity, which researchers attribute to the Lazarus (Hidden Cobra) group of nation-state hackers, used legitimate websites to exfiltrate the stolen credit card data and camouflage the operation.
Stealing credit card information from customers of online stores has become a growing threat over the past years. These are known as MageCart attacks and threat actors rely on malicious scripts (web skimmers) that copy the sensitive information from the checkout page.
Exfiltration network
While investigating the payment card thefts, researchers at web security company Sansec discovered that skimmers were loaded from domains that served malware in successful spear–phishing attacks attributed to North Korean (DPRK) hacker activity, Lazarus group in particular.
This sharing of the infrastructure along with unique identifying characteristics in the code helped connect the dots and chalk up the card skimming attacks to North Korea.
The victims include accessories giant Claire’s, Wongs Jewellers, Focus Camera, Paper Source, Jit Truck Parts, CBD Armour, Microbattery, and Realchems. The list is much larger, though, and includes dozens of stores.
To cover their tracks, the attackers compromised websites of legitimate businesses to dump the stolen card information. According to Sansec’s findings, the actor hijacked sites belonging to an Italian model agency (Lux Model Agency), a bookstore in New Jersey, a vintage music store from Tehran.
Registering domain names similar to those of victim shops is another tactic that appears to bear fruits for Hidden Cobra. The image below shows the exfiltration nodes (red) that DPRK hackers used to collect payment card information from victims (green).
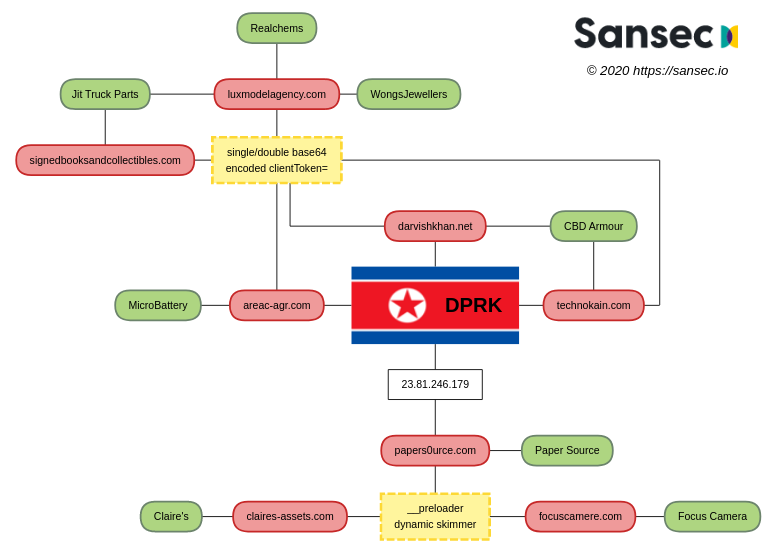
Connecting the dots
The exfiltration domains have been linked to DPRK cyber attacks by multiple cybersecurity companies. They served malware distribution following spear-phishing campaigns that occurred shortly before or after the web-skimming incidents:
- technokain.com (spearphishing operations 1, 2)
- darvishkhan.net (malspam 1, 2)
- areac-agr.com (download server for Dacls RAT)
- papers0urce.com (IP shared with areac-agr.com, hardcoded in a Dacls sample)
In one campaign discovered on June 23, 2019, a skimmer on a U.S. store for truck parts had a double-base64 encoded string for “client-token=”
“The specific encoding and the attempt to disguise the stolen payload as “clientToken” form a uniquely identifying characteristic,” Sansec notes in their report.
Initially, the exfiltration node was Lux Model Agency’s website but the malware disappeared in 24 hours and re-emerged on the same store after a week. This time though, the data went to a New Jersey bookstore.
Over the next months, the same malicious script infected several dozen stores using the following hijacked sites to load it and harvest the stolen cards:
- stefanoturco.com (between 2019-07-19 and 2019-08-10)
- technokain.com (between 2019-07-06 and 2019-07-09)
- darvishkhan.net (between 2019-05-30 and 2019-11-26)
- areac-agr.com (between 2019-05-30 and 2020-05-01)
- luxmodelagency.com (between 2019-06-23 and 2020-04-07)
- signedbooksandcollectibles.com (between 2019-07-01 and 2020-05-24)
In another campaign between February and March 2020, the hackers registered domains that can be easily confused with Claire’s, Focus Camera, and PaperSource.
Sansec later found that the sites of all three brands had been compromised with payment skimming malware and the fake domains loaded the script and collected the harvested data.
Sansec says apart from the domain registrar and DNS service, these incidents also share a “particularly odd code snippet” not seen anywhere else, tracking them to the same actor.
The researchers admit that there is a possibility these attacks could be the work of other actors, unrelated to DPRK, but the chance of simultaneous control over the same set of hijacked websites is unlikely; one reason is that these attackers typically claim the victim for themselves and close the door for other actors by patching the vulnerability that gave them initial access.
Sansec believes that DPRK has been carrying large scale digital skimming activity since at least May 2019, as an alternate means to make money.
To read the original article:



