A newly uncovered Russia-based business email compromise gang has been targeting hundreds of large, multinational corporations in over 40 countries since 2019, according to the security firm Agari.
The gang, which Agari calls Cosmic Lynx, uses a combination of social engineering techniques and well-crafted email messages designed to target the upper echelon of executives, the report notes. The researchers believe the group has conducted about 200 of these types of schemes, with some still continuing in June.
In about three-quarters of the BEC attacks it examined, Agari found that the gang targeted those with titles such as vice president, general manager or managing director.
In many cases, Cosmic Lynx targets organizations that lack security protections and authentication checks, such as the Domain-based Message Authentication, Reporting and Conformance – or DMARC. The gang often sends emails that spoof the CEO’s profile, according to the report.
Sophisticated Operation
Since at least July 2019, Cosmic Lynx fraudsters have presented themselves as representing a company based in Asia that’s working with the targeted organization to process payments for a potential acquisition.
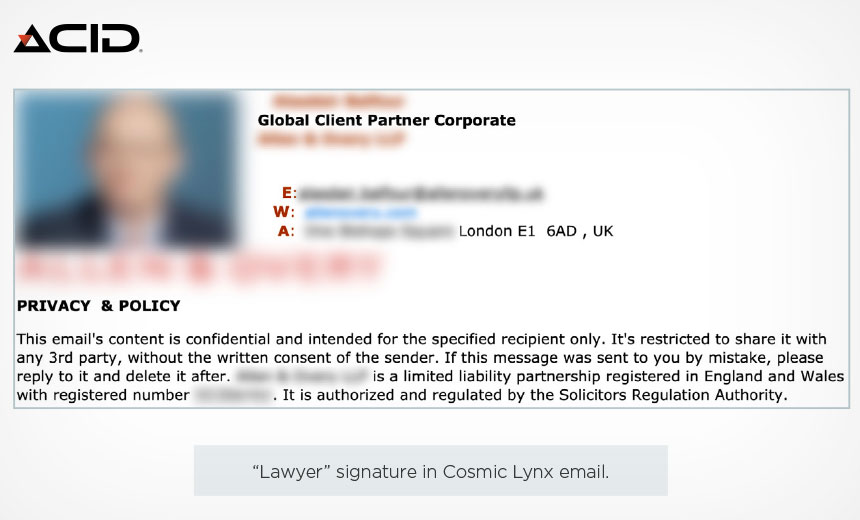
Gang members have also hijacked the identities of legitimate law firms based in the U.K., posing as “external legal counsel” working on the fictitious deal, according to the report.
The goal is to get executives of the targeted company to transfer funds to bank accounts in Hong Kong or Eastern Europe that are controlled by the criminal gang, Agari notes.
“The final stage of a Cosmic Lynx BEC attack is getting the target to send one or more payments to mule accounts controlled by the group. While the average amount requested in most executive impersonation BEC attacks is $55,000, the average Cosmic Lynx attack request is $1.27 million,” according to the report.
Due to an ongoing investigation, the Agari report did not offer specific details about companies the group has targeted, but researchers estimate that the total losses due to these BEC schemes may exceed $400 million.
Tactics
Cosmic Lynx fraudsters conduct research using commercial services to develop a list of individuals to receive their emails that impersonate other executives and begin to manipulate information, according to the report. They have devised methods for bypassing email protection tools, such as DMARC.
“For organizations that have implemented an established DMARC policy set to reject (p=reject) or quarantine (p=quarantine), Cosmic Lynx modifies the display name impersonating a CEO to include their email address, which still gives it the look that the email is coming from the CEO’s account,” Crane Hassold, senior director of threat research at Agari, notes in the report.
 Screenshot of fake attorney profile used in BEC scheme (Source: Agari)
Screenshot of fake attorney profile used in BEC scheme (Source: Agari)
The gang also sends emails from domains that are designed to look like legitimate U.K. law firms and are generally hosted on bullet-proof or anonymous domain providers, according to the report. The goal, the report notes, is to help maintain the appearance of an ongoing acquisition deal.
Russia Ties
The Agari report notes that Cosmic Lynx appears to be one of the first organized Russia-based groups to expand into BEC fraud.
Researchers identified a number of features in Cosmic Lynx’s infrastructure tying its operators to Russian actors. These include the Cosmic Lynx’s infrastructure overlapping with Trickbot and Emotet malware, which is believed to be used by Russian groups, the report notes.
“In addition to these potential connections, we have also observed multiple instances where IP addresses linked to Cosmic Lynx’s BEC domain have overlapped with infrastructure used to host Russian fake document websites,” according to the report. “These sites, which seem to be catering to individuals in Russia and Ukraine, sell a variety of false Russian-language documents such as diplomas, birth certificates and death certificates.”
Armen Najarian, chief identity officer at Agari, notes in the report: “Cosmic Lynx represents the future of organized crime rings that are shifting focus to socially engineered email fraud. The more favorable economics of socially engineered schemes targeting enterprise victims have driven groups like Cosmic Lynx to defocus on the more costly and less lucrative ransomware fraud.”
Other BEC Scams
Until now, many BEC scams were operated by gangs in Nigeria (see: Nigerian Entrepreneur Pleads Guilty in $11 Million BEC Scam).
To read the original article:
https://www.bankinfosecurity.com/russian-bec-gang-targets-hundreds-multinational-companies-a-14575



