A new and targeted ransomware named AgeLocker utilizes the ‘Age’ encryption tool created by a Google employee to encrypt victim’s files.
Yesterday, a consultant created a topic in the BleepingComputer forums about a new ransomware used in an attack against their client.
After examining the encrypted files, it was discovered that a text header was added to each file that starts with the URL ‘age-encryption.org,’ as shown below.
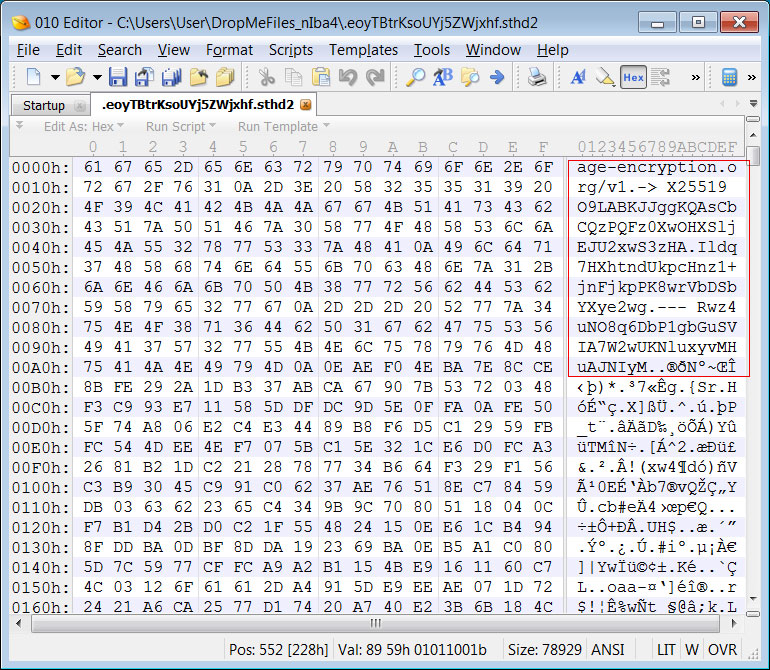
An example of the text header appended to an encrypted file is below:
age-encryption.org/v1
-> X25519 O9LABKJJggKQAsCbCQzPQFz0XwOHXSljEJU2xwS3zHA
Ildq7HXhtndUkpcHnz1+jnFjkpPK8wrVbDSbYXye2wg
--- Rwz4uNO8q6DbP1gbGuSVIA7W2wUKNluxyvMHuAJNIyM
The URL age-encryption.org brings you to a GitHub repository for an encryption utility called ‘Age’ created by Filippo Valsorda, cryptographer, and Go security lead at Google.
According to the Age manual, the utility was designed as a replacement for GPG to encrypt “files, backups, and streams.”
“This is a design for a simple file encryption CLI tool, Go library, and format.
It’s meant to replace the use of gpg for encrypting files, backups, streams, etc.
It’s called “age”, which might be an acronym for Actually Good Encryption, and it’s pronounced like the Japanese 上げ (with a hard g).”
Instead of creating a ransomware that utilizes commonly used encryption algorithms such as AES+RSA, the threat actors behind AgeLocker appear to be using the Age command line tool to encrypt a victim’s files.
Ransomware decryption expert, Michael Gillespie, told BleepingComputer that Age uses the X25519 (an ECDH curve), ChaChar20-Poly1305, and HMAC-SHA256 algorithms, which makes it a very secure method to encrypt a file.
BleepingComputer has reached out to Valsorda to see if he had any advice that can be offered to victims but has not heard back.
AgeLocker ransom note sent via email
It is not known how the threat actors are gaining access to victim’s computers, but once they gain access to the system, they utilize the Age encryption tool to encrypt the victim’s files.
While encrypting data, a custom extension created with the victim’s initials will be appended to each encrypted filename.
In a first for ransomware infections, instead of creating ransom notes on the encrypted system, the attackers emailed the ransom demand to the victim.
After the company’s devices were encrypted in the reported attack, they received an email with a subject line of “[company name] security audit.”
This ransom note listed the devices encrypted by the ransomware and instructions on how to get payment information.
Hello XXX and XXX,
Unfortunately a malware has infected your network and a millions of files has been encrypted using a hybrid encryption scheme.
File names encrypted too.
Encrypted hosts are:
Storage:
1. XXX
2. XXX
3. XXX
4. XXX
5. XXX
Mac + external drives
1. XXX?
2. XXX?
3. XXX
4. XXX
5. XXX
6. XXX
You have to pay for decryption in Bitcoins.
The price depends on how fast you write us.
After payment we will send you the tool(for mac and linux) that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption.
The total size of files must be less than 4Mb (non archived), and files should not contain valuable information. (databases, backups, large excel sheets, etc.), file name shouldn't be changed.
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
https://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Note: we can answer up to 6-9 hours, because of another timezone."According to the victim, the threat actors are asking for 7 bitcoins, or approximately $64,500, to decrypt the files.
Unfortunately, it does not appear possible to recover files encrypted by Age for free at this time.
To read the original article:
https://www.bleepingcomputer.com/news/security/new-agelocker-ransomware-uses-googlers-utility-to-encrypt-files/



