The WastedLocker ransomware is abusing a Windows memory management feature to evade detection by security software.
Before we get to how WastedLocker is evading detection, it is necessary to understand how anti-ransomware solutions detect ransomware.
Anti-ransomware solutions will monitor the operating system for file system calls traditionally used by ransomware when encrypting a file.
As part of anti-ransomware solutions, security software will register a minifilter driver that allows it to monitor the system calls that are interacting with a file system in real-time.
If this driver detects an unknown process performing many sequential operations opening a file, writing to it, and then closing the file, a behavioral detection will be triggered, and the offending process will be terminated.
This behavioral detection method essentially sacrifices a few files to detect malicious behavior and prevent the rest of the drive from being encrypted.
WastedLocker uses Windows Cache Manager
Over the past few weeks, the WastedLocker Ransomware has become notorious after being attributed to the sanctioned Evil Corp hacking group and used to attack Garmin.
In a new report shared with BleepingComputer prior to release, Sophos security researchers explain how WastedLocker uses the Windows Cache Manager to evade detection.
To increase Windows’s performance, commonly used files or files specified by an application are read into and stored in the Windows Cache, which utilizes system memory.
If a program needs to access a file, the operating system will check if it is in the cache, and if so, load it from there. As the data is cached in memory, it makes it much faster to access its contents than reading it from a disk drive.
To bypass detection by anti-ransomware solutions, WastedLocker includes a routine that opens a file, reads it into the Windows Cache Manager, and then closes the original file.
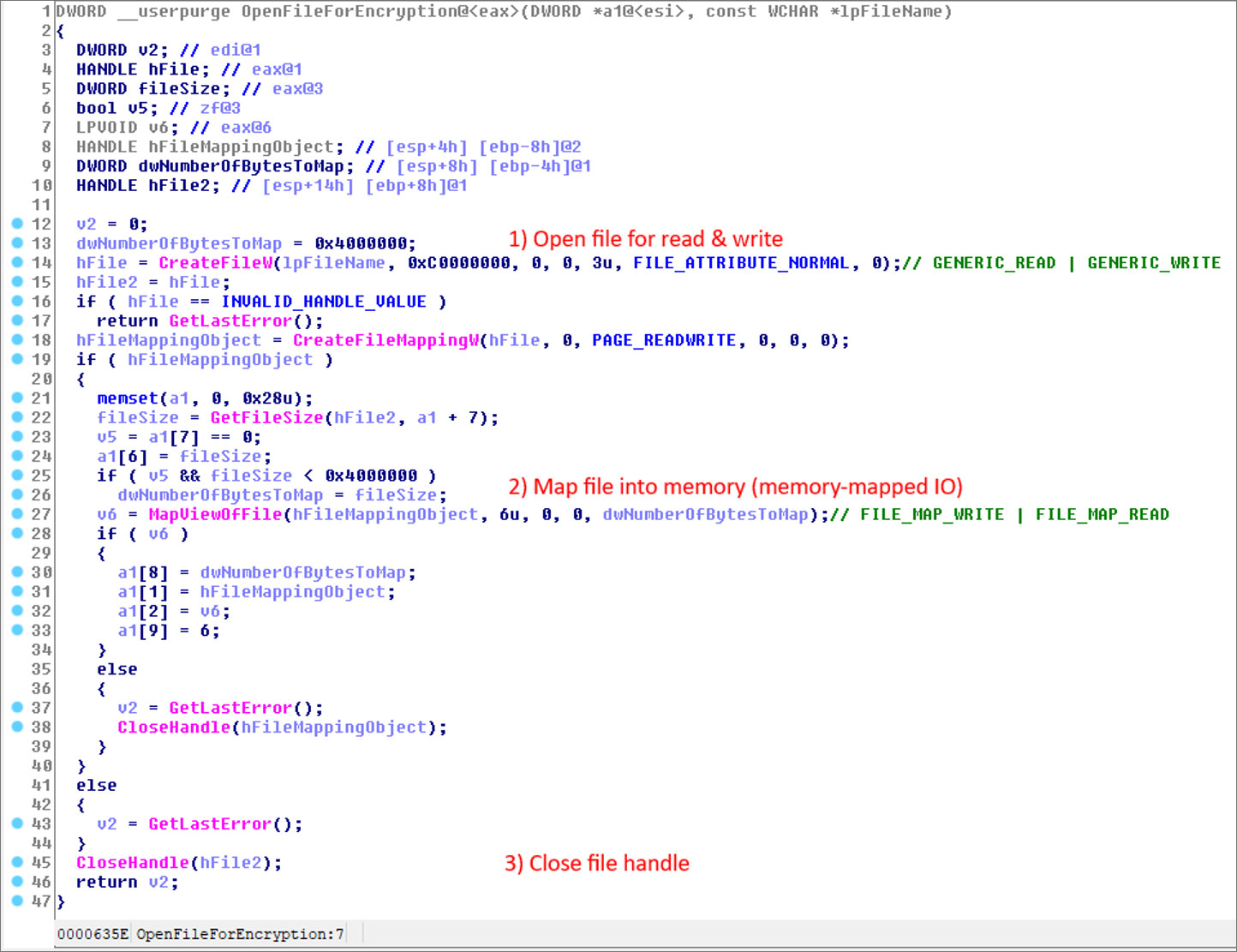
Source: Sophos
As the data is now stored in the Windows Cache Manager, WastedLocker will then encrypt the file’s contents stored in the cache, rather than the file stored on the file system.
When the contents of a file stored in the Windows cache are modified, they become ‘dirty.’ When enough data become dirty, the Windows Cache Manager will write the encrypted cached data back to their original files.
As the Windows Cache Manager is running as a System process, security software will see the writing of the encrypted data from an allowed and legitimate Windows process, as shown below.
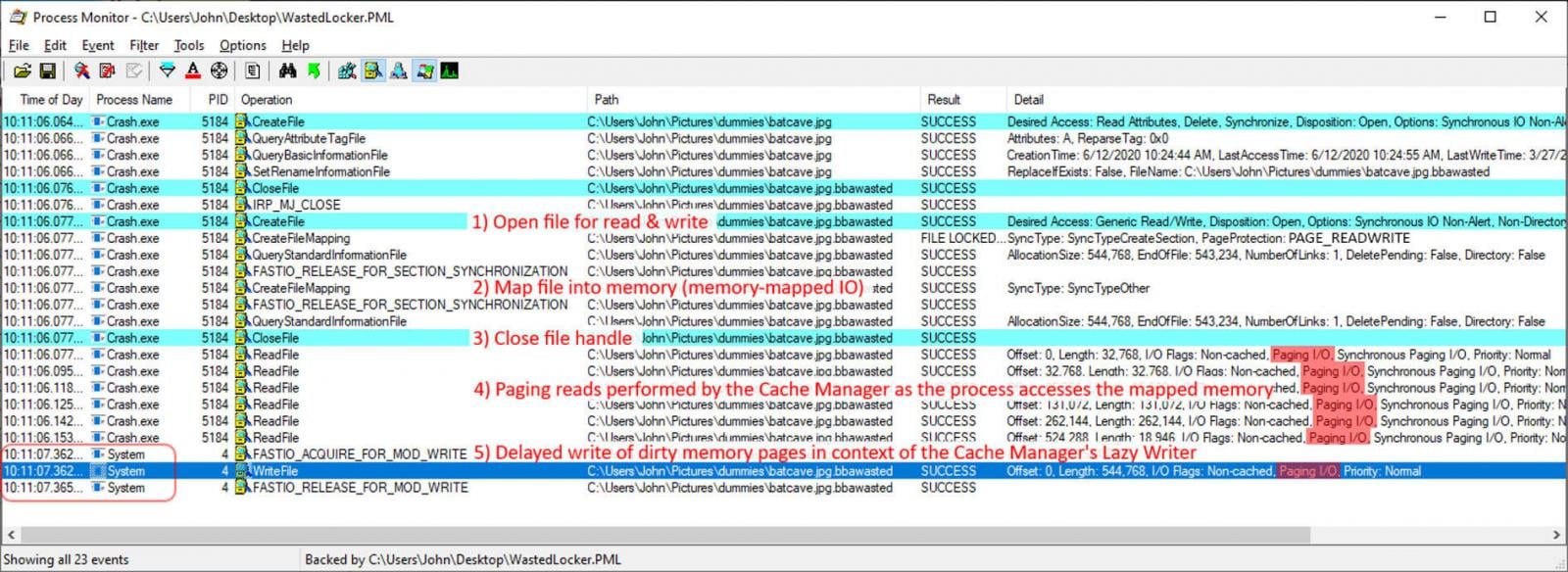
Source: Sophos
Due to this, behavioral detections in anti-ransomware software will see an allowed process writing the encrypted data and not detect that anything is wrong.
This method effectively bypasses a security solution’s ransomware protection modules and allows WastedLocker to encrypt all the files.
Mark Loman, Director of Engineering at Sophos, told BleepingComputer that their CryptoGuard protection engine has been updated to detect this evasion and code updates have been rolled out to users of HitmanPro.Alert.
Customers protected by Intercept X will receive this update as well at a later time, and are immediately protected by the detection of the code packer the malware uses, its use of Alternate Data Streams, and the detection of distribution methods
With its use of advanced techniques such as the Windows Cache Manager, alternate data streams, UAC bypasses, and the hashing of function names, WastedLocker is a ransomware threat that all organizations should be aware and concerned about.
To read the original article: https://www.bleepingcomputer.com/news/security/wastedlocker-ransomware-abuses-windows-feature-to-evade-detection/



