A versatile banking trojan targeting users in Latin America has been circulating in multiple countries including Mexico, Brazil, Chile, Spain, Peru, and Portugal.
The malware ensures persistence on infected systems and has advanced capabilities such as planting backdoors, stealing bitcoins, and exfiltrating credentials.
Dubbed Mekotio, the trojan collects sensitive information from victim hosts, such as firewall configuration, operating system information, if admin privileges are enabled, and the status of any antivirus products installed.
False site update popups
One behavior specific to Mekotio is uising system popups that impersonate system updates.
The Windows popup shown below contains a false message in Portuguese advising the user, “We are currently performing security updates on the site! Please try again later!”
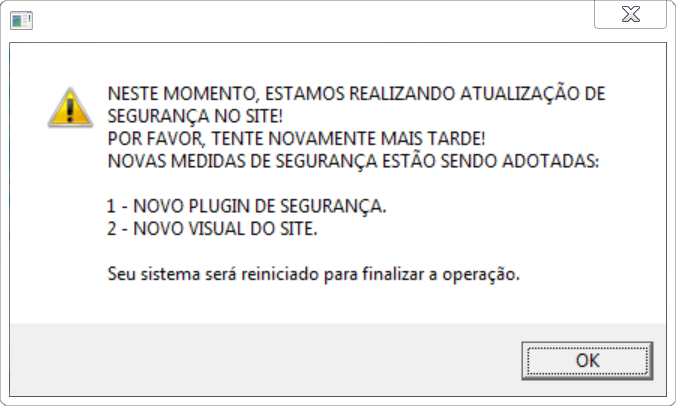
Source: ESET
“Mekotio has several typical backdoor capabilities. It can take screenshots, manipulate windows, simulate mouse and keyboard actions, restart the machine, restrict access to various banking websites and update itself,” explains a report released by ESET this week.
Some variants of the trojan can also hijack cryptocurrency by replacing a Bitcoin wallet address in the clipboard and getting saved passwords from Chrome web browser.
Trojan distributed via phishing
ESET’s researches have stated that phishing spam seems to be the primary manner of distribution leveraged by the creators of Mekotio.
The email pretends to contain a receipt but has links that download an malicious ZIP file associated with this malware.
The trojan has been known to circulate since at least 2015. Since 2018, researchers have observed 38 different distribution chains used by Mekotio and similar strands.
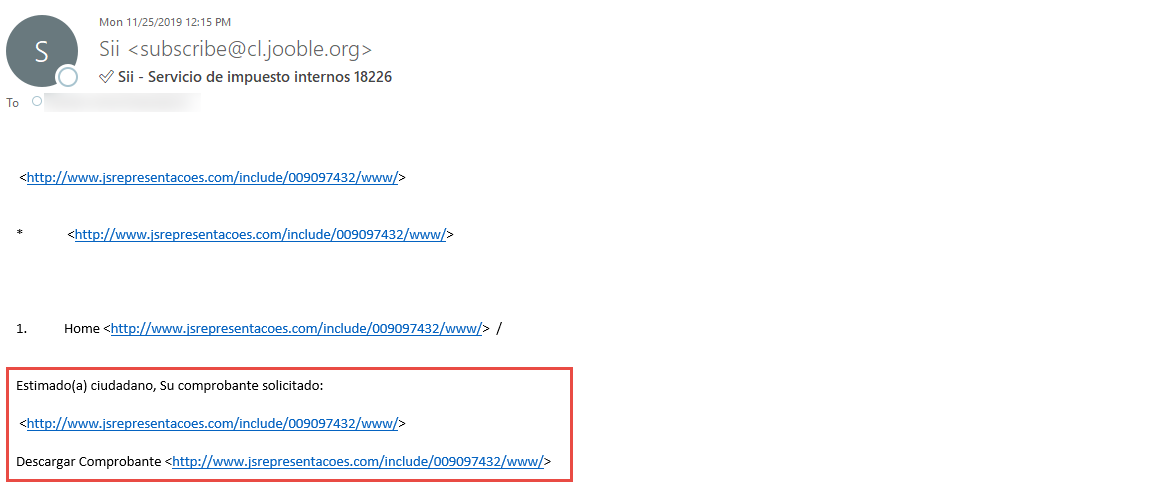
Source: ESET
Attack mechanics
In one of the attack scenarios, the malware “passes context” between different processes to evade detection and analyses.
Initially, a simple BAT dropper initiates a VBScript downloader with parameters containing an HTTP verb and the URL to another downloader.
This intermediate downloader calls yet another URL to obtain and execute a PowerShell script which further fetches the downloader with the malicious payload.
It is worth noting that a custom “User-Agent” HTTP header and method (HTTP verb) is used by these downloaders to fetch next stage downloaders.
This is a clever tactic as someone accessing the URL directly, e.g. from a web browser, would be sending very different “User-Agent” headers and likely be using the default “GET” method, as opposed to the custom “111SA” HTTP verb expected by the C&C server.
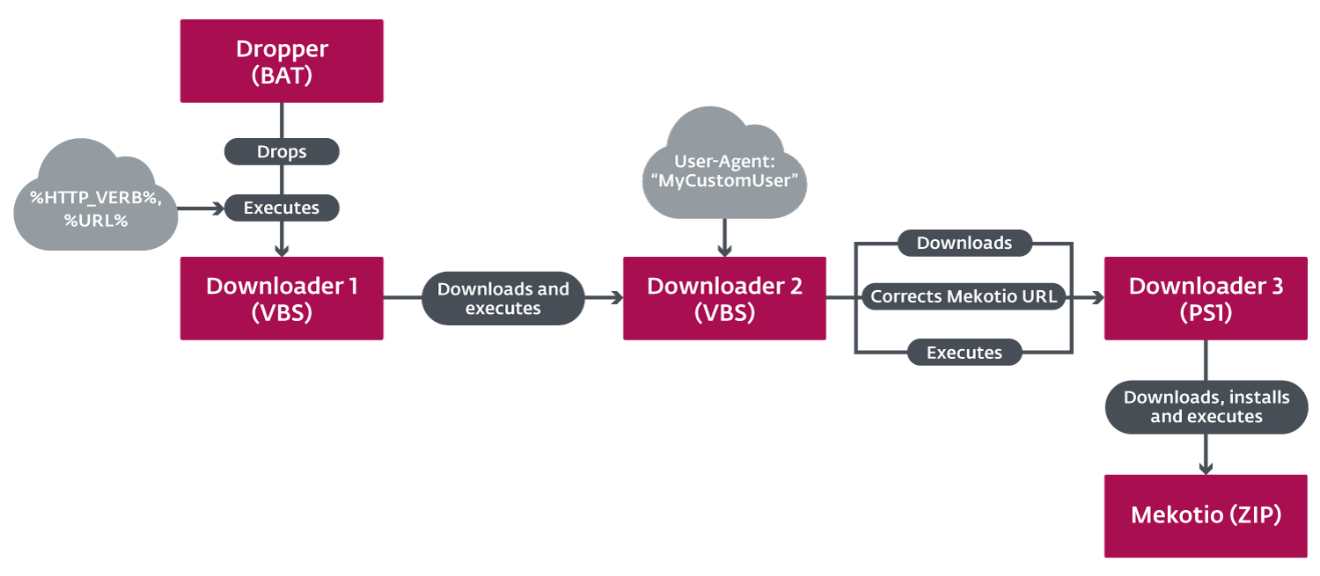
This constant passing of context between processes helps the trojan mask its footsteps. For example, even if one of the Indicators of Compromise (IoCs) was to be caught at the very initial stages by an antivirus product, the remaining URLs and downloaders would stay hidden from the eyes of researchers and detection tools.
Another scenario Mekotio uses is to conceal JavaScript in an MSI package.
“In this case, the chain is much shorter and less robust, as only a single JavaScript, serving as the final stage, is embedded in the MSI and executed,” the report explains.
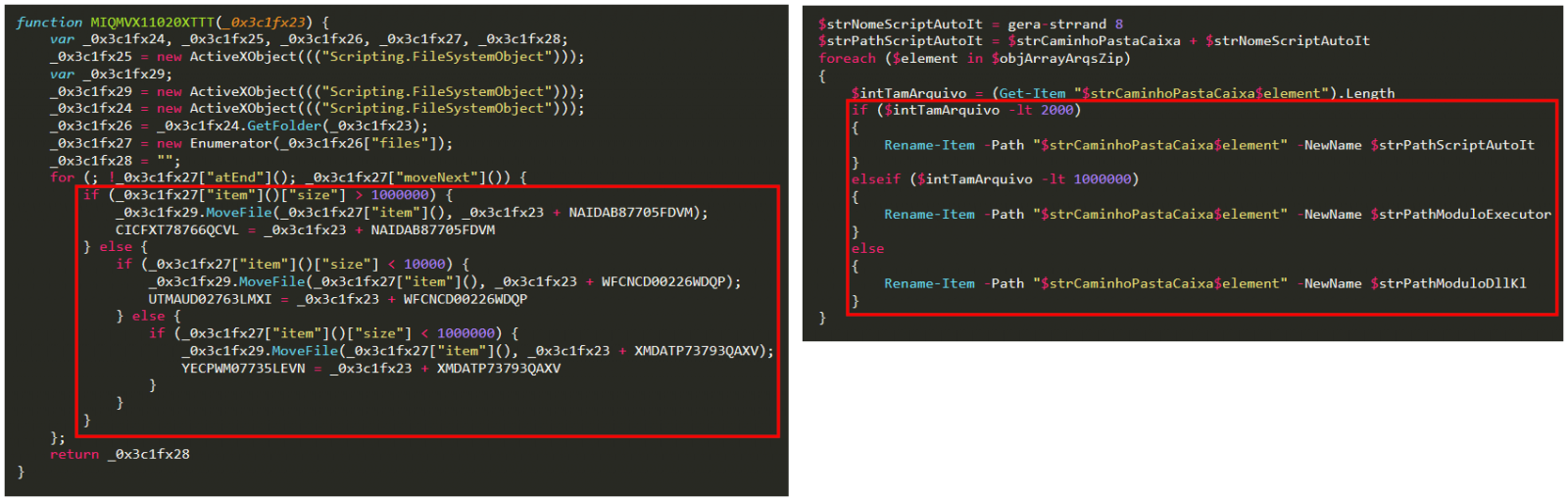
Source: ESET
Mekotio binaries use the same cryptographic algorithm as the Casbaneiro family does when encrypting strings. In Mekotio’s case, however, variation lies in the manner in which data is modified before its decryption.
The researchers stated that “the first few bytes of the hardcoded decryption key may be ignored, as may some bytes of the encrypted string. Some variants further encode encrypted strings with base64.”
The trojan’s very many use cases also extend to include fiddling of registry values.
By disabling various registry values such as “HKCU\Software\Microsoft\windows\CurrentVersion\Explorer\AutoComplete\” the trojan turns off the “autocomplete” feature in web browsers, thereby forcing victims to retype their passwords, which the trojan would then intercept.
C&C Server has cryptic SQL DB references
The command-and-control (C&C) servers used by Mekotio are either based on the open-source Delphi Remote Access PC project or uses an SQL database storing C&C commands.
To conceal the details of the SQL schema, Mekotio does not have outright SQL query strings hardcoded (e.g. “SELECT * FROM table WHERE…”). Instead, it simply calls specific SQL procedures stored on the server-side.
Furthermore, the means of establishing a connection to the SQL DB is cryptic.
Instead of having specific domains and IP addresses hardcoded in the binaries, Mekotio relies on two lists: one with “fake domains” and another with port numbers.
A mysterious algorithm then runs arithmetic operations to dynamically generate the real C&C domain addresses.
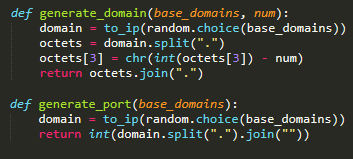
Source: ESET
“A random domain is chosen from both lists and resolved. The IP address is further modified. When generating the C&C domain, a hardcoded number is subtracted from the last octet of the resolved IP address. When generating the C&C port, the octets are joined together and treated like a number,” explain ESET’s researchers.
This makes it more difficult to identify the malicious domains during static analysis.
Different approaches built into the trojan also generate domains based on complex algorithms. For example, generating an MD5 hash of the local time, victim’s timezone, current date, etc.
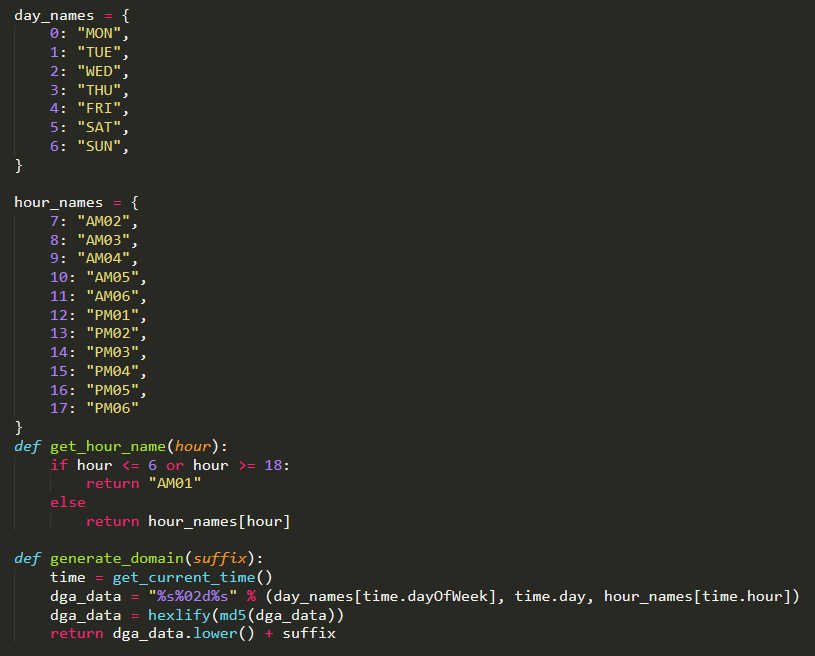
ESET’s researchers suspect there are multiple variants of Mekotio being developed concurrently. They have described this malware’s development lifecycle “rather chaotic,” much like other Latin American banking trojans.
A persistent banking trojan this complex with a large number of variants poses greater challenges for security professionals and opens up more possibilities for its next iteration.
Detailed analysis of Mekotio, along with the complete list of IoCs it uses have been identified and provided in ESET’s report.
To read the original article: https://www.bleepingcomputer.com/news/security/mekotio-banking-trojan-imitates-update-alerts-to-steal-bitcoin/



