The National Security Agency is warning about espionage operations from the Russian Intelligence Directorate (GRU) using a previously undisclosed Linux malware toolset called Drovorub.
The malicious framework has various modules that ensure stealthiness, persistence, and complete access to the compromised machine with the highest privileges.
The NSA today released a technical report (a joint effort with the FBI) detailing Drovorub’s capabilities and offering detection and prevention solutions. The agency says that the framework includes a kernel module rootkit that makes it difficult for network-wide security solutions to catch it.
“Drovorub is a Linux malware toolset consisting of an implant [client] coupled with a kernel module rootkit, a file transfer and port forwarding tool, and a Command and Control (C2) server” – National Security Agency
The client side of the malware can communicate directly with the threat actor’s C2 infrastructure, has file upload/download capabilities, executes arbitrary commands with ‘root’ privileges, and can forward network traffic to other machines on the network.
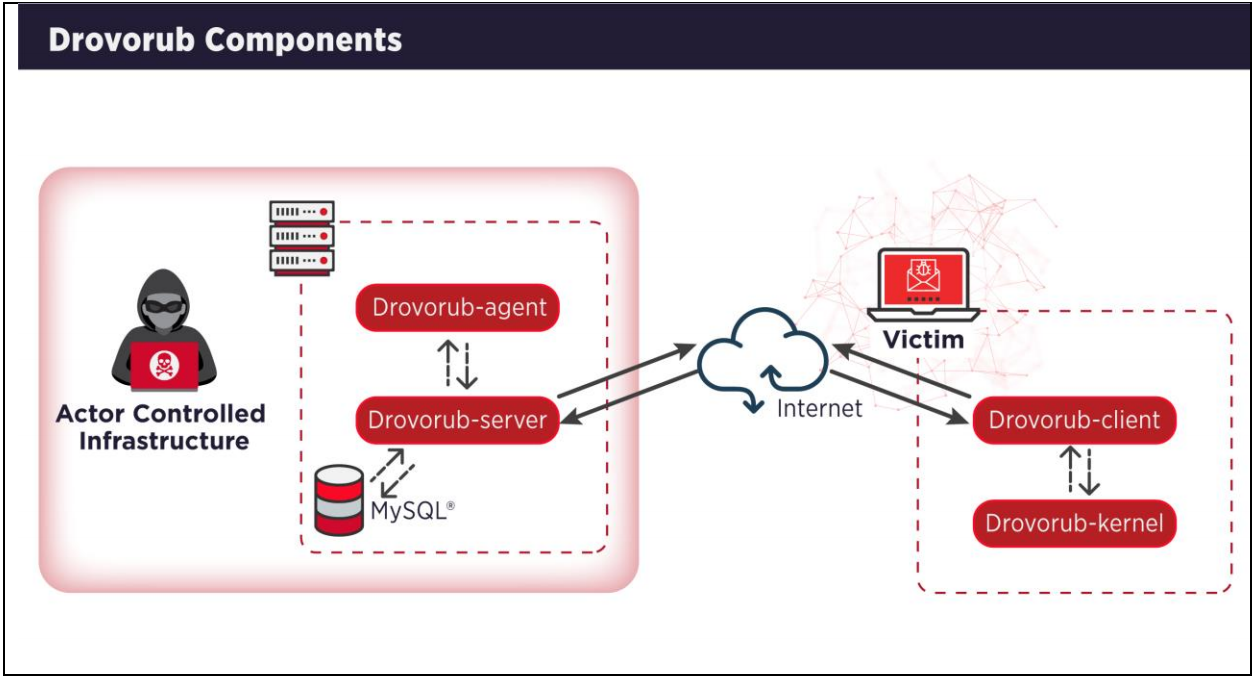
According to the report, the rootkit is highly successful at hiding on an infected machine and survives reboots “unless UEFI [Unified Extensible Firmware Interface] secure boot is enabled in ”Full“ or ”Thorough“ mode.”
NSA’s report describes the technical details for each Drovorub part, which communicate with each other via JSON over WebSockets and encrypt the traffic to and from the server module using the RSA algorithm.
Russian ‘woodcutter’
Both the NSA and the FBI attribute the malware to the Russian General Staff Main Intelligence Directorate 85th Main Special Service Center (GTsSS), military unit 26165.
Cyber activity from this organization is linked to campaigns from the advanced hacking collective known as Fancy Bear (APT28, Strontium, Group 74, PawnStorm, Sednit, Sofacy, Iron Twilight).
This attribution is based on operational command and control infrastructure that has been publicly associated with the GTsSS by companies defending against cyber attacks.
One clue is an IP address Microsoft found in a Strontium campaign exploiting IoT devices in April 2019 that was also used to access a Drovorub C2 during the same time.
The name of the malware means ‘woodcutter’ in Russian and the NSA says that it is how GTsSS refers to the toolset. It is coined from the words Drovo and and Rub, which translate from Russian to “wood/firewood” and “to chop/fell, respectively.
A complete technical analysis for each Drovorub component is available in NSA’s report, along with methods to prevent and detect the attack.
Researchers should take note that the IP addresses, ports, cryptographic keys, files and their paths are not from live operations but the result of the agency’s lab analysis.
Detection and prevention
NSA’s research determined that the malware activity is visible to complementary detection techniques but these are not too effective for the Drovorub kernel module.
Network Intrusion Detection Systems (NIDS) like Suricata, Snort, Zeek can can dynamically de-obfuscate “masked” WebSocket protocol messages (via scripting) and identify C2 messages between Drovorub client, agent, and server components.
A TLS proxy would achieve the same result even if the communication channel uses the TLS protocol for encryption.
A caveat for these methods though, is that the traffic exchange can slip under the radar if TLS is used or the actor switches to a different message format.
For host-based detection, the NSA provides the following solutions:
- Probing the presence of the Drovorub kernel module via a script (included in the report on page 35)
- Security products that may detect malware artifacts and the rootkit functionality, as can the Linux Kernel Auditing System
- Live response techniques – searching for specific filenames, paths, hashes, and with Yara rules (provided in the report along with Snort rules)
- Memory analysis – the most effective method to find the rootkit
- Disk image analysis – malware artifacts are persistent on disk but hidden from regular system binaries and calls by the rootkit
As prevention methods, the NSA recommends installing the latest Linux updates and run the latest software versions available.
Furthermore, system administrators should make sure that machines are running at least Linux Kernel 3.7, which offers kernel signing enforcement.
Setting up systems to load only modules that have a valid digital signature increases the difficulty level for planting malicious kernel modules.
Another recommendation is to enable the UEFI Secure Boot verification mechanism (Thorough or Full enforcement) which allows only legitimate kernel modules to load. However, this does not protect against the recently disclosed BootHole vulnerability until a permanent DBX update emerges.
To read the original article: https://www.bleepingcomputer.com/news/security/nsa-discloses-new-russian-made-drovorub-malware-targeting-linux/



