North Korean hackers tracked as BeagleBoyz have been using malicious remote access tools as part of ongoing attacks to steal millions from international banks according to a joint advisory issued today by several U.S. Government agencies.
The joint release says that North Korea’s BeagleBoyz hacking group has once again started robbing banks through remote internet access since February 2020 to fund the North Korean regime.
BeatleBoys are currently targeting banks in more than 30 countries in an ongoing bank robbery scheme, attempting to steal $2 billion, as U.S. Cyber Command tweeted.
The information shared today by the U.S. Government is the result of information gathered and investigated by analysts at the Cybersecurity and Infrastructure Security Agency (CISA), the Department of the Treasury (Treasury), the Federal Bureau of Investigation (FBI), and U.S. Cyber Command (USCYBERCOM).
“Since February 2020, North Korea has resumed targeting banks in multiple countries to initiate fraudulent international money transfers and ATM cash outs. The recent resurgence follows a lull in bank targeting since late 2019,” the advisory says.
According to the advisory, in a single attack, BeagleBoyz’s ATM cash out schemes allowed them to withdrawn cash from ATM machines operated by banks from dozens of countries, including the United States.
BeagleBoyz also target victim international banks in SWIFT fraud schemes using the systems of unwitting banks, for instance stealing $81 million from the Bank of Bangladesh during 2016.
Luckily, the Federal Reserve Bank of New York was able to stop the remainder of an attempted $1 billion transfer after identifying anomalies in the transfer instructions received from the Bank of Bangladesh.
North Korea’s BeagleBoyz are responsible for the sophisticated cyber-enabled ATM cash-out campaigns identified publicly as “FASTCash” in October 2018. Since 2016, the BeagleBoyz have perpetrated the FASTCash scheme, targeting banks’ retail payment system infrastructure (i.e., switch application servers processing International Standards Organization [ISO] 8583 messages, which is the standard for financial transaction messaging).
BeagleBoyz are part of the North Korean government’s Reconnaissance General Bureau and they have been active since at least 2014, stealing hundreds of millions from banks to fund the country’s regime.
The BeagleBoyz activity overlaps with other groups tracked by cybersecurity firms including APT38 (FireEye), Bluenoroff (Kaspersky), Lazarus Group (ESTSecurity), and Stardust Chollima (CrowdStrike).
They are also known to be behind FASTCash ATM cash outs reported during October 2018, the abuse of compromised bank-operated SWIFT system endpoints since 2015, as well as thefts from cryptocurrency firms.
Since CISA’s initial alert on North Korea’s FASTCash campaigns, the BeagleBoyz has moved to target regional interbank payment processors with FASTCash malware besides individual banks, showing a clear goal of exploring other “upstream opportunities in the payments ecosystem.”
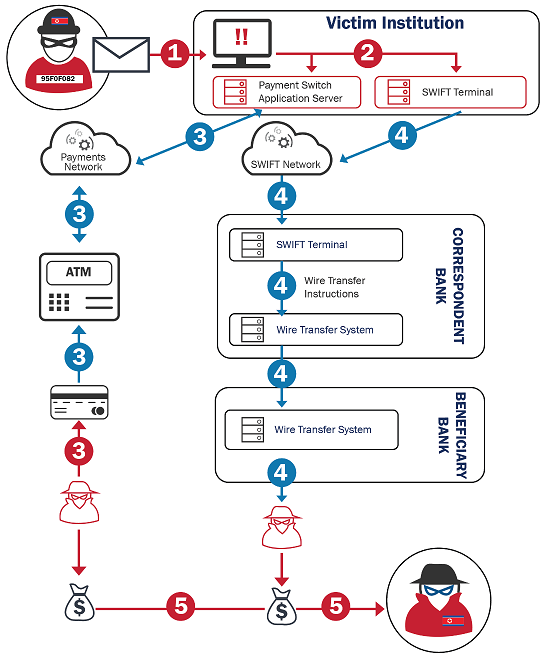
“The BeagleBoyz use a variety of tools and techniques to gain access to a financial institution’s network, learn the topology to discover key systems, and monetize their access. The technical analysis below represents an amalgamation of multiple known incidents, rather than details of a single operation,” the agencies said.
The North Koreans were observed while using a wide range of techniques to gain access to their victims’ systems including spearphishing and watering holes, as well as social engineering in job-application themed phishing attacks starting with 2018 up to early 2020.
They may have also hired the services of criminal hacking groups, like TA505, for initial access into targeted financial institutions, launching the final attack against the victim banks’ systems months later in some cases.
“In addition to robbing traditional financial institutions, the BeagleBoyz target cryptocurrency exchanges to steal large amounts of cryptocurrency, sometimes valued at hundreds of millions of dollars per incident,” the advisory says.
“Cryptocurrency offers the BeagleBoyz an irreversible method of theft that can be converted into fiat currency because the permanent nature of cryptocurrency transfers do not allow for claw-back mechanisms.”
Besides the joint technical alert, U.S. Cyber Command also released three Malware Analysis Reports (MARs) on the North Korean government’s ATM cash-out scheme with information on ECCENTRICBANDWAGON, VIVACIOUSGIFT, and FASTCASH for Windows malware.
The U.S. Treasury sanctioned three DPRK-sponsored hacking groups (Lazarus, Bluenoroff, and Andariel) in September 2019.
More information about HIDDEN COBRA activity in the form of previous alerts is available via the U.S. National Cyber Awareness System.
To read the original article:



