Threat researchers discovered a new malware family that is fully focused on getting as much cryptocurrency as possible from its victims. For this purpose, it steals wallets, hijacks transactions, and starts mining on infected machines.
Named KryptoCibule, the malware has managed to stay under the radar for almost two years, extending its functionality with each new version.
Dodging antivirus solutions
In a technical analysis released today, researchers at ESET note that KryptoCibule relies heavily on the Tor network to communicate with its command and control (C2) servers.
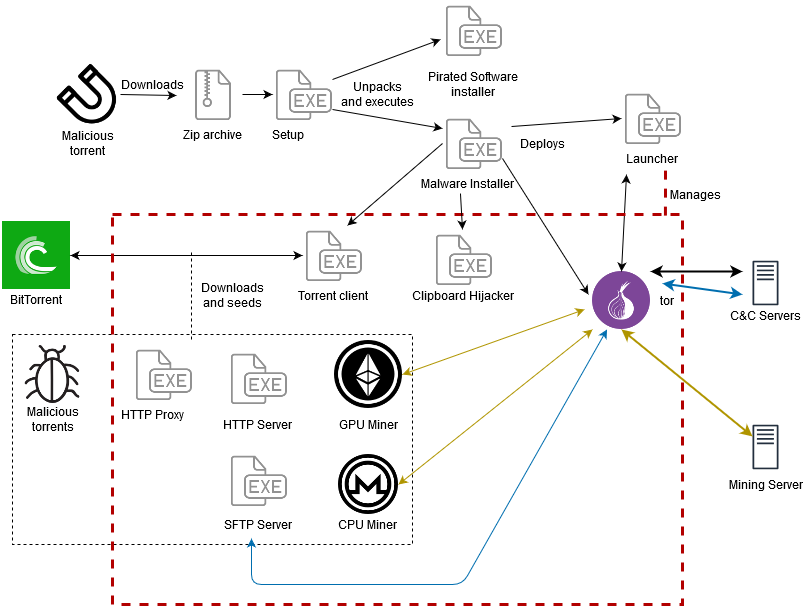
It spreads via malicious torrents in archives pretending to installers for pirated versions of popular software and games. When launching the executable, malware installation starts in the background and the expected routine for the cracked product runs in the foreground.
This drill, along with the fact that it seems to target users in the Czech Republic and Slovakia (more than 85% of ESET’s detections are from these countries), allowed the malware to avoid attention for so long.
Attacking these regions is likely intentional, as researchers discovered that the anti-analysis and detection mechanisms in KryptoCibule specifically check for ESET, Avast, and AVG (subsidiary of Avast) security products, which are based in these two countries.
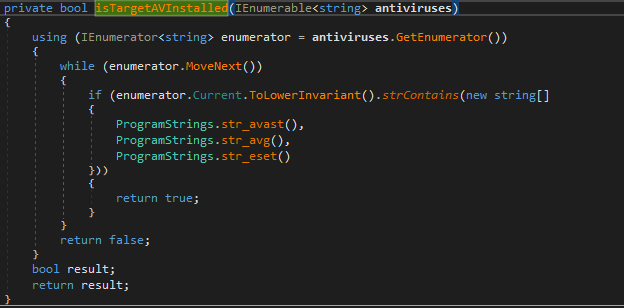
If any of the strings in the image above are detected, the malware takes a raincheck on installing the cryptominer components.
This detail contributed to naming the malware KryptoCibule, which is a mix of the Czech and Slovak words for “crypto“ and “onion.”
Evasion tactics do not stop at this, though. Executing the payload happens only if processes for specific analysis software are missing on the computer. The researchers provide the following list:•
•cain, •filemon, •netmon, •netstat, •nmwifi, •perfmon, •processhacker, •procexp, •procexp64, •procmon, •regmon, •tasklist, •taskmgr, •tcpvcon, •tcpview, •wiresharkStealthy coin mining
Typically, cryptocurrency-related malware goes after the wallets or hijacks transactions but KryptoCibule is a triple threat as it also deploys miners that use both CPU and GPU resources for Monero and Ethereum.
Mining for cryptocurrency is a resource intensive operation likely to draw attention. In this case, though, the process runs unrestricted only if there was no user input for the last three minutes and the computer’s battery level is above 30%.
If these conditions are not met, the Ethereum miner is suspended and the one for Monero uses only one thread. All mining stops when battery level is below 10%.
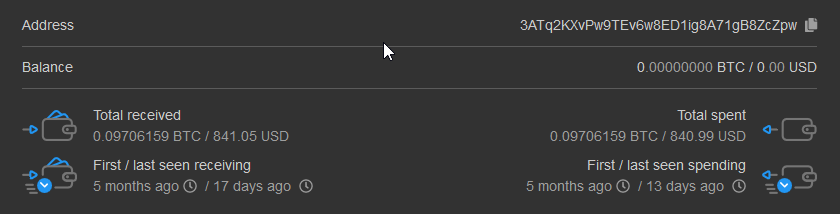
It is unclear how much money KryptoCibule operators made from these processes but researchers found that some wallets used by the transaction hijacking component received a measly $1,800 in Bitcoin and Ethereum. This amount is likely not reflecting the author’s earnings from the malware as it is too small “to justify the development effort observed.”
A third component related to cryptocurrency searches the filesystem for entries with names specific to wallets, miners, and digital coins, as well as “password” and “bank,” or other type of sensitive files (.SSH, .AWS).
Apart from its focus on cryptocurrency, the threat features other tools that give its operators remote access to the compromised host. The attackers can spawn a backdoor using Pupy post-exploitation tool.
To add other tools on an infected computer, the malware installs the Transmission BitTorrent client, which receives remote commands via the RPC interface on the default port. Access to the interface is restricted and the credentials (superman:krypton) are hardcoded.
“To install further software for the malware’s use, such as the SFTP server, the Launcher component makes an HTTP GET request to ‘%C&C%/softwareinfo?title=’ and receives a JSON response containing a magnet URI1 for the torrent to download and other information indicating how to install and execute the program” – ESET
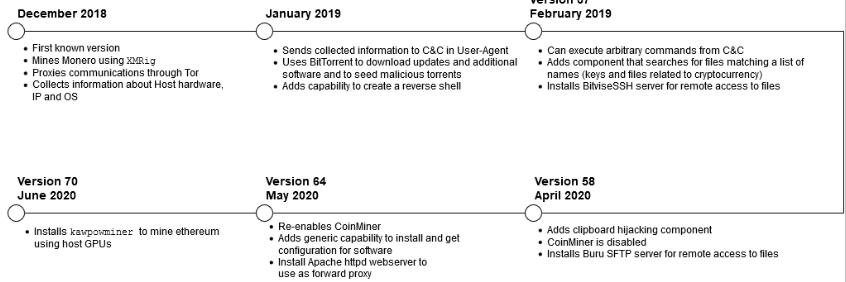
All this functionality is the result of close to two years of development as the researchers were able to track the malware to December 2018. In the image below, they show how KryptoCibule evolved to what it is today.
To read the original article:



